Tag: Data Breach

Data breaches continue to be a reality for organizations across industries, and the complexity of responding to them is only increasing. From AI-driven fraud to third-party exposures, the risk landscape is shifting fast. Having a modern and tested response plan is essential to containing the damage, protecting your customers, and preserving your organization’s reputation when a breach occurs. Experian’s eleventh annual Data Breach Response Guide draws on decades of breach support experience. It offers practical strategies and insights for navigating the moments that matter most: the first hours after a breach and the days that follow. The 2025–2026 guide explores: How AI is shaping new breach and fraud patterns Where organizations are most vulnerable, including third-party and supply chain weak points Consumer expectations and how they influence crisis response How prepared organizations are reducing impact and protecting trust What is required to build a modern, effective breach response plan Organizations with a tested plan can potentially reduce the cost, impact, and long-term consequences of a breach. From real-world case insights to crisis communication templates, this guide is designed to help teams act quickly and confidently. Download the 2025–2026 Data Breach Response Guide to learn how you can strengthen your breach preparedness, reduce risk exposure, and build resilience against the next wave of cybersecurity threats. Download guide

As data breaches become an ever-growing threat to businesses, the role of employees in maintaining cybersecurity has never been more critical. Did you know that 82% of data breaches involve the human element1 , such as phishing, stolen credentials, or social engineering tactics? These statistics reveal a direct connection between employee identity theft and business vulnerabilities. In this blog, we’ll explore why protecting your employees’ identities is essential to reducing data breach risk, how employee-focused identity protection programs, and specifically employee identity protection, improve both cybersecurity and employee engagement, and how businesses can implement comprehensive solutions to safeguard sensitive data and enhance overall workforce well-being. The Rising Challenge: Data Breaches and Employee Identity Theft The past few years have seen an exponential rise in data breaches. According to the Identity Theft Resource Center, there were 1,571 data compromises in the first half of 2024, impacting more than 1.1 billion individuals – a 490% increase year over year2. A staggering proportion of these breaches originated from compromised employee credentials or phishing attacks. Explore Experian's Employee Benefits Solutions The Link Between Employee Identity Theft and Cybersecurity Risks Phishing and Social EngineeringPhishing attacks remain one of the top strategies used by cybercriminals. These attacks often target employees by exploiting personal information stolen through identity theft. For example, a cybercriminal who gains access to an employee's compromised email or social accounts can use this information to craft realistic phishing messages, tricking them into divulging sensitive company credentials. Compromised Credentials as Entry PointsCompromised employee credentials were responsible for 16% of breaches and were the costliest attack vector, averaging $4.5 million per breach3. When an employee’s identity is stolen, it can give hackers a direct line to your company’s network, jeopardizing sensitive data and infrastructure. The Cost of DowntimeBeyond the financial impact, data breaches disrupt operations, erode customer trust, and harm your brand. For businesses, the average downtime from a breach can last several weeks – time that could otherwise be spent growing revenue and serving clients. Why Businesses Need to Prioritize Employee Identity Protection Protecting employee identities isn’t just a personal benefit – it’s a strategic business decision. Here are three reasons why identity protection for employees is essential to your cybersecurity strategy: 1. Mitigate Human Risk in Cybersecurity Employee mistakes, often resulting from phishing scams or misuse of credentials, are a leading cause of breaches. By equipping employees with identity protection services, businesses can significantly reduce the likelihood of stolen information being exploited by fraudsters and cybercriminals. 2. Boost Employee Engagement and Financial Wellness Providing identity protection as part of an employee benefits package signals that you value your workforce’s security and well-being. Beyond cybersecurity, offering such protections can enhance employee loyalty, reduce stress, and improve productivity. Employers who pair identity protection with financial wellness tools can empower employees to monitor their credit, secure their finances, and protect against fraud, all of which contribute to a more engaged workforce. 3. Enhance Your Brand Reputation A company’s cybersecurity practices are increasingly scrutinized by customers, stakeholders, and regulators. When you demonstrate that you prioritize not just protecting your business, but also safeguarding your employees’ identities, you position your brand as a leader in security and trustworthiness. Practical Strategies to Protect Employee Identities and Reduce Data Breach Risk How can businesses take actionable steps to mitigate risks and protect their employees? Here are some best practices: Offer Comprehensive Identity Protection Solutions A robust identity protection program should include: Real-time monitoring for identity theft Alerts for suspicious activity on personal accounts Data and device protection to protect personal information and devices from identity theft, hacking and other online threats Fraud resolution services for affected employees Credit monitoring and financial wellness tools Leading providers like Experian offer customizable employee benefits packages that provide proactive identity protection, empowering employees to detect and resolve potential risks before they escalate. Invest in Employee Education and Training Cybersecurity is only as strong as your least-informed employee. Provide regular training sessions and provide resources to help employees recognize phishing scams, understand the importance of password hygiene, and learn how to avoid oversharing personal data online. Implement Multi-Factor Authentication (MFA) MFA adds an extra layer of security, requiring employees to verify their identity using multiple credentials before accessing sensitive systems. This can drastically reduce the risk of compromised credentials being misused. Partner with a Trusted Identity Protection Provider Experian’s suite of employee benefits solutions combines identity protection with financial wellness tools, helping your employees stay secure while also boosting their financial confidence. Only Experian can offer these integrated solutions with unparalleled expertise in both identity protection and credit monitoring. Conclusion: Identity Protection is the Cornerstone of Cybersecurity The rising tide of data breaches means that businesses can no longer afford to overlook the role of employee identity in cybersecurity. By prioritizing identity protection for employees, organizations can reduce the risk of costly breaches and also create a safer, more engaged, and financially secure workforce. Ready to protect your employees and your business? Take the next step toward safeguarding your company’s future. Learn more about Experian’s employee benefits solutions to see how identity protection and financial wellness tools can transform your workplace security and employee engagement. Learn more 1 2024 Experian Data Breach Response Guide 2 Identity Theft Resource Center. H1 2024 Data Breach Analysis 3 2023 IBM Cost of a Data Breach Report

With cyber threats intensifying and data breaches rising, understanding how to respond to incidents is more important than ever. In this interview, Michael Bruemmer, Head of Global Data Breach Resolution at Experian, is joined by Matthew Meade, Chair of the Cybersecurity, Data Protection & Privacy Group at Eckert Seamans, to discuss the realities of data breach response. Their session, “Cyber Incident Response: A View from the Trenches,” brings insights from the field and offers a preview of Experian's 2025 Data Breach Industry Forecast, including the role of generative artificial intelligence (AI) in data breaches. From the surge in business email compromises (BEC) to the relentless threat of ransomware, Bruemmer and Meade dive into key issues facing organizations big and small today. Drawing from Experian's experience handling nearly 5,000 breaches this year, Bruemmer sheds light on effective response practices and reveals common pitfalls. Meade, who served as editor-in-chief for the Sedona Conference’s new Model Data Breach Notification Law, explains the implications of these regulatory updates for organizations and highlights how standardized notification practices can improve outcomes. Bruemmer and Meade’s insights offer a proactive guide to tackling tomorrow’s cyber threats, making it a must-listen for anyone aiming to stay one step ahead. Listen to the full interview for a valuable look at both the current landscape and what's next. Click here for more insight into safeguarding your organization from emerging cyber threats.
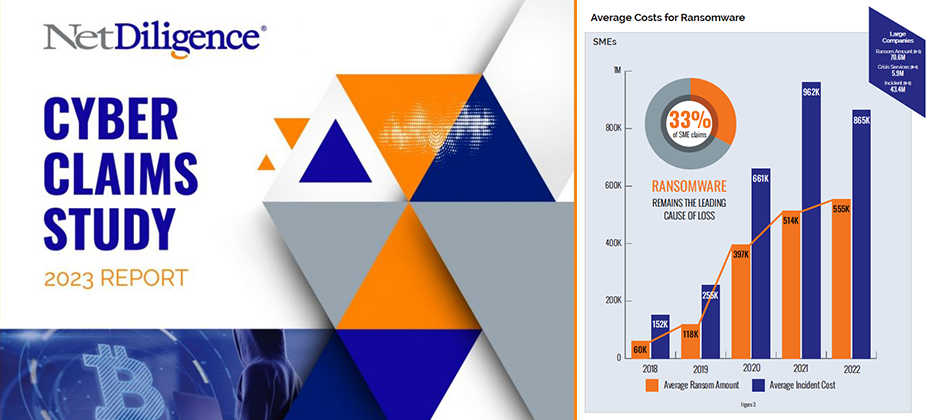
Review of Findings & Front-line Insights Panel Participants: Richard Goldberg (Moderator) – Constangy, Brooks, Smith & Prophete, LLP Michael Bruemmer – Experian Sean Renshw – RSM US, LLP Mark Greisiger – NetDiligence About NetDiligence Cyber Claims Study It is NetDiligence’s 13th year of doing this Cyber Claims Study. A total of 9,028 claims were analyzed during the past five years 2018-2022.An observation from the over 9,000 Cyber Claims (5000 of which are brand new claims this past year in 2023) analyzed is while many of the categories over the last five years have remained the same, the data has changed, sometimes dramatically. About Experian We provide call center coverage, notification coverage, as well as, identity theft protection, and all the consumer resolutions that go along with it for about 5000 data breaches every year, and I was delighted to be on the panel. Key Insights Experian has proudly sponsored the annual NetDiligence Cyber Claims Study for three years. During this time, I’ve witnessed companies adapt and transform their operations to confront the growing tide of cyber threats. The evolution of their infrastructure to anticipate and respond to these challenges has been remarkable and necessary. However, despite my front-row seat in this fast-changing landscape, the results of each study never fail to surprise and intrigue me. The insights from the latest study, conducted in 2023, continue to shape our understanding of the evolving cyber landscape. Ransomware’s Dominance Mark kicked off the discussion by shedding light on the escalating costs associated with cyber incidents. In 2022, the average incident cost for SME organizations remained stable at $169,000 (similar to the combined five-year window from 2018 to 2022 at about 175,000). However, there was a substantial increase for large companies, reaching $20.3 million in 2022 (and if you look at the five-year average, it was about 13 million). This surge raised eyebrows and set the stage for a deep dive into ransomware, a leading cause of concern. Examining Ransomware Trends The conversation swiftly shifted to ransomware, a pervasive threat in the cyber insurance landscape. As I stated, at Experian we see a correlation between the rise in ransomware and third-party breaches. Most of the industry experts on the panel participate in a Ransomware Advisory Group together. Mark brought up a good insight from our advisory group on the brazen tactics employed by threat actors lately, showcasing their intimate knowledge of the cyber insurance world. Business Sectors Under Siege Richard and Sean added to the discussion the top ten business sectors affected by ransomware, with professional services leading the pack. The impact on technology, with a payout of $830,000, stood out as well. Beyond Ransomware The conversation broadened to encompass other types of losses, such as social engineering and business email compromise. The focus on business interruption emerged as a key concern for cyber insurance claims, with the industry grappling with criminal acts versus non-criminal acts. Looking Ahead As the discussion unfolded, industry experts, including myself, expressed eagerness to anticipate the future cyber landscape. Predictions range from the industry mutating to the emergence of new players in the nation-state game. The role of artificial intelligence and innovative solutions from new vendors becomes a focal point of interest. In conclusion, the NetDiligence Cyber Claims Study 2023 Report paints a vivid picture of the challenges and transformations within the cyber insurance domain. The increasing sophistication of threat actors, coupled with evolving business strategies, sets the stage for continuous adaptation and innovation in the fight against cyber threats. As we look ahead, the resilience of businesses and the collaboration between industry stakeholders will play a pivotal role in shaping the cybersecurity landscape. I invite you to access the report and view the discussion replay for a deeper understanding of the challenges and transformations within the cyber insurance claims domain. Get NetDiligece Cyber Claims Study resources on-demand now! Download the report Watch the webinar NetDiligence’s latest Cyber Claims Study and Webinar, sponsored by Experian Data Breach, is available on-demand. This report serves as a resounding call to action, prompting businesses to ready themselves against cyber threats. Dive in to get insights and stay one step ahead of cyber adversaries.

Insights from the Cyber Risk Summit Beverly Hills – October 2023 Authored by Ryan Coyne I recently participated in a panel with industry experts, delving into third-party cyber risks. The panel shed light on best practices, challenges, and strategies to mitigate the impact of third-party incidents. Panel Participants: Stu Panensky (Moderator) – FisherBroyles, LLP Ryan Coyne – Experian Tom Egglestone – Resilience Mark Grazman – Fenix24 Matthew Saidel – FTI Consulting Agenda: Incident Best Practices: Collaboration & Coordination on IR Action Items Upstream Risk of Third Parties: Vendors, Suppliers & Business Partners Downstream Risk in the Policyholder Supply Chain The Cyber Risk Summit held in Beverly Hills provided valuable insights into the risks of engaging unsecured third parties. Key Takeaways Understanding the Significance Tom emphasized the longstanding nature of cyber risk exposure tied to third-party relationships. The increasing reliance on external vendors in a tech-enabled world has heightened this risk, especially with the surge in outsourcing and software adoption. Tom highlighted that, even in 2019, Gartner research indicated that 60% of surveyed companies worked with over 1000 third parties in their supply chain, setting the stage for the escalated risk environment post-pandemic. Crisis Communications in Third-Party Incidents Matt shared insights into the challenges faced when third-party incidents unfold. The necessity of involving crisis communications consultants early in the process, especially for upstream and downstream, was stressed. Preserving the right to operate and maintaining client trust amid incidents were key points Matt made.Hands-On Restoration PerspectiveMark, providing a hands-on restoration perspective, discussed the rarity of involvement at the inception of an event. His emphasis on locking down infrastructure, understanding the threat actor’s persistency, and encouraging robust backup strategies showcased the intricacies involved in restoration efforts.“Restoration efforts often kick in when patient zero is unidentified. Locking down the infrastructure and focusing on repairing affected elements are essential” – Mark Grazman, Fenix24 Notification Strategies and Legal Implications Representing Experian, I shared my perspective on notification complexities that the average consumer may not be aware of, such as notifying everyone upfront versus opt-in processes. The legal implications of notifying on behalf of others and coordinating with multiple parties. The nuanced approach to call center communication and the crucial factor of making details clear in notification letters in minimizing confusion for recipients.I want to emphasize a point I made earlier in the panel on the downstream impact of notification strategies and the need to customize communication for recipients.“For these incidents, it’s most important to minimize complexity on the notification side and minimize confusion for the recipient of your notification letter.” – Ryan Coyne, Experian Insights from an Insurance Claims Handler Tom, as an insurance claims handler, underscored the importance of understanding vendor contracts, particularly clauses related to defense and indemnity. He highlighted the need for transparency in the vendor’s incident response process, especially when the insured isn’t in control, adding a layer of complexity to communication and expectation setting. Crafting a Seamless Notification Process: Public-Private Partnerships Stu Panensky, Moderator: Public-private partnerships emerged as a recurring theme during the panel discussions. The need for collaboration between law enforcement, insurance companies, and businesses became evident. Stu emphasized the role of public-private partnerships in influencing better outcomes and impacting data protection, regulation, and litigation. The insights from the 2023 Beverly Hills Cyber Risk Summit underline the interconnected nature of cyber risks and the critical importance of proactive measures. Stakeholders are urged to adopt a collaborative approach, navigate legal complexities, and stay vigilant in the face of evolving challenges. I welcome you to watch the full discussion on-demand. Watch the panel session on-demand now
In the fast-paced world of cybersecurity, the ability to anticipate and adapt to emerging threats is not just a competitive advantage—it’s a business imperative. As we release our 11th annual “Experian 2024 Data Breach Industry Forecast,” we invite you to embark on a journey into the future of data breaches, a journey that promises to empower data breach professionals, cyber experts, and industry leaders alike. A Glimpse into Tomorrow’s Threat Landscape Our team of experts has meticulously examined the current cybersecurity landscape to identify the trends that will shape the industry in the coming year. The “Experian 2024 Data Breach Industry Forecast” provides a roadmap for staying ahead of these challenges, arming you with the insights needed to fortify your organization’s defenses. Six Pivotal Predictions: Decoding the Future Within the report, we unveil six pivotal predictions that promise to redefine the landscape of data breaches. While we can’t reveal all the details here, we’ll offer a sneak peek to whet your appetite: Six Degrees of Separation: There’s no question that third-party data breaches this year made headlines. Delve into the intricacies of supply chain security and discover why addressing vulnerabilities in the supply chain is the next frontier in cybersecurity. Little by Little Becomes A Lot: When trying to achieve a goal, it’s said that taking small steps can lead to big results. See how hackers could apply that same rule. Not a Third Wheel: It’s widely known who the main players are globally that sponsor attacks and a new country in South Asia may join the international stage. No, not Mother Earth! Plutonium, terbium, silicon wafers — these rare earth materials present an intriguing opportunity for hackers looking to disrupt an enemy’s economy. The Scarface Effect: Like drug cartels, cybergangs are forming sophisticated organizations. Winning from the Inside: In 2024, we may see enterprising threat actors target more publicly traded companies, leveraging data extraction and their talents in plain sight as everyday investors. This is just a glimpse into the dynamic and evolving landscape detailed in our full report. Download the complete “Experian 2024 Data Breach Industry Forecast” to explore these predictions in-depth and stay ahead of the curve. Expert Analysis: Navigating Complexity with Confidence Backed by extensive research and the expertise of our seasoned analysts, the report provides more than just predictions; it offers a deep dive into the complexities of the modern cybersecurity landscape. Our experts share their insights on how these predictions will impact organizations and individuals, providing actionable intelligence that goes beyond the theoretical. Whether you’re a CISO, a Compliance Officer, or a Cyber Risk Insurer, the “Experian 2024 Data Breach Industry Forecast” equips you to navigate the challenges of tomorrow with confidence. Empowering You to Lead in Data Breach Response As you read through the report, you’ll find that our approach goes beyond merely highlighting problems; we provide solutions. Each prediction is accompanied by practical recommendations and best practices, ensuring that you not only understand the evolving landscape but also possess the tools to proactively address the challenges that lie ahead.Now, more than ever, it’s crucial to be proactive in your approach to cybersecurity. Download the full “Experian 2024 Data Breach Industry Forecast” to unlock the insights and strategies that will set you apart in the realm of data breach response. Your journey into the future starts here. The Future is Now. Are you ready to take the first step toward a more secure tomorrow? Download the report now and lead the way in data breach response. Read more

The threat of data breach is constant in our modern, digital world. And as technology advances, so do the strategies and tactics of malicious actors seeking ways to monetize the vulnerabilities of organizations. It’s not a matter of if, but when, a data breach could impact your organization, and it is important for businesses to understand how to operate in it. What is a Data Breach? For many organizations, a data breach is arguably one of the greatest threats to prevent. What is a data breach? Imagine your organization as a fortress, safeguarding a treasure trove of sensitive information—customer data, financial records, proprietary algorithms. A data breach is the unwelcome intrusion into this fortress, where unauthorized individuals gain access to confidential information, often with malicious intent. This can encompass many types of data, including personal identification information (PII), financial data, and intellectual property. Classifications of breaches can vary from intentional cyberattacks to inadvertent exposure due to system vulnerabilities or human error. To grasp the gravity of data breaches, Businesses face tangible consequences when their defenses are breached, and there are no signs of it slowing down. The frequency and severity of data breaches are alarming. According to recent studies¹, the healthcare sector experienced a 55% increase in data breaches in 2022. No business is immune to the evolving threat landscape especially companies that capture customer data and are also inherently the stewards of this data. Understanding the landscape of data breaches will help you better fortify your business against a breach. In the next sections, we’ll explore the causes, impacts, post-breach response strategies, and preventative tactics businesses can employ to safeguard their data. Causes of Data Breaches Human error Even the most well-intentioned employees can become the weak link in an organization’s security chain. According to the “2023 Verizon Data Breach Investigations Report,” 74% of data breaches involve a human element². Investing in comprehensive training programs is essential to foster a culture of cybersecurity awareness and mitigate the risk of employee-related mistakes. Cybersecurity vulnerabilities The digital landscape is rife with potential vulnerabilities, and cybercriminals are adept at exploiting them. Regular cybersecurity assessments, prompt system updates, and the implementation of robust security protocols are recommended proactive measures to fortify against breaches that capitalize on system vulnerabilities. Insider threats Data breaches can originate from within, whether through disgruntled employees with malicious intent or well-meaning staff who inadvertently compromise security. Gurucul’s “2023 Insider Threat Report” highlights that 60% of organizations experienced insider-related incidents in the past year³. Establishing stringent access controls, closely monitoring user activities, and implementing employee education programs are vital steps to mitigate the risks associated with insider threats. Weak and Stolen Passwords Weak and stolen passwords stand as one of the most common gateways for data breaches. Cybercriminals exploit individuals who use easily guessable passwords or recycle them across multiple platforms. This creates a vulnerability that can be easily exploited through automated attacks. Ensuring robust password policies, employing multi-factor authentication, and regularly updating credentials are necessary measures to thwart these breaches and safeguard sensitive information. Malware The insidious world of malware is a persistent threat to data security. Malicious software, often disguised as innocuous files or links, infiltrates systems, and wreak havoc by compromising data integrity and confidentiality. Malware can then swiftly spread, leading to unauthorized access and data exfiltration. Regularly updating antivirus software, conducting thorough system scans, and educating employees about the dangers of clicking on suspicious links are pivotal defenses against malware-driven breaches. Social Engineering Social engineering has emerged as a cunning and effective tactic in data breaches, such as manipulating individuals to divulge confidential information willingly. Whether through phishing emails, deceptive phone calls, or impersonation, cybercriminals exploit human trust to gain unauthorized access. Raising awareness among employees about the dangers of social engineering, implementing rigorous verification processes, and fostering a culture of skepticism can fortify an organization’s defenses against these subtle yet potent attacks. Physical Attacks While the digital realm often takes center stage, physical attacks on data infrastructure remain a tangible and underestimated risk. Breaches can occur through unauthorized access to servers, theft of physical storage devices, or tampering with network equipment. Implementing stringent access controls, employing surveillance systems, and securing physical infrastructure are crucial steps to mitigate the threat of data breaches stemming from physical incursions. Building digital and physical protective measures can help with your defense against the multifaceted landscape of data breaches. Impacts on Businesses Financial repercussions Data breaches are costly to businesses with immediate and enduring consequences. The “Cost of a Data Breach Report 2023” by IBM reported that the average cost of a data breach was $4.45 million per organization⁴. Long-term financial implications include loss of customers, diminished revenue streams, and increased cybersecurity investments to rebuild trust and fortify defenses against future breaches. Reputational damage The fallout from a data breach extends beyond the balance sheet, leaving an indelible mark on a business’s reputation. According to a 2023 survey by Vercara, 66% of U.S. consumers would not trust a company that falls victim to a data breach with their data. Rebuilding trust with transparent communication, swift remediation, and proactive measures to prevent future breaches is essential, demonstrating a commitment to safeguarding sensitive information. Operational disruptions Data breaches causes disruptions in the operations of daily business activities. It takes an average of 73 days to contain a cyber-attack according to the Cost of a Data Breach Report 2023 from IBM⁴. Swift recovery requires a meticulous balance between addressing the breach’s immediate impact and resuming normal operations to minimize further operational strain. Legal and regulatory implications The legal aftermath of a data breach involves navigating a complex landscape of regulations and compliance standards. In the United States, data breaches may trigger legal consequences under various state laws. For instance, the California Consumer Privacy Act (CCPA) allows for fines ranging from $100 to $750 per consumer per incident⁵. Ensuring adherence to data protection laws, promptly reporting breaches to regulatory authorities, and implementing robust security measures become top priorities in avoiding the legal quagmire that often follows a data breach. Notable data breaches Yahoo! (2014): The personal information of 3 billion people was exposed, including names, birth dates, passwords, and phone numbers. Cause: It is believed that the hack originated through a phishing email sent to a Yahoo! employee. Through this phishing email, it’s believed the hackers were able to access user databases and tools.⁶ Cost: $117.5 million in settlements and $350 million off its sale price to Verizon⁷ Marriott International (2018): Information of approximately 500 million guests was compromised, including names, contact details, passport numbers, and travel details. Cause: A cyber-espionage campaign linked to a state-sponsored actor. Attackers gained access to Marriott’s Starwood guest reservation database due to vulnerabilities in the system.⁸ Cost: Over $100 million for remediation efforts and regulatory fines.⁹ Capital One (2019): 106 million customers’ personal information, including credit card applications and Social Security numbers, was exposed. Cause: A misconfigured web application firewall that allowed a hacker to exploit a server-side request forgery vulnerability, leading to unauthorized access and the theft of sensitive customer data.¹⁰ Cost: Estimated between $100 million and $150 million in 2019 alone.¹¹ SolarWinds (2020): Hackers compromised the software supply chain, affecting numerous government agencies and major corporations globally. Cause: The SolarWinds breach was a sophisticated supply chain attack where malicious actors compromised the software update process, injecting malware into software updates distributed by SolarWinds, allowing them access to numerous government and corporate networks.¹² Cost: At least $18 million¹³ JBS USA (2021): The ransomware attack on the world’s largest meat processor disrupted operations and impacted the company’s IT systems. Cause: A ransomware attack, where cybercriminals exploited vulnerabilities in the company’s IT systems to encrypt data and demand a ransom for its release, causing significant disruptions to operations.¹⁴ Cost: $11 million ransom paid to hackers from JBS to restore their IT systems. Post-breach response Assessment and Damage Control Immediate Action Steps In the event of a data breach, the immediacy of response becomes one factor in determining the outcome. Swift and decisive actions during the initial moments can be instrumental in preventing the situation from escalating. The primary focus at this stage is isolating the affected systems, swiftly disconnecting compromised servers and devices from the network. This can help stop unauthorized access and establishes the foundation for a more concentrated and effective response. Alerting the incident response team, IT personnel, and relevant stakeholders promptly is also worth considering to help gain control over the situation. Forensic Analysis Understanding the who, what, and how of an incident is also an important step following a breach. In this context, involving forensic experts in a meticulous analysis is prudent. These professionals specialize in unraveling the intricacies of the breach, identifying entry points, and tracing the movements of attackers within your systems. The significance of forensic analysis extends beyond mere identification; it serves as the groundwork for prevention. Through a comprehensive study of the employed attack vectors and techniques, organizations can enhance their cybersecurity infrastructure. This process of gathering critical information about the breach contributes to the ability to preempt similar incidents, fostering a more resilient stance against evolving cyber threats. Communication Strategy Internal Communication Effective internal communication plays a pivotal role in building a resilient response framework. In the early stages of a crisis, employees emerge as the initial line of defense. Clearly conveying the severity of the situation provides them with a comprehensive understanding of the impact and the organization’s devised response plan. This also empowers the workforce, fostering a sense of unity within the organization and help the organization navigate challenges ahead cohesively, reinforcing its resilience in the face of adversity. External Communication External communication holds equal importance, reaching beyond the organization to customers, partners, and stakeholders. It’s essential to recognize the significance of constructing messages with transparency, honesty, and a proactive stance. Silence or ambiguity can intensify the repercussions, so prioritizing openness becomes foundational for rebuilding trust. Being timely and forthright in sharing information about the breach and the steps taken to rectify the situation is generally a good strategy when engaging with partners and stakeholders. This approach not only informs but can also mold the perception of the organization’s dedication to security and integrity following the aftermath of a breach with a strategic and forward-thinking mindset. Legal and Regulatory Compliance Notification Requirements Within the regulatory framework, a prompt response is an important post-breach step for organizations. It may first involve comprehensively detailing the legal obligations surrounding breach notifications to both regulatory authorities and affected individuals. It’s essential to recognize the variability in requirements across different regions and industries, underscoring the importance of remaining well-informed about these specific nuances. Timeliness of notifications is also factor for organizations to consider. Numerous jurisdictions impose substantial fines for delays in reporting, making it essential for organizations to adhere to strict timelines. Transparency holds equal weight, necessitating clear communication about the extent of the breach, the nature of compromised information, and the specific measures being implemented to address the situation. This approach can help in being compliant with legal standards and plays a vital role in fostering trust among those directly impacted by the breach. Legal Counsel Engagement Organizations generally seek the support of legal counsel to help navigate the intricate legal aftermath of a data breach. Legal experts can help an organization through potential lawsuits and regulatory fines. Engaging legal experts early allows their insights to guide the overall strategy, shaping everything from the communication plan to the recovery efforts. With early legal counsel support, the organization can be proactive in addressing legal challenges, potentially mitigating the severity of consequences that may arise. Recovery and Remediation IT System Restoration The intricacies of IT system restoration mirror the reconstruction of a fortress following an intrusion. Restoring affected IT systems to normal functionality involves comprehensive measures such as thorough system checks, vulnerability assessments, and the eradication of any residual traces left by a breach. Additionally, organizations generally look to enhance security measures during the recovery phase. Simply reverting to the pre-breach state is not enough; instead, the recovery process serves as an opportunity to accept vulnerabilities in old systems and bolster defenses. This entails updating and patching systems, reassessing access controls, and contemplating the incorporation of advanced threat detection tools. Such measures collectively work to minimize the risk of a recurrence and contribute to an overall fortified cybersecurity posture. Prevention Strategies Best practices for securing sensitive data Securing sensitive data is important in the age of relentless cyber threats. Employing encryption protocols, conducting regular security audits, and limiting access privileges are foundational best practices. These proactive measures help create a robust defense, forming an intricate web that shields critical information from potential breaches. Employee training programs to mitigate human error Human error remains a significant contributor to data breaches. Implementing comprehensive employee training programs can be helpful in cultivating a security-conscious workforce and mitigating human error-caused vulnerabilities. From recognizing phishing attempts to practicing proper password hygiene, a well-informed staff acts as the first line of defense and can significantly reduce the likelihood of unintentional security lapses. Implementing robust cybersecurity measures The cornerstone of any data breach prevention strategy is the implementation of robust cybersecurity measures. This includes advanced intrusion detection systems, firewalls, and regular software updates. Proactively addressing vulnerabilities and staying abreast of the latest cybersecurity advancements help fortify an organization’s digital perimeter, creating an environment that is inherently resistant to malicious infiltrations. Staying abreast of emerging trends Staying ahead of data breach threats requires a keen awareness of emerging trends. From sophisticated phishing techniques to novel forms of malware, businesses should continuously adapt their cybersecurity strategies against evolving tactics employed by cybercriminals. The dynamic nature of the cybersecurity landscape demands constant innovation. Adopting cutting-edge technologies like artificial intelligence for threat detection and investing in predictive analytics allows businesses to stay one step ahead, proactively identifying and neutralizing potential threats before they escalate. Collaboration and information-sharing within industries In the face of evolving cyber threats, collaboration is a powerful defense. Establishing networks for information-sharing within industries enables businesses to benefit from collective intelligence. By sharing best practices and threat intelligence, organizations can collectively strengthen their defenses against the ever-changing data breach landscape. Takeaway Data breaches are a persistent threat for all businesses capturing and storing personal identifiable information. Such businesses are inherently the stewards of this data and must protect that data to avoid bad actors gaining access for malicious intent. Knowing what a data breach is just the first step of protecting that data, and it is key to take action. From securing sensitive data to fostering a cybersecurity-aware workforce, businesses must not merely react to the escalating threat of data breaches but proactively strive to create an impenetrable shield around their valuable information. Visit our website for more information about our offerings and how Experian can help you prepare and respond to data breaches. ¹Hippa Journal, 55% of Healthcare Organizations Suffered a Third-Party Data Breach in the Past Year [2022]²Verizon, 2023 Verizon Data Breach Investigations Report³Gurucul, 2023 Insider Threat Report⁴IBM, Cost of a Data Breach Report 2023⁵Office of the Attorney General, California Consumer Privacy Act (CCPA)⁶CSO, INside the Russian hack of Yahoo: How they did it⁷BPB Online, Yahoo Data Breach: What Actually Happened?⁸CSO, Marriott data breach FAQ: How did it happen and what was the impact?⁹Cybersecurity Dive, Marriott finds financial reprieve in reduced GDPR penalty¹⁰Investopedia, Capital One Data Breach Impacts 106 Million Customers¹¹CNET, Capital One $190 Million Data Breach Settlement: Today Is the Last Day to Claim Money¹²Tech Target, SolarWinds hack explained: Everything you need to know¹³Reuters, SolarWinds says dealing with hack fallout cost at least $18 million¹⁴BBC, Meat giant JBS pays $11m in ransom to resolve cyber-attack

2023-2024 Experian Data Breach Response Guide Learn how you can boost your preparedness against cyberattacks—download the new guide now. As the proliferation of connected devices and third-party integrations accelerate, organizations are becoming more exposed to risk. Your attack surface is expanding, and it’s a hacker’s dream. But their dream is your nightmare. While there will always be at least one monster hiding under the bed, being prepared and having a plan can help you sleep easier and soften the blow when an attack does happen. How likely is your organization to be the victim of an attack? As pointed out in the 9th Annual Experian Data Breach Response Guide, “Cyber attacks happen once every 39 seconds.[1] There’s no time to rest, and no time to let your guard down. It’s just a matter of time before your data becomes a target, whether it is a direct hit to your organization or through a third-party supply chain attack (one of the latest trends hackers are using to gain access to huge amounts of data in just one sweep). You never know when your day will come, so being prepared now is the only way. 15% fewer incidents occur on average for customers with a plan.[2] Having fewer incidents helps keep your data safer and your bottom line healthier as the cost of a data breach continues to break records year after year. Learn How You Can Be Prepared Our 2023-2024 Data Breach Response Guide has been updated with the latest predictions, trends, and expert advice based on real-world experience. This is the ninth year I’ve rolled out this guide, and it gets better every year, with deeper insights into the state of cyber threats across industries and current best practices, and step-by-step guidance for creating, testing and implementing a plan for your business. Highlights include: Third-party breaches are rising — A partner breach make up 62% of system intrusions.[3] Healthcare and financial services have the highest volume of breaches, representing over half the share of breaches serviced by Experian in 2022.[4] How having a response plan can save your business—90% of consumers are more forgiving of companies that had a response plan before a breach.[5] How Experian Data Breach Solutions can help your organization respond quickly to and minimize the impact of a data breach Ready to Get Started? A data breach preparedness plan is never a one-and-done deal. It needs to evolve along with the cyber threats it is meant to conquer. Experian is a partner you can trust. We continue to expand our product offerings, keep our eyes and ears on the lookout for rising threats and trends, and use our years of experience to support our partners when they need us most. Download the latest edition of the Experian® Data Breach Guide [1] Zippia, 30 Crucial Cybersecurity Statistics [2023]: Data, Trends and More. [2] Experian Data June 2023 [3] Resmo, Third-Party Data Breach Statistics. [4] Experian Data June 2023 [5] Experian Data Breach Consumer Survey.

When a data breach occurs, it can have a ripple effect on your business, your employees, and your customers. Depending on the severity of the breach, large volumes of personally identifiable information – such as email addresses, birth dates, passwords, social security numbers, etc. – may fall into the hands of unauthorized people who intend to exploit that information for personal gain. While data breaches are difficult to predict, you can take proactive steps to ensure that your business and your customers are well equipped to respond quickly and drive faster resolution. Create a plan The average cost of a data breach in 2023 is $4.45 million, a 15% increase from 2020[1]. This is a considerable loss that can be devastating to a business of any size. The best strategy to mitigate this kind of loss is to be prepared with a data breach response plan. If your business experiences a data breach and you’re unprepared for it, the losses you and your customers incur can be much more serious, and the damage to your company’s bottom line and reputation can last much longer than necessary. By establishing a data breach response plan, you can limit the downside potential of an attack and considerably shorten the recovery time. This can help your business and your customers return to good standing as soon as possible. Arm your team with knowledge The IT department is no longer the only line of defense against cyberattack or data breaches. Many hackers will try to illegally obtain sensitive information from front line or associate level employees using a variety of methods like phishing, ransomware, or social engineering. This puts the responsibility of protecting company data on every employee, not just on the cybersecurity team. This is why it’s important to educate all of your employees on how to recognize potential threats of a data breach. With this knowledge, they can work collectively to keep consumers’ data safe and secure. Address your customers’ concerns effectively If a data breach happens to your business, it’s crucial to notify your customers as soon as possible. Not only should you alert them of the breach, but you should also have a protocol in place to provide up-to-date information, helpful resources, and reassurance. Whether through email, in-app notifications, or call center agents, your customer response process should include clear, frequent, and timely communication throughout the duration of the breach. Keeping your customers informed and at ease during a breach will encourage them to remain calm and feel confident to continue doing business with you. Data breaches and cyberattacks are unpredictable and can have unforeseen, long-lasting negative effects on small, medium, and large businesses alike. But if you have a solid plan, keep your employees knowledgeable about potential threats, and provide useful, timely information to your customers, you can minimize the damage of any breach on your organization. Visit our website for more information about our offerings and how Experian can help you prepare and respond to data breaches. [1]IBM. Cost of a Data Breach Report 2023.

When it comes to online personal data, the majority of Americans believe it has become more and more difficult to control who has access to that information.[1] And as international data breaches continue to feed the dark web, the cost is high for consumers. Identity theft by the numbers At least 16 billion records have been exposed through data breaches since 2019, and 31% of data breach victims later have their identity stolen[2]. The cost of obtaining a full range of documents and account details allowing identity theft is about $1,275.[3] With a 290% increase in stolen data found on the dark web in the past three years, monitoring is a must-have for data-driven service providers[4]. Now more than ever, consumers expect businesses that collect their information to keep it secure. A solution for your customers Here’s the good news: Experian CyberAgent® is a proprietary, patented dark web technology that proactively detects compromised confidential data online around the world. With more than 21 billion records found, this software is designed for proactive cyber detection on an international level. CyberAgent® monitors a variety of identity elements and captures all the data being exchanged, including: Social Security numbers National identification numbers Email addresses/ domains and phone numbers Medical identifications numbers Passport and driver’s license numbers Credit/debit card information Retail card numbers Bank account and routing numbers International banking numbers Global protection As the only internet surveillance tool that can match data on an international level, CyberAgent® breaks language barriers and detects identity theft across the globe. By monitoring thousands of websites and millions of data points, this technology enables you to notify your customers if a match to their monitored personal information is found. Alert your customers before they become a victim of identity theft and offer unrivaled protection from dark web threats. Click here to learn more [1]Ipsos. 2022. Most Americans say it is increasingly difficult to control who can access their online data. [2]Selfkey. 2020. All Data Breaches in 2019 – 2022 – An Alarming Timeline. [3]Privacy Affairs. 2020. Dark Web Price Index 2020. [4]Experian CyberAgent® monitoring counts as of June 2022.

What is elder abuse fraud? Financial abuse is reportedly the fastest-growing form of elder abuse, leaving many Americans vulnerable to theft scams, and putting businesses and other organizations on the frontlines to provide protection and help prevent fraud losses. Financial elder abuse fraud occurs when someone illegally uses a senior’s money or other property. This can be someone they know, or a third party – like fraudsters who are perpetrating romance scams Older consumers and other vulnerable digital newbies were prime targets for this type of abuse during the start of the pandemic when many of them became active online for the first time or started transacting in new ways. This made them especially attractive targets for social engineering (when a fraudster manipulates a person to divulge confidential or private information) and account takeover fraud. While most of us have become used to life online (in fact, there’s been a 25% increase in online activity since the start of the pandemic), some seniors still have risky habits such as poor password maintenance, that can make them more attractive targets for fraudsters. What is the impact of elder abuse fraud? According to the FBI’s Internet Crime Complaint Center (IC3), elder abuse fraud cost Americans over the age of 60 more than $966 million in 2020. In addition to the direct cost to consumers, elder abuse fraud can leave organizations vulnerable to the fallout from data breaches via account takeover, and lost time and money spent helping seniors and other vulnerable Americans recoup their losses, reset accounts, and more. Further, the victim may associate the fraud with the bank, healthcare provider, or other businesses where the account was taken over and decide to stop utilizing that entity all together. How can organizations prevent elder abuse fraud? Preventing elder abuse fraud can take many forms. Organizations should start with a robust fraud management solution that can help prevent account takeover, first-party, synthetic identity fraud, and more. This platform should also include the ability to use data analysis to detect and flag sudden changes in financial behavior, online activities, and transaction locations that could indicate abuse or takeover of the account. With the right fraud strategy in place, organizations can help prevent fraud and build trust with older generations. Given that 95% of Baby Boomers cite security as the most important aspect of their online experience, this step is too important to miss. To learn more about how Experian is helping organizations develop and maintain effective fraud and identity solutions, be sure to visit us or request a call. Contact us

The Threat “With criminals, there’s no such thing as a border anymore. They don’t care where you are, who you are; if there’s money to take from you, they will take it.” That’s what U.S. Secret Service Agent Eric Adams had to say when asked about cybersecurity threats during the “Global Cyber Threatscape & the Role of Law Enforcement” panel I moderated at the latest NetDiligence CyberRisk Summit event. It’s clear to law enforcement that cybercriminals are hyper-connecting, deep information sharing, and crossing virtual borders—becoming more brazen (and clever) by the breach—leaving businesses, insurers, organizations, regulators, and consumers in the cross hairs of compromise, compliance, and recoupment. “We work with law enforcement; we work with insurance companies. We’re collecting data and trying to solve those problems because we understood that if you don’t cooperate before the incident, you don’t work together [at all].” – Michael Bruemmer, Experian During the “Beyond the Arrest: Law Enforcement Roundtable,” Adams and three other cross-border experts, Brian Abellera, Jason Conboy, and Matt Robinson, gave in-depth accounts of “cross-border incident response and the role of U.S. cyber law enforcement and oversees intelligence.” “We’re seeing smaller and medium-sized businesses [being targeted by ransomware]. We are really struggling to keep up with the information flow.” – Matt Robinson, RCMP I frequently talk about how quickly the threats are evolving and how Every Minute Counts in data breach response. The panel echoed this sentiment tenfold, covering five key topics, including “Unique Characteristics of U.S.-Canada Cyber” and “Public-Private International Cooperation.” The Evidence Board “We have to be nimble like the cybercriminals; putting in cyber liaisons internationally.” – Jason Conboy, U.S. Department of Homeland Security Investigations From stem swapping, ransomware revictimization, and romance schemes, the experts discussed how cross-border threats are infiltrating every square inch of the data security landscape. They also focused on the critical role of education, tabletop exercises, and timely incident reporting while zeroing in on how public-private partnerships can influence better outcomes and impact data protection, regulation, and litigation. Watch the full NetDiligence Cyber Risk Summit session on-demand

In the first six months of 2021, there was $590 million in ransomware-related activity, which exceeds the value of $416 million reported for the entirety of 2020 according to the S. Treasury's Financial Crimes Enforcement Network. Constant economic pressure coupled with the ever-increasing volume of data online have created an environment that’s ripe for attacks, leaving businesses and consumers vulnerable to attacks and theft. What are ransomware attacks? Ransomware is a subset of malicious software, AKA malware, that either threatens to publish or block access to data or a computer system. It often takes the form of a cyberattack where criminals take over an organization’s computer network. Once they’ve assumed control, the hackers demand a ransom to restore access to the illicitly encrypted data. Additionally, ransomware attacks and data breaches are now becoming more closely linked, with sensitive data including employees’ personal information, HR records, and more being filtered out and distributed during or after the attack. In fact, Experian has found that 7 of 10 data breaches involve ransomware. The negative impact of ransomware attacks According to the Identity Theft Resource Center, the average ransom demand in 2021 was $5.3 million, a 518% increase from the 2020 average. Experian’s latest Data Breach Response Guide found that businesses were hit with ransomware attacks every 11 seconds in 2021. These attacks also take up to 20% longer to begin breach notifications, leaving businesses even more vulnerable. In addition to the monetary loss and the time spent responding to and recovering from the attack, businesses also stand to suffer reputational damage, because consumer sentiment is that companies are responsible for protecting data. Having a plan in place makes a sizeable impact though, with 90% of consumers being more forgiving of companies that had a response plan in place prior to a breach. How to protect against ransomware attacks Experian’s 2022 Future of Fraud Forecast predicts that ransomware will be a significant fraud threat for companies as fraudsters will look for a sizeable ransom to cede control and potentially steal data from the hacked company. Preparing for the possibility of an attack includes training your staff to spot the signs of a phishing attempt, having a response plan in place, and leveraging partner solutions. To learn more about how Experian helps businesses protect against the fallout of a ransomware attack, visit us, and be sure to read about our other Future of Fraud predictions about cryptocurrency and Buy Now, Pay Later fraud. Request a call Future of Fraud Forecast

As we navigate a new way of living, working, and handling the unpredictability of COVID-19 and other potential health concerns worldwide, now is not the time to ease up on data breach preparedness. I’ve said it many times before, and I’ll repeat it, every minute counts in today’s fast-breaking data breach response environment. As pointed out in the foreword of the 8th Annual Experian® 2022 Data Breach Response Guide, “Almost everything is done and undone with a screen touch, keystroke, password, or pin.” It is a convenient reality for consumers looking to make quick, returnable digital purchases, as it is for hackers who can cause irreversible financial and reputational harm to companies and organizations. In this world, it’s not an option to put data breach preparedness on the back burner. Every employee in your organization, from the C-suite to the call center, must stay ready. In 2021, the average cost of a data breach was $4.24 million.[1] Industry Perspectives, Current Data, Consumer Response New and improved for 2022-2023, our latest Data Breach Response Guide is an in-depth preparedness page-turner, complete with predictions, trends, experienced-based advice from Experian experts, and real-world incident insight informed by servicing breaches over 15 years. The Highlights I’ve managed the roll-out of this guide for years, and I have to say, this guide is the most comprehensive and data-dense one yet. It has everything you need to learn how to prepare, plan, practice, audit, and manage your crisis response. You’ll get details on: The Rise of Ransomware—one happened every 11 seconds in 2021[2] What do businesses think about response plan drills?—84% agree their plans could be more effective with drills[3] Why hackers’ top industry target is still healthcare) and why How Experian® Crisis Solutions helps companies recover strong, much more Cyberattack Preparation is Paramount Cybersecurity and data breach preparedness is changing by the minute. Experian is expanding its product offerings, staying on top of rising threats, and relying on our deep experience to support partners when they need us most. Ready to learn more about how to stay ready for a data breach? Download the Experian® Data Breach Guide now. For additional preparedness insights, sign up for our free resource hub. [1] IBM & Ponemon 2021 Cost of a Data Breach Report [2] Cybersecurity Ventures, Cybercrime to Cost the World $10.5 Trillion Annually by 2025 [3] Experian and Ponemon. 2022. Ninth Annual Study: Is Your Company Ready for a Big Data Breach

Crises come in many forms, without warning, and can be devastating for any size business. A company’s ability to manage crises, specifically with a crisis response notification plan, directly impacts consumers’ trust and perception of their brand. In today’s digital world, consumers are more informed than ever before and consumer trust is what keeps businesses afloat. If that trust is broken or their needs are not met, consumers will take their business elsewhere. Companies cannot afford to lose customers. Research from Frederick Reichheld of Bain & Company, the inventor of the Net Promoter Score, shows that increasing customer retention rates by 5 percent increases profits by 25 percent.[1] When a crisis occurs, 90 percent of consumers are more forgiving of companies that have a response plan in place.[2] Despite that information, 51 percent of companies admit to not having a crisis response notification plan.[3] While crisis communication can be fairly reactive, it helps to have a crisis communication plan in place to make the process easier. Experian Crisis Response Management features a notification system, call center deployment, and crisis specialists to help companies build trust and confidence knowing that their consumers will be taken care of, which breeds customer loyalty. Our team of experts can help you develop a crisis response notification plan to reach out to your customers during any type of crisis. Here are five key steps to developing an effective crisis response notification plan Step 1: Define Your Objective Before you begin, you must first set a clear goal for your plan. This objective should include what the plan should accomplish, when the plan should be executed, and who needs access to the information being shared. For example, “This plan creates a communication structure with external stakeholders in the event of a crisis that affects the reputation of the company.” Step 2: Create a Contact List To ensure the crisis is well-managed, it’s important that all stakeholders are kept informed. Create a contact list of all employees, customers, users, partners, investors, media outlets, the government, and social media followers. Determine the best method of contact for each of these stakeholders (i.e., print mail, email, phone call, etc.) and include that in the contact list document. Step 3: Determine an Information Sharing Structure Depending on where a crisis originates and the threat level of the crisis, protocols may differ by scenario. To avoid confusion, form a hierarchy outlining how information should be shared within the company. Your hierarchy may begin with notifying the CEO, followed by the head of public relations or CTO. The plan needs to define what information should immediately be disclosed to each individual or team in the hierarchy, such as the source of the crisis and the protocols in place to handle the situation. Step 4: Prepare for Possible Questions and Concerns Customers will want answers and if you are not the one supplying them, they will search elsewhere to uncover the truth. Create a running fact sheet that documents the known information of the situation. This helps to prevent rumors or misinterpretations from spreading to media outlets, keeps all responses in alignment, and makes it easier to field customer questions. Step 5: Assess Your Risks Identify the risks you might face under each plan so that, if it does backfire, you’re prepared for any additional losses. By being prepared for this, you’ll be ready for anything that goes wrong with steps to recover faster. Fulfilling your notifications Once you have determined who will receive your crisis response notifications, it is time to fulfill your obligations. Ensure every access point is covered by creating a notification system with Experian for direct emails, call center processes, and a landing page users can go to for fast information. 1. Notification Options Notification requirements vary depending on the crisis at hand and your customers’ preferred method of contact. Some common examples include: Paper mailings Email notification Web announcement Phone calls You may also consider a multipronged approach, which includes email or paper notifications, supported by a website FAQ and a call center where consumers can get more information. 2. Outbound notification and inbound response management Experian offers sufficient phone, website, and application capacity to absorb the spikes of crisis volume on top of normal operating volumes. This service includes address validation, delivery that covers 100+ countries, reporting and analytics of the notification channels, and a dedicated account manager that oversees the entire process. 3. Experienced team of agents Our team of dedicated account managers have serviced over 50,000 incidents, delivered over 30 million print and email notifications each year, and developed a comprehensive range of products for every need. We stay with you as a resource throughout the crisis process and work with you to recover, repair, and protect your business for the future. No one ever expects a crisis to hit, but when it does, it’s important to have a plan in place. Having a dedicated team who can help you navigate through difficult times is essential to quick recovery. At Experian, we understand the importance of customer trust and we help companies recover from crises quickly. Our team of experts are available to help when you need it most. Learn more about our Crisis Response Management services ____________________________________________ [1] Bain & Company. 2001. Prescription for Cutting Costs. [2] Experian. 2019. Data Breach Consumer Survey. [3] Deloitte. 2020. A crisis of confidence.