Data Breach

With cyber threats intensifying and data breaches rising, understanding how to respond to incidents is more important than ever. In this interview, Michael Bruemmer,...
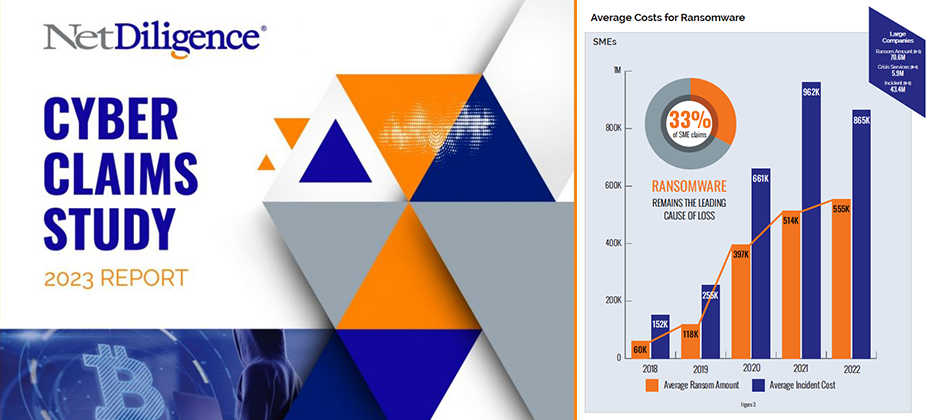
Review of Findings & Front-line Insights Panel Participants: About NetDiligence Cyber Claims Study It is NetDiligence’s 13th year of doing this Cyber Claims Study....

Insights from the Cyber Risk Summit Beverly Hills – October 2023 Authored by Ryan Coyne I recently participated in a panel with industry experts,...
In the fast-paced world of cybersecurity, the ability to anticipate and adapt to emerging threats is not just a competitive advantage—it’s a business imperative....

The threat of data breach is constant in our modern, digital world. And as technology advances, so do the strategies and tactics of malicious...

2023-2024 Experian Data Breach Response Guide Learn how you can boost your preparedness against cyberattacks—downloadthe new guide now. As the proliferation of connected devices...

Reflections, New Predictions, and What to Expect by 2033. Where We’ve Been: A Cybersecurity Recap It’s been a decade since Experian released its first...

When a data breach occurs, it can have a ripple effect on your business, your employees, and your customers. Depending on the severity of...

The Threat “With criminals, there’s no such thing as a border anymore. They don’t care where you are, who you are; if there’s money...

As we navigate a new way of living, working, and handling the unpredictability of COVID-19 and other potential health concerns worldwide, now is not...

Crises come in many forms, without warning, and can be devastating for any size business. A company’s ability to manage crises, specifically with a...

What if there was a way to assess your data security readiness before a breach happens? Imagine the worst thing that could happen to...

Data breaches are becoming more common, and you need to be aware of the risks to effectively protect your business. A breach of consumer...

Experian has been a sponsor of theAnnual Ponemon Data Breach Preparedness Studyfor nine years. During this time, I’ve seen companies change their operations to...

New Year, New Cyber Threats This is my first blog post of 2022, and I’m afraid the news I’m here to bear isn’t ideal:...