Fraud & Identity Management

It’s the holiday season — time for jingle bells, lighting candles, shopping sprees and credit card fraud. But we’re prepared. Our risk analyst team constantly monitors our FraudNet solution performance to identify anomalies our clients experience as millions of transactions occur this month. At its core, FraudNet analyzes incoming events to determine the risk level and to allow legitimate events to process without causing frustrating friction for legitimate customers. That ensures our clients can recognize good customers across digital devices and channels while reducing fraud attacks and the need for internal manual reviews. But what happens when things don’t go as planned? Here’s a recent example. One of our banking clients noticed an abnormally high investigation queue after a routine risk engine tuning. Our risk analyst team looked further into the attacks to determine the cause and assess whether it was a tuning issue or a true fraud attack. After an initial analysis, the team learned that the events shared many of the same characteristics: Came from the same geo location that has been seen in previous attacks on clients Showed suspicious device and browser characteristics that were recognized by Experian’s device identification technology Identified suspicious patterns that have been observed in other recent attacks on banks The conclusion was that it wasn’t a mistake. FraudNet had correctly identified these transactions as suspicious. Experian® then worked with our client and recommended a strategy to ensure this attack was appropriately managed. This example highlights the power of device identification technology as a mechanism to detect emerging fraud threats, as well as link analysis tools and the expertise of a highly trained fraud analyst to uncover suspicious events that might otherwise go unnoticed. In addition to proprietary device intelligence capabilities, our clients take advantage of a suite of capabilities that can further enhance a seamless authentication experience for legitimate customers while increasing fraud detection for bad actors. Using advanced analytics, we can detect patterns and anomalies that may indicate a fraudulent identity is being used. Additionally, through our CrossCore® platform businesses can leverage advanced innovation, such as physical and behavioral biometrics (facial recognition, how a person holds a phone, mouse movements, data entry style), email verification (email tenure, reported fraud on email identities), document verification (autofill, liveliness detection) and digital behavior risk indicators (transaction behavior, transaction velocity), to further advance their existing risk mitigation strategies and efficacy. With expanding partnerships and capabilities offered via Experian’s CrossCore platform, in conjunction with consultative industry expertise, businesses can be more confident during the authentication process to ensure a superb, frictionless customer experience without compromising security.

As our society becomes ever more dependent on everything mobile, criminals are continually searching for and exploiting weaknesses in the digital ecosystem, causing significant harm to consumers, businesses and the economy. In fact, according to our 2018 Global Fraud & Identity Report, 72 percent of business executives are more concerned than ever about the impact of fraud. Yet, despite the awareness and concern, 54 percent of businesses are only “somewhat confident” in their ability to detect fraud. That needs to change, and it needs to change right away. Our industry has thrived by providing products and services that root out bad transactions and detect fraud with minimal consumer friction. We continue to innovate new ways to authenticate consumers, apply new cloud technologies, machine learning, self-service portals and biometrics. Yet, the fraud issue still exists. It hasn’t gone away. How do we provide effective means to prevent fraud without inconveniencing everyone in the process? That’s the conundrum. Unfortunately, a silver bullet doesn’t exist. As much as we would like to build a system that can detect all fraud, eliminate all consumer friction, we can’t. We’re not there yet. As long as money has changed hands, as long as there are opportunities to steal, criminals will find the weak points – the soft spots. That said, we are making significant progress. Advances in technology and innovation help us bring new solutions to market more quickly, with more predictive power than ever, and the ability to help clients to turn these services on in days and weeks. So, what is Experian doing? We’ve been in the business of fraud detection and identity verification for more than 30 years. We’ve seen fraud patterns evolve over time, and our product portfolio evolves in lock-step to counter the newest fraud vectors. Synthetic identity fraud, loan stacking, counterfeit, identity theft; the specific fraud attacks may change but our solution stack counters each of those threats. We are on a continuous innovation path, and we need to be. Our consumer and small business databases are unmatched in the industry for quality and coverage, and that is an invaluable asset in the fight against fraud. It used to be that knowing something about a person was the same as authenticating that same person. That’s just not the case today. But, just because I may not be the only person who knows where I live, doesn’t mean that identity information is obsolete. It is incredibly valuable, just in different ways today. And that’s where our scientists come into their own, providing complex predictive solutions that utilize a plethora of data and insight to create the ultimate in predictive performance. We go beyond traditional fraud detection methods, such as knowledge-based authentication, to offer a custom mix of passive and active authentication solutions that improve security and the customer experience. You want the latest deep learning techniques? We have them. You want custom models scored in milliseconds alongside your existing data requests. We can do that. You want a mix of cloud deployment, dedicated hosted services and on-premise? We can do that too. We have more than 20 partners across the globe, creating the most comprehensive identity management network anywhere. We also have teams of experts across the world with the know how to combine Experian and partner expertise to craft a bespoke solution that is unrivaled in detection performance. The results speak for themselves: Experian analyzes more than a billion credit applications per year for fraud and identity, and we’ve helped our clients save more than $2 billion in annual fraud losses globally. CrossCore™, our fraud prevention and identity management platform, leverages the full breadth of Experian data as well as the data assets of our partners. We execute machine learning models on every decision to help improve the accuracy and speed with which decisions are made. We’ve seen CrossCore machine learning result in a more than 40 percent improvement in fraud detection compared to rules-based systems. Our certified partner community for CrossCore includes only the most reputable leaders in the fraud industry. We also understand the need to expand our data to cover those who may not be credit active. We have the largest and most unique sets of alternative credit data among the credit bureaus, that includes our Clarity Services and RentBureau divisions. This rich data helps our clients verify an individual’s identity, even if they have a thin credit file. The data also helps us determine a credit applicant’s ability to pay, so that consumers are empowered to pursue the opportunities that are right for them. And in the background, our models are constantly checking for signs of fraud, so that consumers and clients feel protected. Fraud prevention and identity management are built upon a foundation of trust, innovation and keeping the consumer at the heart of every decision. This is where I’m proud to say that Experian stands apart. We realize that criminals will continue to look for new ways to commit fraud, and we are continually striving to stay one step ahead of them. Through our unparalleled scale of data, partnerships and commitment to innovation, we will help businesses become more confident in their ability to recognize good people and transactions, provide great experiences, and protect against fraud.

Synthetic identities come from accounts held not by actual individuals, but by fabricated identities created to perpetrate fraud. It often starts with stealing a child’s Social Security number (SSN) and then blending fictitious and factual data, such as a name, a mailing address and a telephone number. What’s interesting is the increase in consumer awareness about synthetic identities. Previously, synthetic identity was a lender concern, often showing itself in delinquent accounts since the individual was fabricated. Consumers are becoming aware of synthetic ID fraud because of who the victims are — children. Based on findings from a recent Experian survey, the average age of child victims is only 12 years old. Children are attractive victims since fraud that uses their personal identifying information can go for years before being detected. I recently was interviewed by Forbes about the increase of synthetic identities being used to open auto loans and how your child’s SSN could be used to get a phony auto loan. The article provides a good overview of this growing concern for parents and lenders. A recent Javelin study found that more than 1 million children were victims of fraud. Most upsetting is that children are often betrayed by people close to them -- while only 7 percent of adults are victimized by someone they know, 60 percent of victims under 18 know the fraudster. Unfortunately, when families are in a tight spot financially they often resort to using their child’s SSN to create a clean credit record. Fraud is an issue we all must deal with — lenders, consumers and even minors — and the best course of action is to protect ourselves and our organizations.

Federal legislation makes verifying an individual’s identity by scanning identity documents during onboarding legal in all 50 states Originally posted on Mitek blog The Making Online Banking Initiation Legal and Easy (MOBILE) Act officially became law on May 24, 2018, authorizing a national standard for banks to scan and retain information from driver’s licenses and identity cards as part of a customer online onboarding process, via smartphone or website. This bill, which was proposed in 2017 with bipartisan support, allows financial institutions to fully deploy mobile technology that can make digital account openings across all states seamless and cost efficient. The MOBILE Act also stipulates that the digital image would be destroyed after account opening to further ensure customer data security. As an additional security measure, section 213 of the act mandates an update to the system to confirm matches of names to social security numbers. “The additional security this process could add for online account origination was a key selling point with the Equifax data breach fresh on everyone’s minds,” Scott Sargent, of counsel in the law firm Baker Donelson’s financial service practice, recently commented on AmericanBanker.com. Read the full article here. Though digital banking and an online onboarding process has already been a best practice for financial institutions in recent years, the MOBILE Act officially overrules any potential state legislation that, up to this point, has not recognized digital images of identity documents as valid. The MOBILE Act states: “This bill authorizes a financial institution to record personal information from a scan, copy, or image of an individual’s driver’s license or personal identification card and store the information electronically when an individual initiates an online request to open an account or obtain a financial product. The financial institution may use the information for the purpose of verifying the authenticity of the driver’s license or identification card, verifying the identity of the individual, or complying with legal requirements.” Why adopt online banking? The recently passed MOBILE Act is a boon for both financial institutions and end users. The legislation: Enables and encourages financial institutions to meet their digital transformation goals Makes the process safe with digital ID verification capabilities and other security measures Reduces time, manual Know Your Customer (KYC) duties and costs to financial institutions for onboarding new customers Provides the convenient, on-demand experience that customers want and expect The facts: 61% of people use their mobile phone to carry out banking activity.1 77% of Americans have smartphones.2 50 million consumers who are unbanked or underbanked use smartphones.3 The MOBILE Act doesn’t require any regulatory implementation. Banks can access this real-time electronic process directly or through vendors. Read all you need to know about the MOBILE Act here. Find out more about a better way to manage fraud and identity services. References 1Mobile Ecosystem Forum, MEF Mobile Money Report (https://mobileecosystemforum.com/mobile-money-report/), Feb. 5, 2018. 2Pew Research Center, Mobile Fact Sheet (http://www.pewinternet.org/fact-sheet/mobile/), Jan. 30, 2017. 3The Federal Reserve System, Consumers and Mobile Financial Services 2015 (https://www.federalreserve.gov/econresdata/consumers-and-mobile-financial-services-report-201503.pdf), March 2015.

Customer Identification Program (CIP) solution through CrossCore® Every day, I work closely with clients to reduce the negative side effects of fraud prevention. I hear the need for lower false-positive rates; maximum fraud detection in populations; and simple, streamlined verification processes. Lately, more conversations have turned toward ID verification needs for Customer Information Program (CIP) administration. As it turns out, barriers to growth, high customer friction and high costs dominate the CIP landscape. While the marketplace struggles to manage the impact of fraud prevention, CIP routinely disrupts more than 10 percent of new customer acquisitions. Internally at Experian, we talk about this as the biggest ID problem our customers aren’t solving. Think about this: The fight for business in the CIP space quickly turned to price, and price was defined by unit cost. But what’s the real cost? One of the dominant CIP solutions uses a series of hyperlinks to connect identity data. Every click is a new charge. Their website invites users to dig into the data — manually. Users keep digging, and they keep paying. And the challenges don’t stop there. Consider the data sources used for these solutions. The winners of the price fight built CIP solutions around credit bureau header data. What does that do for growth? If the identity wasn’t sufficiently verified when a credit report was pulled, does it make sense to go back to the same data source? Keep digging. Cha-ching, cha-ching. Right about now, you might be feeling like there’s some sleight of hand going on. The true cost of CIP administration is much more than a single unit price. It’s many units, manual effort, recycled data and frustrated customers — and it impacts far more clients than fraud prevention. CIP needs have moved far beyond the demand for a low-cost solution. We’re thrilled to be leading the move toward more robust data and decision capabilities to CIP through CrossCore®. With its open architecture and flexible decision structure, our CrossCore platform enables access to a diverse and robust set of data sources to meet these needs. CrossCore unites Experian data, client data and a growing list of available partner data to deliver an intelligent and cost-conscious approach to managing fraud and identity challenges. The next step will unify CIP administration, fraud analytics and a range of verification treatment options together on the CrossCore platform as well. Spoiler alert. We’ve already taken that step.

Although it’s hard to imagine, some synthetic identities are being used for purposes other than fraud. Here are 3 types of common synthetic identities and why they’re created: Bad — To circumvent lag times and delays in establishing a legitimate identity and data footprint. Worse — To “repair” credit, hoping to start again with a higher credit rating under a new, assumed identity. Worst — To commit fraud by opening various accounts with no intention of paying those debts or service fees. While all these synthetic identity types are detrimental to the ecosystem shared by consumers, institutions and service providers, they should be separated by type — guiding appropriate treatment. Learn more in our new white paper produced with Whitepages Pro, Fighting synthetic identity theft: getting beyond Social Security numbers. Download now>
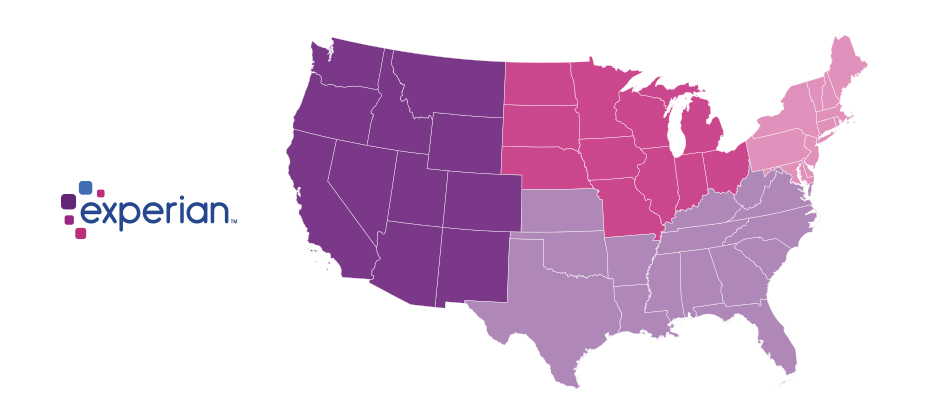
With 16.7 million reported victims of identity fraud in 2017 (that’s 6.64 percent of the U.S. population), it was another record year for the number of fraud victims. And as online and mobile transaction growth continued to significantly outpace brick-and-mortar growth, criminal attacks also grew rapidly. This past year, we saw an increase of more than 30 percent in e-commerce fraud attacks compared with 2016. As we’ve done over the past three years, Experian® analyzed millions of online transactions to identify fraud attack rates for both shipping and billing locations across the United States. We looked at several data points, including geography and IP address, to help businesses better understand how and where fraud is being perpetrated so they can better protect against it. The 2017 e-commerce fraud attack rate analysis shows: Delaware and Oregon continue to be the riskiest states for both billing and shipping fraud. Delaware; Oregon; Washington, D.C.; Florida; and Georgia are the top five riskiest states for billing fraud. Delaware, Oregon, Florida, New York and California are the top five riskiest states for shipping fraud, accounting for 50 percent of total fraud attacks. South El Monte, Calif., is the riskiest city overall, with an increase in shipping fraud of approximately 230 percent. Shipping fraud most often occurs near major airports and seaports due to reshippers and freight forwarders that receive domestic goods and often send them overseas. When a transaction originates from an international IP address, shipping fraud is 6.7 times likelier than the average, while billing fraud becomes 7.1 times likelier. Where is e-commerce fraud happening? Typically, the highest-risk areas for fraud are in ZIP™ codes and cities near large ports of entry or airports. These are ideal locations to reship fraudulent merchandise, enabling criminals to move stolen goods more effectively. Top 10 riskiest billing ZIP™ codes Top 10 riskiest shipping ZIP™ codes 97252 Portland, OR 97079 Beaverton, OR 33198 Miami, FL 33122 Miami, FL 33166 Miami, FL 91733 South El Monte, CA 33122 Miami, FL 97251 Portland, OR 77060 Houston, TX 97250 Portland, OR 33195 Miami, FL 33166 Miami, FL 97250 Portland, OR 97252 Portland, OR 97251 Portland, OR 33198 Miami, FL 33191 Miami, FL 33195 Miami, FL 97253 Portland, OR 33192 Miami, FL Source: Experian.com Source: Experian.com What’s more, many of the riskiest ZIP™ codes and cities experience a high volume of transactions originating from international IP addresses. In fact, the top 10 riskiest ZIP codes overall tend to experience fraudulent activity from numerous countries overseas, including China, Venezuela, Taiwan and Hong Kong, and Argentina. These fraudsters tend to implement complex fraud schemes that can cost businesses millions of dollars in fraud losses. Additionally, the analysis shows that traffic coming from a proxy server — which could originate from domestic and international IP addresses — is 74 times riskier than the average transaction. The problem The increase in e-commerce fraud attacks shouldn’t come as a huge surprise. The uptick in data breaches, merchants’ continued adoption of EMV-enabled terminals to protect against counterfeit card fraud and the abundance of consumer data on the dark web means that information is even more accessible to criminals. This enables them to open fraudulent accounts, take over legitimate accounts and submit fraudulent transactions. Another reason for the increase is automation. In the past, criminals needed a strong understanding of fraud methods and technology, but they can now bring down an entire organization by simply downloading a file and automating the submission of thousands of applications or transactions simultaneously. Since fraudsters need to make these transactions appear as normal as possible, they often leverage the cardholder’s actual billing details with slight differences, such as e-mail address or shipping location. Unfortunately, the mass availability of compromised data and the abundance of fraudsters makes it increasingly challenging to identify and separate legitimate customers from attackers across the country. Because of the widespread prevalence of fraud and data compromises, we don’t see billing fraud concentrated in just one region of the country. In fact, the top five states for billing fraud make up only about 18 percent of overall fraud attacks. Top 5 riskiest billing fraud states Top 5 riskiest shipping fraud states State Fraud attack rate State Fraud attack rate Delaware 93.4 Delaware 195.9 Oregon 86.1 Oregon 170.1 Washington, D.C. 46.5 Florida 45.1 Florida 39.2 New York 37.3 Georgia 31.5 California 32.6 Source: Experian.com Source: Experian.com Prevention and protection need to be the priority As businesses get a better understanding of how and where fraud is perpetrated, they can implement proactive strategies to detect and prevent attacks, as well as protect payment information. While no one single strategy can address the entire scope of fraud, there are advanced data sets and technology — such as device intelligence, behavioral and physical biometrics, document verification and entity resolution — that can help businesses make better fraud decisions. Fortunately, consumers can also play a major role in safeguarding their information. In addition to regularly checking their credit reports and bank/credit card statements for fraudulent activity, consumers can limit the data they share on social networking sites, where attackers often begin when perpetrating identity fraud. While we continue to help both organizations and consumers limit their exposure to e-commerce fraud, we anticipate that criminals will attempt more sophisticated fraud schemes. But businesses can stay ahead of the curve. This comes down to having a keen understanding of how fraud is being perpetrated, as well as leveraging data, technology and multiple layered strategies to better recognize legitimate customers and make more precise fraud decisions. View our e-commerce fraud heat map and download the top 100 riskiest ZIP codes in the United States. Experian is a nonexclusive full-service provider licensee of the United States Postal Service®. The following trademark is owned by the United States Postal Service®: ZIP. The price for Experian’s services is not established, controlled or approved by the United States Postal Service.

Managing your customer accounts at the identity level is ambitious and necessary, but possible Identity-related fraud exposure and losses continue to grow. The underlying schemes have elevated in complexity. Because it’s more difficult to perpetrate “card present” fraud in the post–chip-and-signature rollout here in the United States, bad guys are more motivated and getting better at identity theft and synthetic identity attacks. Their organized nefarious response takes the form of alternate attack vectors and methodologies — which means you need to stamp out any detected exposure point in your fraud prevention strategies as soon as it’s detected. Experian’s recently published 2018 Global Fraud and Identity Report suggests two-thirds, or 7 out of every ten, consumers want to see visible security protocols when they transact. But an ever-growing percentage of them, fueled in no small part by those tech-savvy millennials, expect to be recognized with little or no friction. In fact, 42 percent of the surveyed consumers who stated they would do more transactions online if there weren’t so many security hurdles to overcome were — you guessed it — millennials. So how do you implement identity and account management procedures that are effective and, in some cases, even obvious while being passive enough to not add friction to the user experience? In other words, from the consumer’s perspective, “Let me know you know me and are protecting me but not making it too difficult for me when I want to access or manage my account.” Let’s get one thing out of the way first. This isn’t a one-time project or effort. It is, however, a commitment to the continued informing of your account management strategies with updated identity intelligence. You need to make better decisions on when to let a low-risk account transaction (monetary or nonmonetary) pass and when to double down a bit and step up authentication or risk assessment checks. I’d suggest this is most easily accomplished through a single, real-time access point to myriad services that should, at the very least, include: Identity verification and reverification checks for ongoing reaffirmation of your customer identity data quality and accuracy. Know Your Customer program requirements, anyone? Targeted identity risk scores and underlying attributes designed to isolate identity theft, first-party fraud and synthetic identity. Fraud risk comes in many flavors. So must your analytics. Device intelligence and risk assessment. A customer identity is no longer just their name, address, Social Security number and date of birth. It’s their phone number, email address and the various devices they use to access your services as well. Knowing how that combination of elements presents itself over time is critical. Layered passive or more active authentication options such as document verification, biometrics, behavioral metrics, knowledge-based verification and alternative data sources. Ongoing identity monitoring and proactive alerting and segmentation of customers whose identity risk has shifted to the point of required treatment. Orchestration, workflow and decisioning capabilities that allow your team to make sense of the many innovative options available in customer recognition and risk assessment — without a “throw the kitchen sink at this problem” approach that will undoubtedly be way too costly in dollars spent and good customers annoyed. Fraud attacks are dynamic. Your customers’ perceptions and expectations will continue to evolve. The markets you address and the services you provide will vary in risk and reward. An innovative marketplace of identity management services can overwhelm. Make sure your strategic identity management partner has good answers to all of this and enables you to future-proof your investments.

Identify your customers to spot fraud. It’s a simple concept, but it’s not so simple to do. In our 2018 Global Fraud and Identity Report, we found that consumers expect to be recognized and welcomed wherever and whenever they do business. Here are some other interesting findings regarding recognition and fraud: 66% of consumers surveyed appreciate seeing visible security when doing business online because it makes them feel protected. 75% of businesses want security measures that have little impact on consumers. More than half of businesses still rely on passwords as their top form of authentication. Even though you can’t see your customers face-to-face, the importance of being recognized can’t be overemphasized. How well are you recognizing your customers? Can you recognize your customers?

From malware and phishing to expansive distributed denial-of-service attacks, the sophistication, scale and impact of cyberattacks have evolved significantly in recent years. Mitigate risk by employing these best practices: Manage third-party risks. Regularly review response plans. Opt in to software updates. Educate, educate, educate. Organizations must adopt stronger, more advanced technical solutions to protect sensitive data. While enhanced technology is necessary for defending against data breaches, it can’t work independently. Learn more

While it’s important to recognize synthetic identities when they knock on your door, it’s just as important to conduct regular portfolio checkups. Every circumstance has unique parameters, but the overarching steps necessary to mitigate fraud from synthetic IDs remain the same: Identify current and near-term exposure using targeted segmentation analysis. Apply technology that alerts you when identity data doesn’t add up. Differentiate fraudulent identities from those simply based on bad data. Review front- and back-end screening procedures until they satisfy best practices. Achieve a “single customer view” for all account holders across access channels — online, mobile, call center and face-to-face. With the right set of analytics and decisioning tools, you can reduce exposure to fraud and losses stemming from synthetic identity attacks at the beginning and across the Customer Life Cycle. Learn more

Millions of Americans placed a credit freeze or restricted access to their credit file in recent months to keep identity thieves at bay. Credit freezes keep any new creditors from seeing a consumer’s credit file, which makes it nearly impossible for hackers to open new accounts fraudulently. But a credit freeze can also be problematic for consumers when they are finally ready to consider new credit products and loans. We’ve heard from credit unions and other lenders about sharing best practices to help streamline the process for consumers who want to permanently or temporarily lift the freeze to apply for a legitimate line of credit. Following are the three ways to help clients with a frozen Experian report quickly and efficiently allow access. Unfreeze account: This will remove the freeze entirely from the consumer’s credit report so that it may be accessed with the consumer’s permission. To do this, the consumer will need to contact Experian online, by phone or mail and provide his unique personal identification number (PIN) code—provided when the consumer froze his account—to un-freeze the report. Thaw account: An action that will temporarily remove the freeze for a timeframe determined by the consumer. The consumer should contact Experian online, by phone, or mail and provide his unique PIN code to thaw the report. Grant a creditor one-time access: A consumer may provide a different/temporary PIN to a lender to access the report just once. The PIN can be emailed to the consumer, presented on screen if the consumer is online, or provided on the phone or by mail. Typically, a consumer’s request to thaw or un-freeze his credit file online or by phone will thaw or un-freeze the file within minutes. Download Checklist Experian can be reached: Online: www.experian.com/freeze Phone: 888-397-3742 Mail: P.O. Box 9554, Allen, Texas 75013 Remember, if a consumer has a frozen credit file with all three credit reporting agencies, he will need to contact each agency to enable access to his report.

June 2018 will mark the one-year anniversary of the National Institute of Standards and Technology (NIST) release of Special Publication 800-63-3, Digital Identity Guidelines. While federal agencies are the most directly impacted, this guidance signals a seismic shift in identity proofing across the entire ecosystem of consumers, private sector businesses and public sector agencies. It’s the clearest claim I’ve seen to date that traditional, and rather basic, personally identifiable information (PII) verification should no longer be trusted for remote user interaction. For those of us in the fraud and identity space, this isn’t a new revelation, but one we as an industry have been dealing with for years. As the data breach floodgates continue to be pushed further open, PII is a commodity for the fraudsters, evident in PII prices on the dark web, which are often lower than your favorite latte. Identity-related schemes have increased due to fraud attacks shifting away from card compromise (due to the U.S. rollout of chip-and-signature cards), double-digit growth in online and mobile consumer channels, and high-profile fraud events within both the public and private sector. It’s no shock that NIST has taken a sledgehammer to previous guidance around identity proofing and replaced it with an aggressive and rather challenging set of requirements seemingly founded in the assumption that all PII (names, addresses, dates of birth, Social Security numbers, etc.) is either compromised or easily can be compromised in the future. So where does this leave us? I applaud the pragmatic approach to the new NIST standards and consider it a signal to all of us in the identity marketplace. It’s aggressive and aspirational in raising the bar in identity proofing and management. I welcome the challenge in serving our public sector clients, as we have done for nearly a decade. Our innovative approach to layered levels of identity verification, validation, risk assessment and monitoring adhere to the recommendations of the new NIST standards. I do, however, recommend that any institution applying these standards to their own processes and applications ensure they place equal focus on comparable alternatives for those addressable populations and users who are likely to either opt out of, or fail, initial verification steps stringently aligned with the new requirements. While too early to accurately forecast, it’s relatively safe to assume that the percentage of the population “falling out of the process” may easily be counted in the double digits. It’s only through advanced analytics and technology reliant on a significant breadth and depth of identity data and observations that we can provide trust and confidence across such a diverse population in age, demographics, expectations and access.

I recently sat down with Kathleen Peters, SVP and Head of Fraud and Identity, to discuss the state of fraud and identity, the pace of change in the space and her recent inclusion in the Top 100 influencers in Identity by One World Identity. ----------- Traci: Congratulations on being included on the Top 100 influencers list. What a nice honor. Kathleen: Yes, thank you. It is a nice honor and inspiring to be included among some great innovators in the industry. The list includes entrepreneurs to leaders of large organizations like us. It’s a nice mix across all facets of identity. T: Tell me about your role. How long have you been at Experian? K: I lead the team that defines the product strategy for our global fraud and ID portfolio. I’ve been with Experian just over four years, joining soon after we acquired 41st Parameter®. T: What was your first job? K: My first job out of college was with Motorola in Chicago. I was an electrical engineer, working on advanced cellphone technology. T: They were not able to keep up with the market? K: The entire industry was caught by the introduction of the iPhone. All the major cellphone companies were impacted — Nokia, Ericsson, Siemens and others. Talk about disrupting an industry. T: Yeah. These are great examples of how the disrupters have taken out the initial companies. Certainly, Motorola, Nokia, those companies. Even RIM Blackberry, which redefined the digital or cellular space, has all but disappeared. K: Yes, exactly. It was interesting to watch RIM Blackberry when they disrupted Motorola’s pager business. Motorola had a very robust pager line. Even then they had a two-way pager with a keyboard. They just missed the idea of mobile email completely. It’s really, really fascinating to look back now. T: Changing the subject a little, what motivates you to get out of bed in the morning? K: One of my favorite questions. I’m a very purpose-driven person. One of the things I really like about my role and one of the reasons I came to Experian in the first place is that I could see this huge potential within the company to combine offline and online identity information and transaction information to better recognize people and stop fraud. T: What do you see as the biggest threat to organizations today? K: I would have to say the pace of change. As we were just talking about, major industries can be disrupted seemingly overnight. We’re in the midst of a real digital transformation in how we live, how we work, how we share information and even how we share money. The threat to companies is twofold. One is the “friendly fire” threat, like the pace of change, disrupters to the market, new ways of doing things and keeping pace with that innovation. The second threat is that with digitization comes new types of security and fraud risks. Today, organizations need to be ever-vigilant about their security. T: How do you stay ahead of that pace of change? K: Well, my husband and I have lived in Silicon Valley since 1997. Technology and innovation are all around us. We read about it and we hear about it in the news. We engage with our neighbors and other people who we meet socially and within our networks. You can’t help but be immersed in it all the time. It certainly influences the way we go about our lives and how we think and act and engage as a family. We’re all technically curious. We have two kids, and our neighborhood high school, Homestead High, is the same high school Steve Jobs went to. It’s fun that way. T: Definitely. What are some of the most effective ways for businesses to combat the threat of fraud? K: I firmly believe that nowadays it all needs to start with identity. What we’ve found — and confirmed through research in our recent Global Fraud Report, plus conversations I’ve had with clients and analysts — is that if you can better recognize someone, you’ll go a long way to prevent fraud. And it does more than prevent fraud; it provides a better experience for the people you’re engaged with. Because once you recognize an individual, that initiates a trusted relationship between the two of you. Once people feel they’re in a trusted relationship, whether it’s a social relationship or a financial transaction, whatever the relationship is — once you feel trusted, you feel safe, you feel protected. And you’re more likely to want to engage again in the future. I believe the best thing organizations can do is take a multilayered approach to authenticating and identifying people upfront. There are so many ways to do this digitally without disrupting the consumer, and this is the best opportunity for businesses. If we collectively get that right, we’ll stop fraud. T: What are some of the things Experian is focusing on to help businesses stop fraud? K: We’ve focused on our CrossCore® platform. CrossCore is a common access and decisioning capability platform that allows the combining and layering of many different approaches — some active, some passive — to identify a customer in a transaction. You can incorporate things like biometrics and behavioral attributes. You can incorporate digital information about the device you’re engaging with. You can layer in online and offline identity information, like that from our Precise ID® product. CrossCore also enables you to layer in other digital attributes and alternative data such as email address, phone number and the validity of that phone number. CrossCore provides a great opportunity for us to showcase innovation, whether that comes from a third-party partner or even from our own Experian DataLabs. T: How significant do you see machine learning moving forward? K: Machine learning, it has all kinds of names, right? I think of machine learning, artificial intelligence, data robotics, parallel computing — all these things are related to what we used to call big data processing, but that’s not really the trendy term anymore. The point is that there is so much data today. There’s a wealth of data from all different sources, and as a society we’re producing it in exponential volumes. Having more and more and more data is not useful if you can’t derive insights from it. That’s why machine learning, augmented with human intervention or direction, is the best way forward, because there’s so much data out there available in the world now. No matter what problem we’re trying to solve, there’s a wealth of data we can amass, but we need to make sense of it. And the way to make sense of massive amounts of data in a reasonable amount of time is by using some sort of artificial intelligence, or machine learning. We’re going to see it in all kinds of applications. We already are today. So, while I think of machine learning as a generic term, I do think it’s going to be with us for a while to quickly compute and derive meaningful insights from the massive amounts of data all around us. T: Thanks, okay. Last question, and I hope a little fun. How would you describe yourself in one word? K: Curious. T: Ah, that’s a good choice. K: I am always curious. That’s why I love living where I live. It’s why I like working in technology. I’ve always wondered how things work, how we might improve on them, what’s under the hood. Why people make the decisions they do. How does someone come up with this? I’m always curious. T: Well, thank you for the time, and congrats again on being included in the Top 100 influencers in Identity.

Experian® is honored to be an MRC Technology Award nominee. But we can’t win the MRC People’s Choice Award without your help! The annual MRC Technology Awards recognize the most elite solution providers making significant contributions in the fraud, payments and risk industries. CrossCore® is the first smart, open, plug-and-play platform for fraud and identity services. We know, and our clients agree, that it delivers a better way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. Need further convincing? Here are the top 3 reasons you should vote for CrossCore. Reason 1: common access Manage your entire fraud and identity portfolio. Start immediately by turning on Experian services through a single integration. Connect to services quickly with a common, flexible API. Reason 2: open approach Control the data being used in decisions. CrossCore supports a best-in-class approach to managing a portfolio of services that work together in any combination — including Experian solutions, third-party services and client systems — delivering the level of confidence needed for each transaction. Reason 3: workflow decisioning Act quickly and adapt to new risks with built-in strategy design and workflow capabilities. You can precisely tailor strategies based on transaction type or risk threshold. Make changes dynamically, with no downtime. We hope you’ll vote for CrossCore as a better way to manage fraud prevention and identity services.