Financial Services

Opening a new consumer checking account in the 21st century should be simple and easy to understand as a customer right? Unfortunately, not all banks have 21st century systems or processes reflecting the fact that negotiable order of withdrawal (NOW) accounts, or checking accounts, were introduced decades ago within financial institutions and often required the consumer to be in person to open the account. A lot has changed and consumers demand simpler and transparent account opening processes with product choices that match their needs at a price that they’re willing to pay. Financial institutions that leverage modernized technology capabilities and relevant decision information have the best chance to deliver consumer friendly experiences that meet consumer expectations. It is obvious to consumers when we in the financial services industry get it right and when we don’t. The process to open a checking account should be easily understood by consumers and provide them with appropriate product choices that aren’t “one size fits all”. Banks with more advanced core-banking systems incorporating relevant and compliant decision data and transparent consumer friendly approval processes have a huge opportunity to differentiate themselves positively from competitors. The reality is that banking deposit management organizations throughout the United States continue to evolve check screening strategies, technology and processes. This is done in an effort to keep up with evolving regulatory expectations from the consumer advocacy regulatory bodies such as the Consumer Financial Protection Bureau (CFPB) and designed to improve transparency of checking account screening for new accounts for an increased number of consumers. The CFPB advocates that financial institutions adopt new checking account decision processes and procedures that maintain sound management practices related to mitigating fraud and risk expense while improving consumer transparency and increasing access to basic consumer financial instruments. Bank shareholders demand that these accounts be extended to consumers profitably. The CFPB recognizes that checking accounts are a basic financial product used by almost all consumers, but has expressed concerns that the checking account screening processes may prevent access to some consumers and may be too opaque with respect to the reasons why the consumer may be denied an account. The gap between the expectations of the CFPB, shareholders and bank deposit management organization’s current products and procedures are not as wide as they may seem. The solution to closing the gap includes deploying a more holistic approach to checking account screening processes utilizing 21st century technology and decision capabilities. Core banking technology and checking products developed decades ago leave banks struggling to enact much needed improvements for consumers. The CFPB recognizes that many financial institutions rely on reports used for checking account screening that are provided by specialty consumer reporting agencies (CRAs) to decision approval for new customers. CRAs specialize in checking account screening and provide financial institutions with consumer information that is helpful in determining if a consumer should be approved or not. Information such as the consumer’s check writing and account history such as closed accounts or bounced checks are important factors in determining eligibility for the new account. Financial institutions are also allowed to screen consumers to assess if they may be a credit risk when deciding whether to open a consumer checking account because many consumers opt-in for overdraft functionality attached to the checking account. Richard Cordray, the CFPB Director, clarified the regulatory agency’s position as to how consumers are treated in checking account screening processes within his prepared remarks at a forum on this topic in October 2014. “The Consumer Bureau has three areas of concern. First, we are concerned about the information accuracy of these reports. Second, we are concerned about people’s ability to access these reports and dispute any incorrect information they may find. Third, we are concerned about the ways in which these reports are being used.” The CFPB suggests four items they believe will improve financial institution’s checking account screening policies and practices: Increase the accuracy of data used from CRA’s Identify how institutions can incorporate risk screening tools while not excluding potential accountholders unnecessarily Ensure consumers are aware and notified of information used to decision the account opening process Ensure consumers are informed of what account options exist and how they access products that align with their individual needs Implementing these steps shouldn’t be too difficult to accomplish for deposit management organizations as long as they are fully leveraging software such as Experian’s PowerCurve customized for deposit account origination, relevant decision information such as Experian’s Precise ID Platform and Vantage Score® credit score combined with consumer product offerings developed within the bank and offered in an environment that is real-time where possible and considers the consumer’s needs. Enhancing checking account screening procedures by taking into account consumer’s life-stage, affordability considerations, unique risk profile and financial needs will satisfy expectations of the consumers, regulators and the financial institution shareholders. Financial institutions that use technology and data wisely can reduce expenses for their organizations by efficiently managing fraud, risk and operating costs within the checking account screening process while also delighting consumers. Regulatory agencies are often delighted when consumers are happy. Shareholders are delighted when regulators and consumers are happy. Reengineering checking account opening processes for the modern age results in a win-win-win for consumers, regulators and financial institutions. Discover how an Experian Global Consultant can help you with your banking deposit management needs.
Originally contributed by: Bill Britto Smart meters have made possible new services for customers, such as automated budget assistance and bill management tools, energy use notifications, and "smart pricing" and demand response programs. It is estimated that more than 50 million smart meters have been deployed as of July 2014. Utilities and customers alike are benefiting from these smart meter deployments. It is now obvious the world of utilities is changing, and companies are beginning to cater more to their customers by offering them tools to keep their energy costs lower. For example, several companies offer prepay to some of their customers who do not have bank accounts. For many of those "unbanked" customers, prepay could be the only way to sign up for a utility services. Understanding the value of prospects and the need to automate decisions to achieve higher revenue and curb losses is imperative to the utility. It is here where a decisioning solution, like PowerCurve OnDemand> can make a real difference for utility customers by providing modified decision strategies based on market dynamics, business and economic environments. Imagine what a best of class decision solution can do by identifying what matters most about consumers and business and by leveraging internal and external data assets to replace complexity with cost efficiency? Solutions like PowerCurve OnDemand deliver the power and speed-to-market to respond to changing customer demands, driving profitability and growing customer lifetime value - good for business and good for customers.

A new comarketing agreement for MainStreet Technologies’ (MST) Loan Loss Analyzer product with Experian Decision Analytics’ Baker Hill Advisor® product will provide the banking industry with a comprehensive, automated loan-management offering. The combined products provide banks greater confidence for loan management and loan-pricing calculations. Experian Decision Analytics Baker Hill Advisor product supports banks’ commercial and small-business loan operations comprehensively, from procuring new loans through collections. MST’s Loan Loss Analyzer streamlines the estimation and documentation of the Allowance for Loan and Lease Losses (ALLL), the bank’s most critical quarterly calculation. The MST product automates the most acute processes required of community bankers in managing their commercial and small-business loan portfolios. Both systems are data-driven, configurable and designed to accommodate existing bank processes. The products already effectively work together for community banks of varying asset sizes, adding efficiencies and accuracy while addressing today’s increasingly complex regulatory requirements. “Experian’s Baker Hill Advisor product-development priorities have always been driven by our user community. Changes in regulatory and accounting requirements have our clients looking for a sophisticated ALLL system. Working with MainStreet, we can refer our clients to an industry-leading ALLL platform,” said John Watts, Experian Decision Analytics director of product management. “The sharing of data between our organizations creates an environment where strategic ALLL calculations are more robust and tactical lending decisions can be made with more confidence. It provides clients a complete service at every point within the organization.” “Bankers, including many using our Loan Loss Analyzer, have used Experian’s Baker Hill® software to manage their commercial loan programs for more than three decades,” said Dalton T. Sirmans, CEO and MST president. “Bankers who choose to implement Experian’s Baker Hill Advisor and the MST Loan Loss Analyzer will be automating their loan management, tracking, reporting and documentation in the most comprehensive, user-friendly and feature-rich manner available.” For more information on MainStreet Technologies, please visit http://www.mainstreet-tech.com/banking For more information on Baker Hill, visit http://ex.pn/BakerHill

By: John Robertson I began this blog series asking the question “How can banks offer such low rates?” Exploring the relationship of pricing in an environment where we have a normalized. I outlined a simplistic view of loan pricing as: + Interest Income + Non-Interest Income Cost of Funds Non-Interest Expense Risk Expense = Income before Tax Along those lines, I outlined how perplexing it is to think at some of these current levels, banks could possibly make any money. I suggested these offerings must be lost leaders with the anticipation of more business in the future or possibly, additional deposits to maintain a hold on the relationship over time. Or, I shudder to think, banks could be short funding the loans with the excess cash on their balance sheets. I did stumble across another possibility while proving out an old theory which was very revealing. The old theory stated by a professor many years ago was “Margins will continue to narrow…. Forever”. We’ve certainly seen that in the consumer world. In pursuit of proof to this theory I went to the trusty UBPR and looked at the net interest margin results from 2011 until today for two peer groups (insured commercial banks from $300 million to $1 billion and insured commercial banks greater the $3 billion). What I found was, in fact, margins have narrowed anywhere from 10 to 20 basis points for those two groups during that span even though non-interest expense stayed relatively flat. Not wanting to stop there, I started looking at one of the biggest players individually and found an interesting difference in their C&I portfolio. Their non-interest expense number was comparable to the others as well as their cost of funds but the swing component was non-interest income. One line item on the UPBR’s income statement is Overhead (i.e. non-interest expense) minus non-interest income (NII). This bank had a strategic advantage when pricing there loans due to their fee income generation capabilities. They are not just looking at spread but contribution as well to ensure they meet their stated goals. So why do banks hesitate to ask for a fee if a customer wants a certain rate? Someone seems to have figured it out. Your thoughts?

By: Mike Horrocks A recent industry survey was published that called out the number one reason that lenders were dissatisfied or willing to go to another financial institution (and take their book of business with them) was not compensation. While, compensation is often thought of as the number one driver for this kind of change in your bench of lenders, it had much more to do with being able to serve customers efficiently. One of the key reasons that lenders were unhappy was that they were in a workflow and decisioning process where the lender could not close loans on time, putting stress on the loan officer's relationships and destroying borrower confidence. Thinking of my own experiences as a commercial lender, my interactions with the private bankers, branch managers, and lenders that served every kind of customer, I would absolutely have to agree with this study. Nothing is more disheartening then working on bringing in a client, and then having the process not give me a response in the time that my clients are expecting or that the completion is achieving. Automation in the process is the key. While lenders still will need to be engaged in the process and paying attention to the relationship, it can be significantly refocused to other parts of the business. This leads to benefits such as: Protecting the back office and the consistence of booking and servicing loans. Ensuring that the risk appetite is consistent for the institution for every deal. Growing a portfolio of loans that can and will adhere to sound portfolio management techniques. So how is your process supporting lenders? Are you automating to help in areas that give you a competitive advantage with robust credit scores, decision strategies or risk management solutions that are helping close deals quickly or are you requiring a process that is keeping them from bringing more customers (and profits) in the door? Henry Ford is credited to say, “Coming together is a beginning. Keeping together is progress. Working together is success.” Take a closer look at your lending process. Do you have the tools that help bring your lenders, your customers, and your organization together? If you don’t you may be losing some of your best talent for loan production at a time when you can least afford it.

Cherian Abraham, our mobile commerce and payments consultant, recently wrote about the future of mobile banking in regards to the Apple Pay news out this week. The below article originally appeared in American Banker and is an edited version of his blog post. Editor's note: A version of this post originally appeared on Drop Labs. Depending on who you ask, the launch of Apple Pay was either exciting or uninspiring. The truth is far more complicated — particularly in terms of how it will impact the dynamics of Apple's relationship with banks. I would venture that most of the financial institutions on stage at the launch of Apple Pay earlier this week have mixed feelings about their partnership. They have had to sacrifice a lot of the room for negotiation that banks have retained with other wallet players such as Google Wallet and Softcard (the company formerly known as Isis). If you are an Apple Pay launch partner, having your credential or token on Apple Pay does not mean that you get to extend that credential into your own mobile banking app or wallet. For example, Bank A, with its credentials stored on Apple Pay, cannot leverage those credentials so that its own mobile banking app can use them to enable direct payments. Banks will have to accept that their credentials will be indefinitely locked to Apple Pay till deletion. No bank wants its brand to be overshadowed by Apple, nor do banks want smartphone users to close their app and open up a different wallet to make a payment. But this was not up for debate with Apple, which wants to tightly control the payment experience. This should be a cause of concern for Apple Pay partner banks, for whom enabling payments outside of Apple Pay in iOS is now off the table. Banks' only hope of having an integrated payment experience is to focus on Android, which supports host card emulation technology. HCE uses software to emulate a contactless smart card and communicate with near-field communication readers. I would expect a lot of banks to revisit Android and HCE in upcoming months. That goes double for the institutions that were not chosen to partner with Apple, along with retailers who have not rejected contactless payments as a modality in stores. Given that Apple will reportedly collect fees from its partner banks when customers execute transactions on the mobile wallet, all banks should be thinking about ways that they can make their presence on other Apple offerings more lucrative. If I were them, I would begin segmenting customers who hold one of iTunes' 500 million active accounts to see which ones are affluent spenders and which cards have higher interest rates, then implement targeted customer incentive strategies to move Apple users to higher-rate cards. I would use the same tactic to convince customers to replace debit cards on file with iTunes with credit cards. But the big takeaway is that from here on out, banks can only gain incremental value from iOS. If they want to create a unified payment system that customers can use as part of their existing banking relationships, they'll have to focus on Android. Should that happen, I doubt that Apple could prevent such moves from diluting its merchant value proposition. But such moves on the part of issuers are hardly long-term strategies to incentivize frequent usage, merchant participation and overall customer value. Learn more about how Experian can help you with your mobile banking needs please visit: http://ex.pn/1t3zCSJ?INTCMP=DA_Blog_Post091214

by John P. Robertson, Senior Business Process Specialist As a Senior Business Process Specialist for the Experian Decision Analytics, John provides guidance to clients in the areas of profitability strategies for risk based pricing and relationship profitability. He assists banks in developing and implementing successful transitions for commercial lending that improve both the financial efficiency of the lending process and the productivity of the lending officers. John has 26 years of experience in the banking industry, with prior background in cash, treasury, and asset /liability management. For quite some time now, the banking industry has experienced a flat funding curve. Very small spreads have existed between the short and long term rates. Slowly, we have begun to see the onset of a normalized curve. At this writing, the five year FHLB Advance rate is about 2.00%. A simplistic view of loan pricing looks something like this: + Interest Income + Non-Interest Income - Cost of Funds - Non-Interest Expense - Risk Expense = Income before Tax The example is pretty simple and straight forward, “back of the napkin” kind of stuff. We back into a spread needed to reach breakeven on a five year fixed rate loan by using the UBPR (Uniform Bank Performance Report) national peer average for Non-Interest Expense of approximately 3.00%. You would need a pre-tax rate requirement of 5.00% before you consider the risk and before you make any money. If you tack on 1.00% for risk and some kind of return expectation, the rate requirement would put you around a 6.00% offering level. From a lender’s perspective, a 6.00% rate on a minimal risk five year fixed rate loan doesn’t exist. They might as well go home. CFO’s have been asking themselves, “What do we do with this excess cash? We get such a paltry spread. How can we put higher yielding loans on our books at today’s competitive rates? We’ve got plenty of capital even with the new regulation requirements so can we repo the securities and use the net spread for our cost of funds?” Leveraging the excess cash and securities in order to meet the pressing rate demands may be a way banks have been funding selective loans at such low rates on highly competitive, quality loan originations of size. But you have to wonder, what about that old adage, “You don’t short fund long term loans.” Won’t you eventually have to deal with compression and “margin squeeze”? Oh and by the way, aren’t you creating a mismatch in the balance sheet which requires explanation. Are they buying a swap to extend the maturity? If so, are they really making their targeted return? If this is what they are doing, why not just accept a lower return but one that is better than the securities? Share your thoughts with me.

Online crooks are getting more sophisticated by the second. Nowadays, fraudsters have the ability to conduct “clean fraud,” obtaining legitimate identities of users from the black market or data breaches to compromise a victim’s card account. Malware, too, is becoming more sophisticated both in the mobile and non-mobile space. But how can organizations fight such high-level tactics in such a broad, complex space? John Sarreal, Senior Director of Product Management at 41st Parameter, an online fraud prevention player, sat down with PYMNTS after the recent release of the white paper “Surveillance, Staging, and the Fraud Lifecycle” to reveal the inner workings of a cyber criminal’s mind, what should be done before and after data is snatched, and which aspects of account takeover are the most overlooked and dangerous. Interview excerpts Take us through the mind of a cyber-criminal. What are the most sophisticated tactics used today to capture account information from corporate systems? JS: The amount of clean fraud that we see with our customers is unprecedented. By focusing on obtaining legitimate credentials and identities, fraudsters are more easily able to bypass traditional controls. This means that fraud tools need to adapt and gather additional attributes to augment their fraud screening. Although the techniques they’re using now to obtain these credentials are increasingly sophisticated, the MOs are still rooted in basic phishing and social engineering attacks. Fraudsters will use identity information obtained from the black market or data breaches to conduct very convincing phishing attacks to reveal everything that is needed to compromise a victim’s card account. There’s also increasing sophistication in the use of malware to steal sensitive credentials in both the mobile and non-mobile arena. In Android, for example, Google recently passed a vulnerability that allows sophisticated malware to impersonate digital certificate signing authorities. This vulnerability allowed the malware to install itself on a mobile device without any user notification or intervention – obviously, a very dangerous attack. Link to the podcast and transcript here.

Every prospecting list needs to be filtered by your organizations specific credit risk threshold. Whether you’re developing a campaign targeting super-prime, sub-prime, or consumers who fall somewhere in between, an effective credit risk model needs to do two things: 1) accurately represent a consumer’s risk level and 2) expand the scoreable population. The newly redeveloped VantageScore® credit score does both. With the VantageScore® credit score, you get a scoring model that’s calibrated to post-recession consumer behavior, as well the ability to score nearly 35 million additional consumers - consumers who are typically excluded from most marketing lists because they are invisible to older legacy models. Nearly a third of those newly-scoreable consumers are near-prime and prime. However, if your market is emerging to sub-prime consumers - you’ve found the mother-load! Delinquency isn’t the only risk to contend with. Bankruptcies can mean high losses for your organization at any risk level. Traditional credit risk models are not calibrated to specifically look for behavior that predicts future bankruptcies. Experian's Bankruptcy PLUS filters out high bankruptcy risk from your list. Using Bankruptcy PLUS you’re able to bring down your overall risk while removing as few people as possible. My next post looks into ways to identify profitable consumers in your list. For more see: Four steps to creating the ideal prospecting list.

At Experian, we frequently get asked by clients how they can get bigger mailing list that open new markets and reach more people. But bigger isn’t necessarily better, and it doesn’t always translate to a higher return on your marketing investment. Instead of just increasing volume, let’s consider a different, more focused approach - using the latest in analytic tools and scores. This approach relies on effective pre-screening to create the ideal prospecting lists based on your business objective. We’ve identified four key steps to building a prescreen list of your ideal prospects: Optimize risk selection Find the most profitable consumers Target customers who need or want your products Design the right offer In the next post, Optimal Risk Selection, I’ll dig deeper into each step and present some tools and scores that can help meet the objective of each.

By: Teri Tassara “Do more with less” is a pervasive and familiar mantra nowadays as lenders seek to make smarter and more precise lending decisions while expertly balancing growth objectives and tightened budgets. And lest we forget, banks must also consider the latest regulations and increased regulatory scrutiny from the industry’s governing bodies - such as OCC and CFPB. Nowadays, with the extensive application of predictive analytics in everyday lending practices, it makes sense to look to analytics to fine tune decision-making and achieve a greater return on investment in three common growth objectives for bankcard acquisitions: Profitable growth - How do I find the most profitable acquisition targets? How do I know the borrowing characteristic of each consumer? Are they high spend or high income? Do they carry a balance but always make timely payments? Universe expansion - How many more consumers are there that meet my lending criteria? How can I effectively reach them? Customer experience - How do I offer the right product to the right customer? How do I communicate to my customers that I understand their lending needs? To that end, growth objectives vary by lender; as such, so should their bankcard acquisitions analytical toolkit. The analytical toolkit arsenal should enable lenders to develop refined bankcard campaign strategies based on their specific objectives. Look for upcoming posts on the essential components of the bankcard acquisitions analytical toolkit.

By: Mike Horrocks The Wall Street Journal just recently posted an article that mentioned the cost of the financial regulations for some of the largest banks. Within the article it is staggering to see the cost of the financial crisis and also to see how so much of this could have been minimized by sound banking practices, adoption to technology, etc. As a former commercial banker and as I talk with associates in the banking industry, I know that there are more causes to point at for the crisis then there are fingers…but that is not the purpose of my blog today. My point is the same thing I ask my teenage boys when they get in trouble, “Now, what are you going to do to fix it?” Here are a couple of ideas that I want to share with the banking industry. Each bank and market you are going after is a bit unique; however think about these this week and what you could do. It is about the customer – the channel is just how you touch that customer. Every day you hear the branch office is dead and that mobile is the next wave. And yes, if I was a betting man, I would clearly say mobile is the way to go. But if you don’t do it right, you will drive customers away just as fast (check out the stats from a Google mobile banking study). At the end of the day, make sure you are where your customers want to be (and yes for some that could even be a branch). Trust is king. The Beatles may have said that “All You Need Is Love”, but in banking it is all about trust. Will my transaction go thru? Will my account be safe? Will I be able to do all that I need to do on this mobile phone and still be safe since it also has Angry Birds on it? If your customer cannot trust you to do what they feel are simple things, then they will walk. You have to protect your customers, as they try to do business with you and others. Regulations are here to stay. It pains me to say it, but this is going to be a truth for a long while. Banks need to make sure they check the box, stay safe, and then get on to doing what they do best – identify and manage risk. No bank will win the war for shareholder attention because they internally can answer the regulators better than the competition. When you are dealing with complicated issues like CCAR, Basel II or III, or any other item, working with professionals can help you stay on track. This last point represents a huge challenge for banks as the number of regulations imposed on financial institutions has grown significantly over the past five years. On top that the level of complexity behind each regulation is high, requiring in-depth knowledge to implement and comply. Lenders have to understand all the complexity of these regulations so they can find the balance to meet compliance obligations. At the same time they need to identify profitable business opportunities. Make sure to read our Comply whitepaper to gain more insight on regulations affecting financial institutions and how you can prepare your business. A little brainstorming and a single action toward each of these in the next 90 days will make a difference. So now, what are you going to do to fix it?
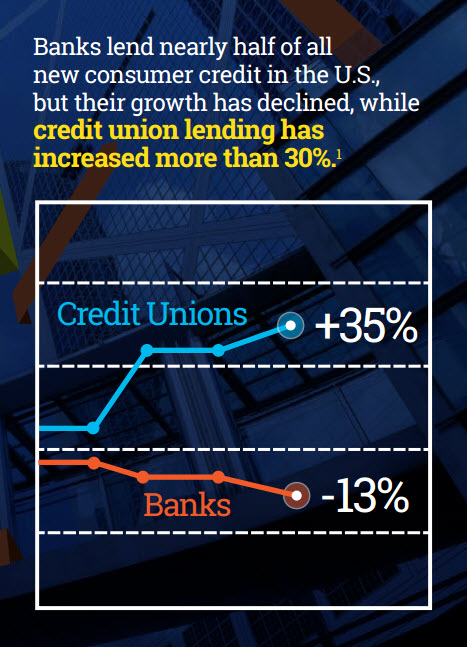
Are you sure you are making the best consumer credit decisions? Given the constantly evolving market conditions, it is a challenge to keep informed. In order to confidently grow and manage the bottom line, organizations need to avoid these four basic risks of making credit decisions with limited trend visibility. Competitive Risk - With limited visibility to industry trends, organizations cannot understand their position relative to peers. Product Risk - Organizations without access to the latest consumer behaviors cannot identify and capitalize on emerging trends. Market Risk - Decisions suffer when made without considering market trends in the context of the economy. Resource Risk - Extracting useful insights from vast market data requires abundant resources and comprehensive expertise. Get more information on the business risks of navigating credit decisions with limited trend visibility.

By: Mike Horrocks Living just outside of Indianapolis, I can tell you that the month of May is all about "The Greatest Spectacle in Racing", the Indy 500. The four horsemen of the apocalypse could be in town, but if those horses are not sponsored by Andretti Racing or Pennzoil – forget about it. This year the race was a close one, with three-time Indy 500 winner, Helio Castroneves, losing by .06 of a second. It doesn’t get much closer. So looking back, there are some great lessons from Helio that I want to share with auto lenders: You have to come out strong and with a well-oiled machine. Castroneves lead the race with no contest for 38 laps. You cannot do that without a great car and team. So ask yourself - are you handling your auto lending with the solution that has the ability to lead the market or are you having to go to the pits often, just to keep pace? You need to stay ahead of the pack until the end. Castroneves will be the first to admit that his car was not giving him all the power he wanted in the 196th lap. Now remember there are only 200 laps in the race, so with only four laps to go, that is not a good time to have a hiccup. If your lending strategy hasn't changed "since the first lap", you could have the same problem getting across the the finish line? Take time to make sure your automated scoring approach is valid, question your existing processes, and consider getting an outside look from leaders in the industry to make sure your are still firing on all cylinders. Time kills. Castroneves lost by .06 seconds. That .06 of a second means he was denied access into a very select club of four time winners. That .06 of a second means he does not get to drink that coveted glass of milk. If your solution is not providing your customers with the fastest and best credit offers, how many deals are you losing? What exclusive club of top auto lenders are you being denied access to? Second place is no fun. If you're Castroneves, there's no substitute for finishing first at the Indianapolis Motor Speedway. Likewise, in today’s market, there is more need than ever to be the Winner’s Circle. Take a pit stop and check out your lending process and see how you're performing against your competitors and in the spirit of the race – “Ladies and gentlemen, start your engines!”
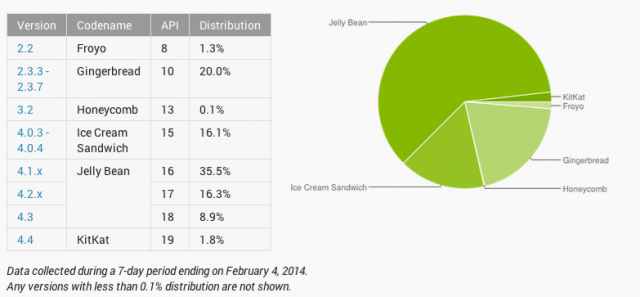
Both Visa and MasterCard announced their support for Host Card Emulation (HCE) and their intent to release HCE specifications soon. I have been talking about HCE from late 2012 (partly due to my involvement with SimplyTapp) and you could read as to why HCE matter and what Android KitKat-HCE announcement meant for payments. But in light of the network certification announcements yesterday, this post is an attempt to provide some perspective on what the Visa/MasterCard moves mean, how do their approaches differ in certifying payments using cloud hosted credentials, what should issuers expect from a device and terminal support perspective, why retailers should take note of the debate around HCE and ultimately – the role I expect Google to continue to play around HCE. All good stuff. First, what do the Visa/MasterCard announcements mean? It means that it’s time for banks and other issuers to stop looking for directions. The network announcements around HCE specifications provide the clarity required by issuers to meaningfully invest in mobile contactless provisioning and payment. Further, it removes some of the unfavorable economics inherited from a secure element-centric model, who were forced to default to credit cards with higher interchange in the wallet. Renting space on the secure element cost a pretty penny and that is without taking operational costs in to consideration, and as an issuer if you are starting in the red out of the gate, you were not about to put a Durbin controlled debit card in the wallet. But those compulsions go with the wind now, as you are no longer weighed down by these costs and complexities on day one. And further, the door is open for retailers with private label programs or gift cards to also look at this route with a lot more interest. And they are. MasterCard mentioned bank pilots around HCE in its press release, but MCX is hardly the only retailer payment initiative in town. Let me leave it at that. How do the Visa/MasterCard specs differ? From the press releases, some of those differences are evident – but I believe they will coalesce at some point in the future. MasterCard’s approach speaks to mobile contact-less as the only payment modality, whereas Visa refers to augmenting the PayWave standard with QR and in-app payments in the future. Both approaches refer to payment tokens (single or multi-use) and one can expect them to work together with cloud provisioned card profiles, to secure the payment transaction and verify transactional integrity. To MasterCard’s benefit – it has given much thought to ensuring that these steps – provisioning the card profile, issuing payment tokens et al – are invisible to the consumer and therefore refrains from adding undue friction. I am a purist at heart – and I go back to the first iteration of Google Wallet – where all I had to do to pay was turn on the screen and place the device on the till. That is the simplicity to beat for any issuer or retailer payment experiences when using contactless. Otherwise, they are better off ripping out the point-of-sale altogether. MasterCard’s details also makes a reference to a PIN. The PIN will not be verified offline as it would have been if a Secure Element would have been present in the device, rather – it would be verified online which tells me that an incorrect PIN if input would be used to create an “incorrect cryptogram” which would be rejected upstream. Now I am conflicted using a PIN at the point of sale for anything – to me it is but a Band-Aid, it reflects the inability to reduce fraud without introducing friction. Visa so far seems to be intentionally light on details around mandating a PIN, and I believe not forcing one would be the correct approach – as you wouldn’t want to constrain issuers to entering a PIN as means to do authentication, and instead should have laid down the requirements but left it to the market to decide what would suffice – PIN, biometrics et al. Again – I hope these specs will continue to evolve and move towards a more amenable view towards customer authentication. Where do we stand with device and terminal support? All of this is mute if there are not enough devices that support NFC and specifically – Android KitKat. But if you consider Samsung devices by themselves (which is all one should consider for Android) they control over 30% of the NA market – 44.1 million devices sold in 2013 alone. Lion share of those devices support NFC out of the box – including Galaxy Note II and 3, Galaxy S3 and S4 – and their variants mini, Active, Xoom et al. And still, the disparity in their approach to secure elements, continuing lack of availability in standards and Android support – Tap and Pay was largely a dream. What was also worrisome is that 3 months after the launch of Android KitKat – it still struggles under 2% in device distribution. That being said, things are expected to get markedly better for Samsung devices at least. Samsung has noted that 14 of its newer devices will receive KitKat. These devices include all the NFC phones I have listed above. Carriers must follow through quickly (tongue firmly in cheek) to deliver on this promise before customers with old S3 devices see their contracts expire and move to a competitor (iPhone 6?). Though there was always speculation as to whether an MNO will reject HCE as part of the Android distribution, I see that as highly unlikely. Even carriers know a dead horse when they see one, and Isis’s current model is anything but one. Maybe Isis will move to embrace HCE. And then there is the issue of merchant terminals. When a large block of merchants are invested in upending the role of networks in the payment value chain – that intent ripples far and wide in the payments ecosystem. Though it’s a given that merchants of all sizes can expect to re-terminalize in the next couple of years to chip & pin (with contactless under the hood) – it is still the prerogative of the merchant as to whether the contactless capability is left turned on or off. And if merchants toe Best Buy’s strategy in how it opted to turn it off store-wide, then that limits the utility of an NFC wallet. And why wouldn’t they? Merchants have always viewed “Accept all cards” to also mean “Accept all cards despite the form factor” and believes that contactless could come to occupy a higher interchange tier in the future – as questions around fraud risk are sufficiently answered by the device in real-time. This fear is though largely unsubstantiated, as networks have not indicated that they could come to view mobile contact-less as being a “Card Present Plus” category that charges more. But in the absence of any real assurances, fear, uncertainty and doubt runs rampant. But what could a retailer do with HCE? If re-terminalization is certain, then retailers could do much to explore how to leverage it to close the gap with their customer. Private label credit, closed loop are viable alternatives that can be now carried over contactless – and if previously retailers were cut out of the equation due to heavy costs and complexity for provisioning cards to phones, they have none of those limitations now. A merchant could now fold in a closed loop product (like a gift card) in to their mobile app – and accept those payments over contact-less without resorting to clunky QR or barcode schemes. There is a lot of potential in the closed loop space with HCE, that Retailers are ignoring due to a “scorched earth” approach towards contactless. But smarter merchants are asking ‘how’. Finally, what about Google? Google deserves much praise for finally including HCE in Android and paving the way for brands to recognize the opportunity and certify the approach. That being said, Google has no unequal advantage with HCE. In fact, Google has little to do with HCE going forward, despite GoogleWallet utilization of HCE in the future. I would say – HCE has as much to do with Google going forward, as Amazon’s Kindle Fire has to do with Android. Banks and Retailers have to now decide what this means for them – and view HCE as separate to Google – and embrace it if they believe it has potential to incent their brands to remain top of wallet, and top of mind for the consumer. It is a level playing field, finally. Where do you go next? Indeed – there is a lot to take in – starting with HCE’s role, where it fit in to your payment strategy, impact and differences in Visa/MasterCard approaches, weaving all of these in to your mobile assets while not compromising on customer experience. Clarity and context is key and we can help with both. Reach out to us for a conversation. HCE is a means to an end – freeing you from the costs and complexities of leveraging contactless infrastructure to deliver an end-to-end mobile experience, but there is still the question of how your business should evolve to cater to the needs of your customers in the mobile channel. Payment is after all, just one piece of the puzzle.