Uncategorized

Leadership and Cybersecurity Multiple studies suggest many executives aren’t as engaged as they should be when ensuring their organizations are prepared to mitigate and manage cybersecurity risks. Insights from our Fourth Annual Data Breach Preparedness Survey, conducted by the Ponemon Institute, support this sentiment. Of the privacy, compliance and IT professionals polled: 57% said their company’s board, chairman and chief executive officer were not informed about or involved in data breach response planning. 60% have leadership who don’t want to know immediately when a material breach occurs. 66% have a board that doesn’t understand the specific cybersecurity threats their organization faces. 74% said their board isn’t willing to take ownership for successful incident response plan implementation. For organizations to protect themselves, cybersecurity professionals need to create greater engagement among the organization’s leadership. Next week, we’ll look at how they can accomplish this. If you’d like, you can jump ahead and read it now. Fourth Annual Data Breach Preparedness Survey

Did you know that 80% of all data migrations fail? Like any large project, data migration relies heavily on many variables. Successful data migration depends on attention to detail, no matter how small. Here are 3 items essential to a successful data migration: Conduct a Pre-Migration Impact Assessment to identify the necessary people, processes and technology needed. Ensure accurate, high-quality data to better streamline the migration process and optimize system functionality. Assemble the right team, including an experienced leader and business users, to ensure timely and on-budget completion. 35% of organizations plan to migrate data this year. If you’re among them, use this checklist to create the right plan, timeline, budget, and team for success.

Create a better consumer experience during the debt collection process When most people think about debt collection, unpleasant images may come to mind, like relentless phone calls or collections notices. Whatever the case may be, the collections process often ends in a less than desirable experience for consumers. And, quite frankly, it needs to change. Steve Platt, Experian’s Group President of Decision Analytics, recently spoke with American Banker regarding how banks and other financial institutions can create a better consumer experience during the debt collection process. While balancing consumer needs and managing rising delinquencies can be a complex challenge, Steve conveyed that the technology and analytics exist to simplify the process. As an industry, we’re at a point where customer acquisition costs far exceed the costs to nurture existing customers through the entire life-cycle - from application to repayment. So, suffice to say, lenders need to rethink how they engage and communicate with their customers. Technology to the rescue Luckily, we live in an era where troves and troves of data are made available every day. We just need to help lenders leverage it to its fullest extent. For example, the right data and technology can help answer questions, such as: What’s the most effective communication channel to reach a customer? When should you contact them? How often? There isn’t a one-size-fits-all approach to debt collection. Each customer is different. Each has their own unique situation. Effective debt collection is about knowing the difference between a customer who has simply forgotten to pay and those who may be struggling financially, and communicating with them accordingly. Go digital Part of knowing how to engage consumers is also understanding we live in a digital world. We perform many of our daily tasks through our mobile devices, desktops or tablets. So, it would make sense for lenders to help their customers manage their past-due accounts virtually. Imagine being able to negotiate payment dates and terms from the privacy of your own home. It just so happens that technology can make this a reality. At the end of the day, the customer needs to be at the heart of the collections strategy. Each customer needs to be communicated with on a case-by-case basis depending on their unique circumstances. The resources exist to make customers feel like individuals, rather than numbers in a spreadsheet. And the lenders that appeal to the customer’s experience will see lower charge-offs and higher customer retention.

School’s out, and graduation brings excitement, anticipation and bills. Oh, boy, here come the student loans. Are graduates ready for the bills? Even before they have a job lined up? With lots of attention from the media, I was interested in analyzing student loan debt to see if this is a true issue or just a headline grab. There’s no shortage of headlines alluding to a student loan crisis: “How student loans are crushing millennial entrepreneurialism” “Student loan debt in 2017: A $1.3 trillion crisis” “Why the student loan crisis is even worse than people think” Certainly sounds like a crisis. However, I’m a data guy, so let’s look at the data. Pulling from our data, I analyzed student loan trades for the last four years starting with outstanding debt — which grew 21 percent since 2013 to reach a high of $1.49 trillion in the fourth quarter of 2016. I then drilled down and looked at just student loan trades. Created with Highstock 5.0.7Total Number of Student Loans TradesStudent Loan Total TradesNumber of trades in millions174,961,380174,961,380182,125,450182,125,450184,229,650184,229,650181,228,130181,228,130Q4 2013Q4 2014Q4 2015Q4 2016025M50M75M100M125M150M175M200MSource: Experian (function(){ function include(script, next) {var sc=document.createElement("script");sc.src = script;sc.type="text/javascript";sc.onload=function() {if (++next < incl.length) include(incl[next], next);};document.head.appendChild(sc);}function each(a, fn){if (typeof a.forEach !== "undefined"){a.forEach(fn);}else{for (var i = 0; i < a.length; i++){if (fn) {fn(a[i]);}}}}var inc = {},incl=[]; each(document.querySelectorAll("script"), function(t) {inc[t.src.substr(0, t.src.indexOf("?"))] = 1;});each(Object.keys({"https://code.highcharts.com/stock/highstock.js":1,"https://code.highcharts.com/adapters/standalone-framework.js":1,"https://code.highcharts.com/highcharts-more.js":1,"https://code.highcharts.com/highcharts-3d.js":1,"https://code.highcharts.com/modules/data.js":1,"https://code.highcharts.com/modules/exporting.js":1,"http://code.highcharts.com/modules/funnel.js":1,"http://code.highcharts.com/modules/solid-gauge.js":1}),function (k){if (!inc[k]) {incl.push(k)}});if (incl.length > 0) { include(incl[0], 0); } function cl() {if(typeof window["Highcharts"] !== "undefined"){new Highcharts.Chart("highcharts-79eb8e0a-4aa9-404c-bc5f-7da876c38b0f", {"chart":{"type":"column","inverted":true,"polar":false,"style":{"fontFamily":"Arial","color":"#333","fontSize":"12px","fontWeight":"normal","fontStyle":"normal"}},"plotOptions":{"series":{"dataLabels":{"enabled":true},"animation":true}},"title":{"text":"Student Loan Total Trades","style":{"fontFamily":"Arial","color":"#333333","fontSize":"18px","fontWeight":"bold","fontStyle":"normal","fill":"#333333","width":"792px"}},"subtitle":{"text":"","style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal","fill":"#666666","width":"792px"}},"exporting":{},"yAxis":[{"title":{"text":"Number of trades in millions","style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal"}},"labels":{"format":""},"type":"linear"}],"xAxis":[{"title":{"style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal"},"text":""},"reversed":true,"labels":{"format":"{value:}"},"type":"linear"}],"series":[{"data":[["Total Student Loans",174961380]],"name":"Q4 2013","turboThreshold":0,"_colorIndex":0,"_symbolIndex":0},{"data":[["Total Student Loans",182125450]],"name":"Q4 2014","turboThreshold":0,"_colorIndex":1,"_symbolIndex":1},{"data":[["Total Student Loans",184229650]],"name":"Q4 2015","turboThreshold":0,"_colorIndex":2,"_symbolIndex":2},{"data":[["Total Student Loans",181228130]],"name":"Q4 2016","turboThreshold":0,"_colorIndex":3,"_symbolIndex":3}],"colors":["#26478d","#406eb3","#632678","#982881"],"legend":{"itemStyle":{"fontFamily":"Arial","color":"#333333","fontSize":"12px","fontWeight":"normal","fontStyle":"normal","cursor":"pointer"},"itemHiddenStyle":{"fontFamily":"Arial","color":"#cccccc","fontSize":"18px","fontWeight":"normal","fontStyle":"normal"},"layout":"horizontal","floating":false,"verticalAlign":"bottom","x":0,"align":"center","y":0},"credits":{"text":"Source: Experian"}});}else window.setTimeout(cl, 20);}cl();})(); Over the past four years, student loan trades grew 4 percent, but saw a slight decline between 2015 and 2016. The number of trades isn’t growing as fast as the amount of money that people need. The average balance per trade grew 17 percent to $8,210. Either people are not saving enough for college or the price of school is outpacing the amount people are saving. I shifted the data and looked at the individual consumer rather than the trade level. Created with Highstock 5.0.7Student Loan Average Balance per Trade4.044.043.933.933.893.893.853.85Q4 2013Q4 2014Q4 2015Q4 201600.511.522.533.544.5Source: Experian (function(){ function include(script, next) {var sc=document.createElement("script");sc.src = script;sc.type="text/javascript";sc.onload=function() {if (++next < incl.length) include(incl[next], next);};document.head.appendChild(sc);}function each(a, fn){if (typeof a.forEach !== "undefined"){a.forEach(fn);}else{for (var i = 0; i < a.length; i++){if (fn) {fn(a[i]);}}}}var inc = {},incl=[]; each(document.querySelectorAll("script"), function(t) {inc[t.src.substr(0, t.src.indexOf("?"))] = 1;});each(Object.keys({"https://code.highcharts.com/stock/highstock.js":1,"https://code.highcharts.com/adapters/standalone-framework.js":1,"https://code.highcharts.com/highcharts-more.js":1,"https://code.highcharts.com/highcharts-3d.js":1,"https://code.highcharts.com/modules/data.js":1,"https://code.highcharts.com/modules/exporting.js":1,"http://code.highcharts.com/modules/funnel.js":1,"http://code.highcharts.com/modules/solid-gauge.js":1}),function (k){if (!inc[k]) {incl.push(k)}});if (incl.length > 0) { include(incl[0], 0); } function cl() {if(typeof window["Highcharts"] !== "undefined"){new Highcharts.Chart("highcharts-66c10c16-1925-40d2-918f-51214e2150cf", {"chart":{"type":"column","polar":false,"style":{"fontFamily":"Arial","color":"#333","fontSize":"12px","fontWeight":"normal","fontStyle":"normal"},"inverted":true},"plotOptions":{"series":{"dataLabels":{"enabled":true},"animation":true}},"title":{"text":"Student Loan Average Number of Trades per Consumer","style":{"fontFamily":"Arial","color":"#333333","fontSize":"18px","fontWeight":"bold","fontStyle":"normal","fill":"#333333","width":"356px"}},"subtitle":{"text":"","style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal","fill":"#666666","width":"356px"}},"exporting":{},"yAxis":[{"title":{"text":"","style":{"fontFamily":"Arial","color":"#666666","fontSize":"14px","fontWeight":"normal","fontStyle":"normal"}},"type":"linear","labels":{"format":"{value}"}}],"xAxis":[{"title":{"style":{"fontFamily":"Arial","color":"#666666","fontSize":"14px","fontWeight":"normal","fontStyle":"normal"}},"type":"linear","labels":{"format":"{}"}}],"colors":["#26478d","#406eb3","#632678","#982881","#ba2f7d"],"series":[{"data":[["Average Trades per Consumer",4.04]],"name":"Q4 2013","turboThreshold":0,"_colorIndex":0},{"data":[["Average Trade per Consumer",3.93]],"name":"Q4 2014","turboThreshold":0,"_colorIndex":1},{"data":[["Average Trade per Consumer",3.89]],"name":"Q4 2015","turboThreshold":0,"_colorIndex":2},{"data":[["Average Trades per Consumer",3.85]],"name":"Q4 2016","turboThreshold":0,"_colorIndex":3}],"legend":{"floating":false,"itemStyle":{"fontFamily":"Arial","color":"#333333","fontSize":"12px","fontWeight":"bold","fontStyle":"normal","cursor":"pointer"},"itemHiddenStyle":{"fontFamily":"Arial","color":"#cccccc","fontSize":"18px","fontWeight":"normal","fontStyle":"normal"},"layout":"horizontal"},"credits":{"text":"Source: Experian"}});}else window.setTimeout(cl, 20);}cl();})(); The number of overall student loan trades per consumer is down to 3.85, a decrease of 5 percent over the last four years. This is explained by an increase in loan consolidations as well as the better planning by students so that they don’t have to take more student loans in the same year. Lastly, I looked at the average balance per consumer. This is the amount that consumers, on average, owe for their student loan trades. Created with Highstock 5.0.7Balance in thousands ($)Quarterly $USD Debt per ConsumerQ4 Student Loan TrendsAverage Student Loan Debt Balance per Consumer27,93427,93429,22629,22630,52330,52332,06132,061Q4 2013Q4 2014Q4 2015Q4 201605,00010,00015,00020,00025,00030,00035,000Source: Experian (function(){ function include(script, next) {var sc=document.createElement("script");sc.src = script;sc.type="text/javascript";sc.onload=function() {if (++next < incl.length) include(incl[next], next);};document.head.appendChild(sc);}function each(a, fn){if (typeof a.forEach !== "undefined"){a.forEach(fn);}else{for (var i = 0; i < a.length; i++){if (fn) {fn(a[i]);}}}}var inc = {},incl=[]; each(document.querySelectorAll("script"), function(t) {inc[t.src.substr(0, t.src.indexOf("?"))] = 1;});each(Object.keys({"https://code.highcharts.com/stock/highstock.js":1,"https://code.highcharts.com/adapters/standalone-framework.js":1,"https://code.highcharts.com/highcharts-more.js":1,"https://code.highcharts.com/highcharts-3d.js":1,"https://code.highcharts.com/modules/data.js":1,"https://code.highcharts.com/modules/exporting.js":1,"http://code.highcharts.com/modules/funnel.js":1,"http://code.highcharts.com/modules/solid-gauge.js":1}),function (k){if (!inc[k]) {incl.push(k)}});if (incl.length > 0) { include(incl[0], 0); } function cl() {if(typeof window["Highcharts"] !== "undefined"){Highcharts.setOptions({lang:{"thousandsSep":","}});new Highcharts.Chart("highcharts-0b893a55-8019-4f1a-9ae1-70962e668355", {"chart":{"type":"column","inverted":true,"polar":false,"style":{"fontFamily":"Arial","color":"#333","fontSize":"12px","fontWeight":"normal","fontStyle":"normal"}},"plotOptions":{"series":{"dataLabels":{"enabled":true},"animation":true}},"title":{"text":"Average Student Loan Balance per Consumer","style":{"fontFamily":"Arial","color":"#333333","fontSize":"18px","fontWeight":"bold","fontStyle":"normal","fill":"#333333","width":"308px"}},"subtitle":{"text":"","style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal","fill":"#666666","width":"792px"}},"exporting":{},"yAxis":[{"title":{"text":"Balance numbers are in thousands ($)","style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal"}},"labels":{"format":"{value:,1f}"},"reversed":false}],"xAxis":[{"title":{"style":{"fontFamily":"Arial","color":"#666666","fontSize":"16px","fontWeight":"normal","fontStyle":"normal"},"text":"Balance in thousands ($)"},"labels":{"format":"{value:}"},"type":"linear","reversed":true,"opposite":false}],"series":[{"data":[["Average Balance per Consumer",27934]],"name":"Q4 2013","turboThreshold":0,"_colorIndex":0},{"data":[["Average Balance per Consumer",29226]],"name":"Q4 2014","turboThreshold":0,"_colorIndex":1},{"data":[["Average Balance per Consumer",30523]],"name":"Q4 2015","turboThreshold":0,"_colorIndex":2},{"data":[["Average Balance per Consumer",32061]],"name":"Q4 2016","turboThreshold":0,"_colorIndex":3}],"colors":["#26478d","#406eb3","#632678","#982881"],"legend":{"itemStyle":{"fontFamily":"Arial","color":"#333333","fontSize":"12px","fontWeight":"bold","fontStyle":"normal","cursor":"pointer"},"itemHiddenStyle":{"fontFamily":"Arial","color":"#cccccc","fontSize":"18px","fontWeight":"normal","fontStyle":"normal"}},"lang":{"thousandsSep":","},"credits":{"text":"Source: Experian"}});}else window.setTimeout(cl, 20);}cl();})(); Here we see a growth of 15 percent over the last four years. At the end of 2016, the average person with a student loan balance had just over $32,000 outstanding. While this is a large increase, we should compare it with other purchases: This balance is no more than a person purchasing a brand-new car without a down payment. While we’re seeing an increase in overall outstanding debt and individual loan balances, I’m not yet agreeing that this is the crisis the media portrays. If students are educated about the debt that they’re taking out and making sure that they’re able to repay it, the student loan market is performing as it should. It’s our job to help educate students and their families about making good financial decisions. These discussions need to be had before debt is taken out, so it’s not a shock to the student upon graduation.
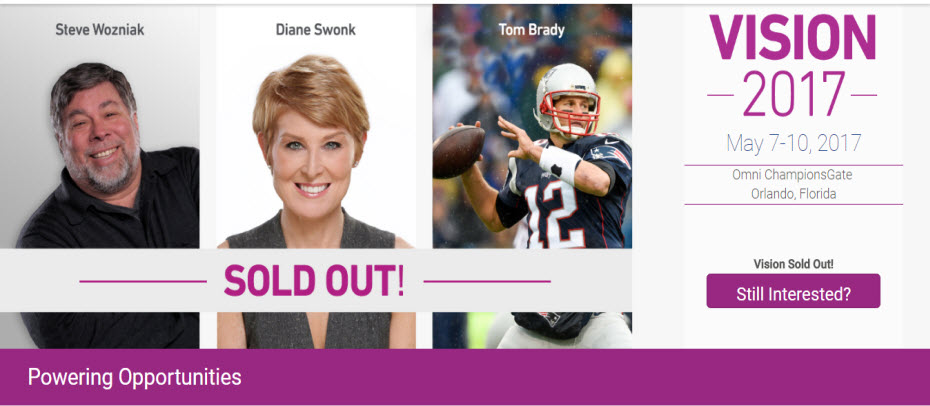
Experian’s annual Vision Conference, a four-day event designed to bring business leaders together to discuss the latest ideas and solutions surrounding targeting new markets, growing customer bases and profitability, reducing fraud and more, begins Sunday evening in Orlando, Florida. Over the course of the week, a total of 65 sessions will touch on newsworthy and breaking trends. Attendees will discover: The latest generational insights – including a first look at the coming-of-age Gen Z crowd – regarding credit scores, spend patterns and digital behaviors Multiple presentations on the economy, the mortgage market, student lending, small business forecasts and new developments in online marketplace lending Deep dives on fraud in relation to the epidemic of synthetic IDs, Know Your Customer (KYC) compliance strategies, maturing your organization to defeat fraud, and the dark web Regulatory round-ups touching on everything from the Military Lending Act (MLA), the Telephone Consumer Protection Act (TCPA), Current Expected Credit Loss (CECL) and what is emerging from the new administration Best-in-class sessions on data and analytics, modeling, virtual collections, trended data and credit marketing Intel on the state of commercial lending, the rise of the mircopreneur and the business credit profile across various life stages. Beyond a jam-packed schedule of breakout sessions, the conference will additionally host a series of general session speakers sure to educate and entertain. On Monday, Steve Wozniak, also known as “The Woz” takes the stage to talk about his experiences as co-founder of Apple Computer Inc. and his years in the emerging technology space. Diane Swonk, CEO of DS Economics, will address the crowd on Tuesday to provide details and analysis on the state of the global and U.S. economies. Finally, legendary quarterback and recent Super Bowl MVP and winner Tom Brady will speak on Wednesday to close out the event. Conference attendees can follow everything utilizing their Experian Vision app. Hot stats, pictures and event news will also be shared on multiple social handles using #ExperianVision.

There has been a lot of discussion around the auto loan market regarding delinquency rates in the past year. It is a topic Experian is asked about frequently from clients in regard to what particular economic market behaviors mean for the overall consumer lending. To understand this issue more clearly, I ran a deeper dive on the data from our Q3 Experian-Oliver Wyman Market Intelligence report. There are some interesting, and perhaps concerning, trends in the data for automotive loans and leases. Want Insights on the latest consumer credit trends? Register for our 2016 year-end review webinar. Register now Auto loan delinquency rates are at their highest mark since 2008 The findings indicate that the performance of the most recent loans opened from Q4 2015 are now performing as poorly as the loans from the credit crisis back in 2008. In fact, you have to go back to 2008, and in some cases, 2007, to see loan default rates as poorly as the Q4 2015 auto loans originated in the last year. Below we have the auto loan vintage performance for loans originated in Q4 of the last 8 years — going back to 2008. The lines on the chart each represent 60 days late or more (60+) delinquency rates over specific time period grades. For these charts, I analyzed the first three, six, and nine months from the loan origination date. As you can see, the rates of delinquency have steadily increased in recent years, with the increase in the Q4 2015 loans opened equaling or even surpassing 2008 levels. The above chart reflects all credit grades, so one might think that this change is a result of the change in the credit origination mix. By digging a little deeper into the data, we can control for the VantageScore® credit score at the loan opening, or origination date, and review performance by looking at two different score segments separately. Is there concern for Superprime and Prime consumers auto loans? In the chart immediately below, the same analysis as above has been conducted, but only for trades originated by Superprime and Prime consumers at the time of origination. You can see that although the trend is not as pronounced as when all grades are considered, even these tiers of consumers are showing significant increases in their 60+ days past due (DPD) rates in recent vintages. Separately, looking at the Subprime and Deep Subprime segments, you can really see the dramatic changes that have occurred in the performance of recent auto vintages. Holding score segments constant, the data indicates a rate of credit deterioration in the Subprime and Deep Subprime segments that we have not observed since at least 2008 — back to when we started tracking this data. What’s concerning here is not only the absolute values of the vintage delinquencies but also the trend, which is moving upward for all three time periods. Where does the risk fall? Now that we see the evidence of the deterioration of credit performance across the credit spectrum, one might ask – who is bearing the risk in these recent vintages? Taking a closer look at the chart below, you can see the significant increase in the volumes of loans across lender type, but particularly interesting to me is the increase in 2016 for the Captive Auto lenders and Credit Unions, who are hitting highs in their lending volumes in recent quarters. If the above trend holds and the trajectory continues, this suggests exposure issues for those lenders with higher volumes in recent months. What does this mean for your business? Speak to Experian's global consulting practice to learn more. Learn more Just to be thorough, let's continue and look at the relative amounts of loans going to the different score segments by each of the lender types. Comparing the lender type and the score segments (below) reveals that finance lenders have a greater than average exposure to the Subprime and Deep Subprime segments. To summarize, although auto lending has recently been viewed as a segment where loan performance is good, relative to historical levels, I believe, the above data signals a striking change in that perspective. Recent loan performance has weakened to a point where comparing the 2008 vintage with 2015 vintage, one might not be able to distinguish between the two. // <![CDATA[ var elems={'winWidth':window.innerWidth,'winTol':600,'rotTol':800,'hgtTol':1500}, updRes=function(){var xAxislabelSize=function(){if(elems.winWidth<elems.winTol){return'12px'}else{return'14px'}},xAxislabelRotation=function(){if(elems.winWidth<elems.rotTol){return-90}else{return 0}},seriesLabelSize=function(){if(elems.winWidth<elems.winTol){return'12px'}else{return'16px'}},legenLabelSize=function(){if(elems.winWidth<elems.winTol){return'12px'}else{return'16px'}},chartHeight=function(){if(elems.winWidth<elems.rotTol){return 600}else{return 400}},labelInside=function(){if(elems.winWidth<elems.rotTol){return false}else{return true}},chartStack=function(){if(elems.winWidth<elems.rotTol){return null}else{return'normal'}};this.sourceRef=function(){return['Source: Experian.com']};this.seriesColor=function(){return['#982881','#0d6eb6','#26478D','#d72b80','#575756','#b02383']};this.chartFontFamily=function(){return'"Roboto",Helvetica,Arial,sans-serif'};this.xAxislabelSize=function(){return xAxislabelSize()};this.xAxislabelOverflow=function(){return'none'};this.xAxislabelRotation=function(){return xAxislabelRotation()};this.seriesLabelSize=function(){return seriesLabelSize()};this.legenLabelSize=function(){return legenLabelSize()};this.chartHeight=function(){return chartHeight()};this.labelInside=function(){return labelInside()};this.chartStack=function(){return chartStack()}}(), updY=function(chart){var points=chart.series[0].points;for(var i=0;i elems.rotTol){if(thisWidth<20){var y=points[i].dataLabel.y;y-=10;points[i].dataLabel.css({color:'#575756'}).attr({y:y-thisWidth})}}}},updX=function(chart){var points=chart.series[0].points;for(var i=0;i elems.rotTol){if(thisWidth

How will the FinCEN revisions impact your business? (Part 1) Some recently published FinCEN revisions and advisories are causing a stir. First, let’s look at revisions to Customer Due Diligence that require compliance by May 2018. Under the updated requirements for Customer Due Diligence, covered financial institutions must expand programs, including Customer Identification Programs (CIP), to include Beneficial Owners of Legal Entity customers. Under the new rule, financial institutions must collect and verify identity information (name, address, date of birth, Social Security number or passport number for foreign individuals): For each Natural Person with at least 25% ownership in the Legal entity and For an individual with significant responsibility for managing or controlling the business — for example, a chief executive officer, a chief financial officer, a chief operating officer, a managing member, a general partner, a president, a vice president or a treasurer The U.S. Treasury estimates that illicit proceeds generated in the United States alone total $400 billion annually. These requirements are intended to prevent anonymous access to financial systems through shielded or minority ownership. While the effort to stem the tide of illicit proceeds is laudable, the impact to business may be significant. Most organizations will need to audit their data collection practices, and many will need to make changes to either data collection or workflow processes to ensure compliance. While quite simple and straightforward on paper, the standardization of additional CIP policies and procedures tend to create substantive impact to the customer experience as well as operational resource allocations and utilization. Covered financial institutions should already be discussing with their current or prospective fraud risk and identity management vendors to ensure that: There is a clear path to altering both data collection and verification of these additional identity elements. Clear and accurate benchmarking around expected verification rates is available ahead of the compliance date to allow for operational workflow design to accommodate both ‘verifications’ and ‘referrals stemming from lack of full verification.’ Service providers are granting access to best-in-class data assets and search & match logic related to identity element verification and risk assessment, along with multi-layered options to reconcile those initial verification ‘fails.’ Full business reviews and strategy design sessions are underway or being scheduled to align and document overall objectives of the program, benchmarking of leading industry practices, current and future state gaps, near- and long-term initiatives and a prioritized roadmap, a viable business case toward additional investment in services and resources, and a plan of execution. Will this impact your business? Will you need to make any changes? Click here to read part two - FinCEN and email-compromise fraud.

Prescriptive solutions: Get the Rx for your right course of action By now, everyone is familiar with the phrase “big data” and what it means. As more and more data is generated, businesses need solutions to help analyze data, determine what it means and then assist in decisioning. In the past, solutions were limited to simply describing data by creating attributes for use in decisioning. Building on that, predictive analytics experts developed models to predict behavior, whether that was a risk model for repayment, a propensity model for opening a new account or a model for other purposes. The next evolution is prescriptive solutions, which go beyond describing or predicting behaviors. Prescriptive solutions can synthesize big data, analytics, business rules and strategies into an environment that provides businesses with an optimized workflow of suggested options to reach a final decision. Be prepared — developing prescriptive solutions is not simple. In order to fully harness the value of a prescriptive solution, you must include a series of minimum capabilities: Flexibility — The solution must provide users the ability to make quick changes to strategies to adjust to market forces, allowing an organization to pivot at will to grow the business. A system that lacks agility (for instance, one that relies heavily on IT resources) will not be able to realize the full value, as its recommendations will fall behind current market needs. Expertise — Deep knowledge and a detailed understanding of complex business objectives are necessary to link overall business goals to tactical strategies and decisions made about customers. Analytics — Both descriptive and predictive analytics will play a role here. For instance, the use of a layered score approach in decisioning — what we call dimensional decisioning — can provide significant insight into a target market or customer segment. Data — It is assumed that most businesses have more data than they know what to do with. While largely true, many organizations do not have the ability to access and manage that data for use in decision-making. Data quality is only important if you can actually make full use of it. Let’s elaborate on this last point. Although not intuitive, the data you use in the decision-making process should be the limiting factor for your decisions. By that, I mean that if you get the systems, analytics and strategy components of the equation right, your limitation in making decisions should be data-driven, and not a result of another part of the decision process. If your prescriptive environment is limited by gaps in flexibility, expertise or analytic capabilities, you are not going to be able to extract maximum value from your data. With greater ability to leverage your data — what I call “prescriptive capacity” — you will have the ability to take full advantage of the data you do have. Taking big data from its source through to the execution of a decision is where prescriptive solutions are most valuable. Ultimately, for a business to lead the market and gain a competitive advantage over its competitors — those that have not been able to translate data into meaningful decisions for their business — it takes a combination of the right capabilities and a deep understanding of how to optimize the ecosystem of big data, analytics, business rules and strategies to achieve success.

We are excited to announce that Experian Fraud and Identity Solutions is presenting at FinovateFall 2016! Finovate conferences showcase cutting-edge banking and financial technology in a unique demo-only format. Held twice a year, the conferences bring together the leaders from top financial institutions, fintech companies, investors from around the globe, and fintech media to share and promote the most innovative financial technology solutions. "Experian’s Fraud and Identity Solutions is a leader in customer-centric identity and fraud solutions, providing fraud management solutions to some of the world’s largest brands in financial services, insurance, and retail," said Adam Fingersh, general manager and senior vice president of Fraud and Identity Solutions in North America. "We will introduce our Fraud and Identity Solutions and promote our newly released CrossCore platform. CrossCore puts more control in the hands of fraud teams to adapt and deploy strategies that keep up with the pace of fraud while reducing burdens on IT and data science teams." Fingersh and John Sarreal, senior director of Fraud and Identity product management at Experian, are presenting the 7-minute demo focusing on the key CrossCore capabilities, and how CrossCore manages fraud and identity services through its flexible API; open, plug-and-play platform; and powerful workflow and strategy design capabilities. In Forrester’s 2016 “Vendor Landscape: Mobile Fraud Management”, Experian Fraud and Identity Solutions was cited as having the most capabilities and one of the highest estimated revenues in total fraud management in the market, between $200 million and $250 million. Join us for the event on September 8-9 in New York. Experian also has an exclusive 20% off discount code (Experian20FF16) to get even more savings! For more information on the event or to view videos of previous demos, please visit finovate.com.

Is the speed of fraud threatening your business? Like many other fraud and compliance teams, your teams may be struggling to keep up with new business dynamics. The following trends are changing the way consumers do business with you: 35 percent year-over-year growth in mobile commerce More than $27 billion forecasted value of mobile payment transactions in 2016 45 percent of smartphone owners using a mobile device to make a purchase every month More than 1 billion mobile phone owners will use their devices for banking purposes by the end of 2015 In an attempt to stay ahead of fraud, systems have become more complex, more expensive and even more difficult to manage, leading to more friction for your customers. How extensive is this impact? 30 percent of online customers are interrupted to catch one fraudulent attempt One in 10 new applicants may be an imposter using breached data $40 billion of legitimate customer sales are declined annually because of tight rules, processes, etc. This rapid growth only reinforces the need for aggressive fraud prevention strategies and adoption of new technologies to prepare for the latest emerging cybersecurity threats. Businesses must continue their efforts to protect all parties’ interests. Fraudsters have what they need to be flexible and quick. So why shouldn’t businesses? Introducing CrossCore™, the first smart plug-and-play platform for fraud and identity services. CrossCore uses a single access point to integrate technology from different providers to address different dangers. When all your fraud and identity solutions work together through a single application program interface, you reduce friction and false positives — meaning more growth for your business. View our recent infographic on global fraud trends

Part four in our series on Insights from Vision 2016 fraud and identity track It was a true honor to present alongside Experian fraud consultant Chris Danese and Barbara Simcox of Turnkey Risk Solutions in the synthetic and first-party fraud session at Vision 2016. Chris and Barbara, two individuals who have been fighting fraud for more than 25 years, kicked off the session with their definition of first-party versus third-party fraud trends and shared an actual case study of a first-party fraud scheme. The combination of the qualitative case study overlaid with quantitative data mining and link analysis debunked many myths surrounding the identification of first-party fraud and emphasized best practices for confidently differentiating first-party, first-pay-default and synthetic fraud schemes. Following these two passionate fraud fighters was a bit intimidating, but I was excited to discuss the different attributes included in first-party fraud models and how they can be impacted by the types of data going into the specific model. There were two big “takeaways” from this session for me and many others in the room. First, it is essential to use the correct analytical tools to find and manage true first-party fraud risk successfully. Using a credit score to identify true fraud risk categorically underperforms. BustOut ScoreSM or other fraud risk scores have a much higher ability to assess true fraud risk. Second is the need to for a uniform first-party fraud bust-out definition so information can be better shared. By the end of the session, I was struck by how much diversity there is among institutions and their approach to combating fraud. From capturing losses to working cases, the approaches were as unique as the individuals in attendance This session was both educational and inspirational. I am optimistic about the future and look forward to seeing how our clients continue to fight first-party fraud.

On June 2, the Consumer Financial Protection Bureau (CFPB) proposed a rule aimed at “payday lending” that will apply to virtually all lenders, with request for comments by Sept. 14. Here is a summary of the basic provisions of the proposed rule. However, with comments, the proposal is more than 1,300 pages in length, and the proposed rule and examples are more than 200 pages long. It is necessary to review the details of the proposed rule to understand its potential impact on your products and processes fully. You may wish to review your current and future offerings with your institution’s counsel and compliance officer to determine the potential impact if major provisions of this proposed rule are finalized by the CFPB. Coverage The proposal generally would cover two categories of loans. First, the proposal generally would cover loans with a term of 45 days or less. Second, the proposal generally would cover loans with a term greater than 45 days, provided that they have an all-in annual percentage rate greater than 36 percent and either are repaid directly from the consumer’s account or income or are secured by the consumer’s vehicle. Ability to repay For both categories of covered loans, the proposal would identify it as an abusive and unfair practice for a lender to make a covered loan without reasonably determining that the consumer has the ability to repay the loan. Or if the lender does not determine if the consumer can make payments due, as well as meet major financial obligations and basic living expenses during and for 30 days after repayment. Lenders would be required to verify the amount of income that a consumer receives, after taxes, from employment, government benefits or other sources. In addition, lenders would be required to check a consumer’s credit report to verify the amount of outstanding loans and required payments. “Safe Harbor” The proposed rule would provide lenders with options to make covered loans without satisfying the ability-to-repay and payment notice requirements, if those loans meet certain conditions. The first option would be offering loans that generally meet the parameters of the National Credit Union Administration “payday alternative loans” program, where interest rates are capped at 28 percent and the application fee is no more than $20. The other option would be offering loans that are payable in roughly equal payments with terms not to exceed two years and with an all-in cost of 36 percent or less, not including a reasonable origination fee, so long as the lender’s projected default rate on these loans is 5 percent or less. The lender would have to refund the origination fees any year that the default rate exceeds 5 percent. Lenders would be limited as to how many of either type of loan they could make per consumer per year. Outstanding loans The proposal also would impose certain restrictions on making covered loans when a consumer has — or recently had — certain outstanding loans. These provisions are extensive and differ between short- and long-term loans. For example: Payday and single-payment auto title: If a borrower seeks to roll over a loan or returns within 30 days after paying off a previous short-term debt, the lender would be restricted from offering a similar loan. Lenders could only offer a similar short-term loan if a borrower demonstrated that their financial situation during the term of the new loan would be materially improved relative to what it was since the prior loan was made. The same test would apply if the consumer sought a third loan. Even if a borrower’s finances improved enough for a lender to justify making a second and third loan, loans would be capped at three in succession followed by a mandatory 30-day cooling-off period. High-cost installment loans: For consumers struggling to make payments under either a payday installment or auto title installment loan, lenders could not refinance the loan into a loan with similar payments. This is unless a borrower demonstrated that their financial situation during the term of the new loan would be materially improved relative to what it was during the prior 30 days. The lender could offer to refinance if that would result in substantially smaller payments or would substantially lower the total cost of the consumer’s credit. Payments Furthermore, it would be defined as an unfair and abusive practice to attempt to withdraw payment from a consumer’s account for a covered loan after two consecutive payment attempts have failed, unless the lender obtains the consumer’s new and specific authorization to make further withdrawals from the account. The proposal would require lenders to provide certain notices to the consumer before attempting to withdraw payment for a covered loan from the consumer’s account unless exempt under one of the “safe harbor” options. Registered information systems Finally, the proposed rule would require lenders to use credit reporting systems to report and obtain information about loans made under the full-payment test or the principal payoff option. These systems would be considered consumer reporting companies, subject to applicable federal laws and registered with the CFPB. Lenders would be required to report basic loan information and updates to that information. The proposed regulation may be found here.

Industry’s first smart plug-and-play fraud platform allows companies to connect their own solutions, Experian products and third-party vendors in one place to better protect their customers from fraud threats Experian unveiled the fraud and identity industry’s first open platform designed to catch fraud faster, improve compliance and enhance the customer experience. Experian’s CrossCore™ gives companies an easier way to connect any new or existing tools and systems in one place, whether they are Experian, internal or third-party partner solutions. This “plug-and-play” capability allows companies to rapidly adapt to changing conditions and risks. “Our clients have expressed frustration over the lack of a truly holistic industry solution that delivers the level of confidence and control they need without requiring a massive multiyear project to replace everything they have,” said Steve Platt, global executive vice president, Fraud and Identity, Experian. “New fraud threats, updates to regulatory requirements and customer expectations for a hassle-free experience are making it challenging for fraud and compliance teams to keep up. CrossCore will give them the flexibility they need to balance customer protection with customer experience.” The CrossCore open platform enables organizations to manage services through a common access point that supports a layered approach to managing risks across providers. CrossCore includes powerful workflow and strategy design capabilities that allow fraud and compliance teams to create and adapt strategies based on evolving threats and business needs. This helps them to respond more quickly and reduces the burden on IT. Fraud and compliance teams must constantly respond to new fraud threats and changing regulatory requirements by implementing new tools on top of existing solutions. “A layered approach is imperative, because fraudsters can break through each layer individually, but they will face greater barriers with each additional layer imposed,” said Avivah Litan, vice president and distinguished analyst, Security and Privacy, of Gartner.[1] Over time, as layers have been added and fortified, systems have become increasingly complex, expensive to integrate and difficult to manage, often increasing customer friction. A key feature of the CrossCore fraud platform is the ease of integration with third-party partner solutions. At launch, CrossCore will support fraud and identity services provided by third-party partners, including Acxiom® (Identity Solutions), TeleSign and many others already integrated with Experian solutions, with more being added to the platform. Previously, integrating third-party solutions required tremendous time and effort, which often challenged in-house teams to execute in a timely, efficient manner. Through CrossCore, the responsibility of integrating additional tools and systems moves away from those teams to the platform itself, enabling clients to select best-in-class solutions from multiple providers without creating a strain on resources. Al Pascual, senior vice president, research director and head of fraud & security for Javelin, said, “There are so many great niche solutions to work with, and new ones come out almost every day. To really have a world-class approach, the client has to put all those little things together, because there never will be one vendor who does it all. The market challenge is about how to make it faster and easier to bring things together to enable a more dynamic and fluid approach to managing risk.” CrossCore features Common access through a flexible API connects disparate systems to improve risk controls while reducing integration cost and complexity An open approach enables clients to connect and optimize a portfolio of best-in-class solutions across Experian, third-party services and existing systems Powerful strategy design and workflow decisioning functions enable fraud and compliance teams to apply services in any combination to get the level of confidence required A modern Software as a Service (SaaS) architecture provides scalability and the ability to make strategy changes dynamically with no down time Experian, which offers fraud and identity services in more than 44 countries, developed CrossCore to address the widespread market need consistently expressed by its clients for a faster, easier way to get more out of their existing systems and add new tools to improve their customers’ experience while minimizing risk. Companies can begin accessing CrossCore immediately, with the ability to turn on Experian services through a single integration, connect their own fraud and identity capabilities with a common API and turn on new services as they are added. The initial release includes key Experian products: FraudNet for Account Opening; Hunter®, for application fraud detection; Prove-ID, for international identity verification; and Precise ID®, for U.S. identity verification, including knowledge-based authentication. (KBA). Third-party fraud and identity service providers can engage with CrossCore to connect their services. “Now, companies can implement a new approach to managing fraud and identity services — one that will give them greater control over their risk exposure and enable them to provide a safer and more enjoyable experience for their customers,” added Platt. Learn more about CrossCore at https://www.experian.com/crosscore [1]Gartner, Identity Proofing Revisited as Data Confidentiality Dies, Avivah Litan, Dec. 12, 2013; last reviewed on April 28, 2015

James W. Paulsen, Chief Investment Strategist for Wells Capital Management, kicked off the second day of Experian’s Vision 2016, sharing his perspective on the state of the economy and what the future holds for consumers and businesses alike. Paulsen joked this has been “the most successful, disappointing recovery we’ve ever had.” While media and lenders project fear for a coming recession, Paulsen stated it is important to note we are in the 8th year of recovery in the U.S., the third longest in U.S. history, with all signs pointing to this recovery extending for years to come. Based on his indicators – leverage, restored household strength, housing, capital spending and better global growth – there is still capacity to grow. He places recession risk at 20 to 25 percent – and only quotes those numbers due the length of the recovery thus far. “What is the fascination with crisis policies when there is no crisis,” asks Paulsen. “I think we have a good chance of being in the longest recovery in U.S. history.” Other noteworthy topics of the day: Fraud prevention Fraud prevention continues to be a hot topic at this year’s conference. Whether it’s looking at current fraud challenges, such as call-center fraud, or looking to future-proof an organization’s fraud prevention techniques, the need for flexible and innovative strategies is clear. With fraudsters being quick, and regularly ahead of the technology fighting them, the need to easily implement new tools is fundamental for you to protect your businesses and customers. More on Regulatory The Military Lending Act has been enhanced over the past year to strengthen protections for military consumers, and lenders must be ready to meet updated regulations by fall 2016. With 1.46 million active personnel in the U.S., all lenders are working to update processes and documentation associated with how they serve this audience. Alternative Data What is it? How can it be used? And most importantly, can this data predict a consumer’s credit worthiness? Experian is an advocate for getting more entities to report different types of credit data including utility payments, mobile phone data, rental payments and cable payments. Additionally, alternative data can be sourced from prepaid data, liquid assets, full file public records, DDA data, bill payment, check cashing, education data, payroll data and subscription data. Collectively, lenders desire to assess someone’s stability, ability to pay and willingness to repay. If alternative data can answer those questions, it should be considered in order to score more of the U.S. population. Financial Health The Center for Financial Services Innovation revealed insights into the state of American’s financial health. According to a study they conducted, 57 percent of Americans are not financially healthy, which equates to about 138 million people. As they continue to place more metrics around defining financial health, the center has landed on four components: how people plan, spend, save and borrow. And if you think income is a primary factor, think again. One-third of Americans making more than $60k a year are not healthy, while one-third making less than $60k a year are healthy. --- Final Vision 2016 breakouts, as well as a keynote from entertainer Jay Leno, will be delivered on Wednesday.

It’s impossible to capture all of the insights and learnings of 36 breakout sessions and several keynote addresses in one post, but let’s summarize a few of the highlights from the first day of Vision 2016. 1. Who better to speak about the state of our country, specifically some of the threats we are facing than Leon Panetta, former Secretary of Defense and Director of the CIA. While we are at a critical crossroads in the United States, there is room for optimism and his hope that we can be an America in Renaissance. 2. Alex Lintner, Experian President of Consumer Information Services, conveyed how the consumer world has evolved, in large part due to technology: 67 percent of consumers made purchases across multiple channels in the last six months. More than 88M U.S. consumers use their smartphone to do some form of banking. 68 percent of Millennials believe within five years the way we access money will be totally different. 3. Peter Renton of Lend Academy spoke on the future of Online Marketplace Lending, revealing: Banks are recognizing that this industry provides them with a great opportunity and many are partnering with Online Marketplace Lenders to enter the space. Millennials are not the largest consumers in this space today, but they will be in the future. Sustained growth will be key for this industry. The largest platforms have everything they need in place to endure – even through an economic downturn.In other words, Online Marketplace Lenders are here to stay. 4. Tom King, Experian’s Chief Information Security Officer, addressed the crowds on how the world of information security is growing increasingly complex. There are 1.9 million records compromised every day, and sadly that number is expected to rise. What can businesses do? “We need to make it easier to make the bad guys go somewhere else,” says King. 5. Look at how the housing market has changed from just a few years ago: Inventory continues to be extraordinarily lean. Why? New home building continues to run at recession levels. And, 8.5 percent of homeowners are still underwater on their mortgage, preventing them from placing it on the market. In the world of single-family home originations, 2016 projections show that there will be more purchases, less refinancing and less volume. We may see further growth in HELOC’s. With a dwindling number of mortgages benefiting from refinancing, and with rising interest rates, a HELOC may potentially be the cheapest and easiest way to tap equity. 6. As organizations balance business needs with increasing fraud threats, the important thing to remember is that the customer experience will trump everything else. Top fraud threats in 2015 included: Card Not Present (CNP) First Party Fraud/Synthetic ID Application Fraud Mobile Payment/Deposit Fraud Cross-Channel FraudSo what do the experts believe is essential to fraud prevention in the future? Big Data with smart analytics. 7. The need for Identity Relationship Management can be seen by the dichotomy of “99 percent of companies think having a clear picture of their customers is important for their business; yet only 24 percent actually think they achieve this ideal.” Connecting identities throughout the customer lifecycle is critical to bridging this gap. 8. New technologies continue to bring new challenges to fraud prevention. We’ve seen that post-EMV fraud is moving “upstream” as fraudsters: Apply for new credit cards using stolen ID’s. Provision stolen cards into mobile wallet. Gain access to accounts to make purchases.Then, fraudsters are open to use these new cards everywhere. 9. Several speakers addressed the ever-changing regulatory environment. The Telephone Consumer Protection Act (TCPA) litigation is up 30 percent since the last year. Regulators are increasingly taking notice of Online Marketplace Lenders. It’s critical to consider regulatory requirements when building risk models and implementing business policies. 10. Hispanics and Millennials are a force to be reckoned with, so pay attention: Millennials will be 81 million strong by 2036, and Hispanics are projected to be 133 million strong by 2050. Significant factors for home purchase likelihood for both groups include VantageScore® credit score, age, student debt, credit card debt, auto loans, income, marital status and housing prices. More great insights from Vision coming your way tomorrow!