Tag: fraud trends

In today’s digital payments landscape, fraudsters are constantly developing new tactics to exploit vulnerabilities. One of the most common credit card schemes financial institutions and merchants face are BIN attacks. But what exactly is a BIN attack, and how does BIN attack fraud work? What is a BIN attack? BIN attacks, a type of card not present fraud, target the Bank Identification Number (BIN) — the first six to eight digits of a credit or debit card number that identify the issuing financial institution. Fraudsters use these digits to systematically generate and test potential card number combinations. The goal of a BIN attack is to discover valid card numbers that can be used for fraudulent transactions. Because BINs are publicly available and consistent across card issuers, they provide a predictable framework for attackers. How does it differ from other types of payment fraud? Payment fraud takes many forms, but BIN attacks stand apart because of their scale and automation. Card testing fraud vs. BIN attacks: Both involve criminals running authorization attempts to identify valid card details. However, card testing typically uses data from a single stolen card, while BIN attacks systematically generate thousands of possible card numbers from a known BIN range. Account takeover fraud vs. BIN attacks: In an account takeover, fraudsters gain access to a customer’s existing account, often through phishing or stolen login credentials. BIN attacks don’t require account access — instead, they exploit card number patterns to guess valid accounts. What are the consequences of a BIN attack? BIN attacks don’t just result in stolen card numbers — they create wide-ranging business risks that can impact operations, revenue and customer trust. For financial institutions and merchants, the ripple effects can be significant: High transaction volumes: BIN attacks are carried out using automated scripts or bots that fire off thousands of transaction attempts per minute. This traffic can overwhelm payment systems, slow down processing and disrupt the checkout experience for legitimate customers. Increased chargebacks: Once fraudsters identify valid cards, they make unauthorized purchases that often result in chargebacks. Both merchants and issuers absorb these losses — merchants lose revenue, while issuers reimburse cardholders. Network and processing costs: Every transaction attempt — even those declined during a BIN attack — still incurs network and processing fees. Merchants and issuers can end up paying for thousands of authorization requests, draining resources. Reputational damage: Today’s consumers expect seamless and secure payments. If they experience frequent declines, blocked cards or fraudulent activity, their trust in the institution or merchant erodes. How to protect against BIN attack fraud Mitigating BIN attacks requires a proactive, layered defense strategy. Financial institutions and merchants should consider: Advanced fraud detection and analytics: BIN attacks generate massive volumes of fraudulent traffic. By leveraging AI-driven analytics and machine learning, institutions and merchants can monitor for unusual transaction patterns, velocity spikes and bot-driven activity. Identity and device intelligence: Fraudsters often hide behind bots, stolen IP addresses and compromised devices. With identity verification and device intelligence solutions, merchants and institutions can better determine whether a transaction is coming from a legitimate customer or a fraudster testing card details. Multi-factor authentication (MFA): BIN attacks succeed on speed and automation, firing off thousands of transactions. MFA can help disrupt this process by requiring additional proof of identity from the customer, such as facial recognition or one-time passcodes. Credit card authentication: BIN attacks exploit the gap between payment credentials and the identity of the person using them. A solution like Experian LinkTM seamlessly connects the payment instrument with the digital identity presented for payment, helping merchants to reduce false declines, fraud and operating expenses. Build a stronger defense against BIN attacks BIN attacks are a growing threat in today’s digital payments ecosystem. But with the right safeguards in place, organizations can stay ahead. Learn how Experian can help you strengthen your fraud defenses to reduce losses and protect customer trust. Learn more

In this article...What is a TOAD attack?How TOAD attacks happenEffective countermeasures Keeping TOADS at bay with Experian Imagine receiving a phone call informing you that your antivirus software license is about to expire. You decide to renew it over the phone, and before you know it, you have been “TOAD-ed”! What is a TOAD attack? Telephone-Oriented Attack Deliveries (TOADs) are an increasingly common threat to businesses worldwide. According to Proofpoint's 2024 State of the Phish Report, 10 million TOAD attacks are made every month, and 67% of businesses globally were affected by a TOAD attack in 2023. In the UK alone, businesses have lost over £500 million to these scams, while in the United States the reported monetary loss averaged $43,000 per incident, with some losses exceeding $1 million.TOADs involve cybercriminals using real phone numbers to impersonate legitimate callers, tricking victims into divulging sensitive information or making fraudulent transactions. This type of attack can result in substantial financial losses and reputational damage for businesses. How TOAD attacks happen TOAD attacks often involve callback phishing, where victims are tricked into calling fake call centers. Before they strike, scammers will gather a victim's credentials from various sources, such as past data breaches, social media profiles, and information bought on the dark web. They will then contact the individual through applications like WhatsApp or call their phone directly. Here is a common TOAD attack example: Initial contact: The victim receives an email from what appears to be a reputable company, like Amazon or PayPal. Fake invoice: The email contains a fake invoice for a large purchase, prompting the recipient to call a customer service number. Deception: A scammer, posing as a customer service agent, convinces the victim to download malware disguised as a support tool, granting the scammer access to the victim's computer and personal information. These techniques keep improving. One of the cleverer tricks of TOADs is to spoof a number or email so they contact you as someone you know. Vishing is a type of phishing that uses phone calls, fake numbers, voice changers, texts, and social engineering to obtain sensitive information from users. It mainly relies on voice to fool users. (Smishing is another type of phishing that uses texts to fool users, and it can be combined with phone calls depending on how the attacker works.) According to Rogers Communication website, an employee in Toronto, Canada got an email asking them to call Apple to change a password. They followed the instructions, and a “specialist” helped them do it. After receiving their password, the cyber criminals used the employee's account to send emails and deceive colleagues into approving a fake payment of $5,000. Artificial intelligence (AI) is also making it easier for TOAD phishing attacks to happen. A few months ago, a Hong Kong executive was fooled into sending HK$200m of his company's funds to cyber criminals who impersonated senior officials in a deepfake video meeting. Effective countermeasures To combat TOAD attacks, businesses must implement robust solutions. Employee training and awareness: Regular training sessions and vishing simulations help employees recognize and respond to TOAD attacks. Authentication and verification protocols: Implementing multi-factor authentication (MFA) and call-back verification procedures enhances security for sensitive transactions. Technology solutions: Bots and spoofing detection and voice biometric authentication technologies help verify the identity of callers and block fraudulent numbers. Monitoring and analytics: Advanced fraud detection and behavioral analytics identify anomalies and unusual activities indicative of TOAD attacks. Secure communication channels: Ensure consumers have access to verified customer service numbers and promote secure messaging apps. A strong strategy should also involve using advanced email security solutions with AI fraud detection and machine learning (ML) to effectively defend against TOAD threats. These can help identify and stop phishing emails. Regular security audits and updates are necessary to find and fix vulnerabilities, and an incident response plan should be prepared to deal with and reduce any breaches. By integrating technology, processes, and people into their strategy, organizations can develop a strong defense against TOAD attacks. Keeping TOADS at bay with Experian® By working and exchanging information with other businesses and industry groups, you can gain useful knowledge about new or emerging threats and defense strategies. Governments and organizations like the Federal Communications Commission (FCC) have a shared duty to defend the private sector and public consumers from TOAD attacks, while many of the current rules and laws seem to lag behind what criminals are doing. By combining the best data with our automated ID verification processes, Experian® helps you protect your business and reputation. Our best-in-class solutions employ device recognition, behavioral biometrics, machine learning, and global fraud databases to spot and block suspicious activity before it becomes a problem. Learn more *This article includes content created by an AI language model and is intended to provide general information.

This article was updated on March 4, 2024. If you steal an identity to commit fraud, your success is determined by how long it takes the victim to find out. That window gets shorter as businesses get better at knowing when and how to reach an identity owner when fraud is suspected. In response, frustrated fraudsters have been developing techniques to commit fraud that does not involve a real identity, giving them a longer run-time and a bigger payday. That's the idea behind synthetic identity (SID) fraud — one of the fastest-growing types of fraud. Defining synthetic identity fraud Organizations tend to have different definitions of synthetic identity fraud, as a synthetic identity will look different to the businesses it attacks. Some may see a new account that goes bad immediately, while others might see a longer tenured account fall delinquent and default. The qualifications of the synthetic identity also change over time, as the fraudster works to increase the identity’s appearance of legitimacy. In the end, there is no person to confirm that fraud has occurred, in the very best case, identifying a synthetic identity is inferred and verified. As a result, inconsistent reporting and categorization can make tracking and fighting SID fraud more difficult. To help create a more unified understanding and response to the issue, the Federal Reserve and 12 fraud experts worked together to develop a definition. In 2021, the Boston Federal Reserve published the result, “Synthetic identity fraud is the use of a combination of personally identifiable information to fabricate a person or entity to commit a dishonest act for personal or financial gain."1 To break down the definition, personally identifiable information (PII) can include: Primary PII: Such as a name, date of birth (DOB), Social Security number (SSN) or another government-issued identifier. When combined, these are generally unique to a person or entity. Secondary PII: Such as an address, email, phone number or device ID. These elements can help verify a person or entity's identity. Synthetic identities are created when fraudsters establish an identity from scratch using fake PII. Or they may combine real and fake PII (I.e., a stolen SSN with a fake name and DOB) to create a new identity. Additionally, fraudsters might steal and use someone's SSN to create an identity - children, the elderly and incarcerated people are popular targets because they don't commonly use credit.4 But any losses would still be tied to the SID rather than the victim. Exploring the Impact of SID fraud The most immediate and obvious impact of SID fraud is the fraud losses. Criminals may create a synthetic identity and spend months building up its credit profile, opening accounts and increasing credit limits. The identities and behaviors are constructed to look like legitimate borrowers, with some having a record of on-time payments. But once the fraudster decides to monetize the identity, they can apply for loans and max out credit cards before ‘busting out’ and disappearing with the money. Aite-Novaric Group estimates that SID fraud losses totaled $1.8 billion in 2020 and will increase to $2.94 billion in 2024.2 However, organizations that do not identify SIDs may classify a default as a credit loss rather than a fraud loss. By some estimates, synthetic identity fraud could account for up to 20 percent of loan and credit card charge-offs, meaning the annual charge-off losses in the U.S. could be closer to $11 billion.3 Additionally, organizations lose time and resources on collection efforts if they do not identify the SID fraud. Those estimates are only for unsecured U.S. credit products. But fraudsters use synthetic identities to take out secured loans, including auto loans. As part of schemes used to steal relief funds during the pandemic, criminals used synthetic identities to open demand deposit accounts to receive funds. These accounts can be used to launder money from other sources and commit peer-to-peer payment fraud. Deposit account holders are also a primary source of cross-marketing for some financial institutions. Criminals can take advantage of vulnerable onboarding processes for deposit accounts where there’s low risk to the institution and receive offers for lending products. Building a successful SID prevention strategy Having an effective SID prevention strategy is more crucial than ever for organizations. Aside from fraud losses, consumers listed identity theft as their top concern when conducting activities online. And while 92% of businesses have an identity verification strategy in place, 63% of consumers are "somewhat confident" or "not very confident" in businesses' ability to accurately identify them online. Read: Experian's 2023 Identity and Fraud Report Many traditional fraud models and identity verification methods are not designed to detect fake people. And even a step up to a phone call for verification isn't enough when the fraudster will be the one answering the phone. Criminals also quickly respond when organizations update their fraud detection methods by looking for less-protected targets. Fraudsters have even signed their SIDs up for social media accounts and apps with low verification hurdles to help their SIDs pass identity checks.5 Understand synthetic identity risks across the lifecycle Synthetic Identities are dynamic. When lending criteria is tightened to synthetics from opening new accounts, they simply come back when they can qualify. If waiting brings a higher credit line, they’ll wait. It’s important to recognize that synthetic identity isn’t a new account or a portfolio management problem - it’s both. Use analytics that are tailored to synthetic identity Many of our customers in the financial services space have been trying to solve synthetic identity fraud with credit data. There’s a false sense of security when criteria is tightened and losses go down—but the losses that are being impacted tend to not be related to credit. A better approach to synthetic ID fraud leverages a larger pool of data to assess behaviors and data linkages that are not contained in traditional credit data. You can then escalate suspicious accounts to require additional reviews, such as screening through the Social Security Administration's Electronic Consent Based SSN Verification (eCBSV) system or more stringent document verification. Find a trusted partner Experian's interconnected data and analytics platforms offer lenders turnkey identity and synthetic identity fraud solutions. In addition, lenders can take advantage of the risk management system and continuous monitoring to look for signs of SIDs and fraudulent activity, which is important for flagging accounts after opening. These tools can also help lenders identify and prevent other common forms of fraud, including account takeovers, e-commerce fraud, child identity theft fraud and elderly fraud. Learn more about our synthetic identity fraud solutions. Learn more 1Federal Reserve Bank (2021). Defining Synthetic Identity Fraud 2Aite Novarica (2022). Synthetic Identity Fraud: Solution Providers Shining Light into the Darkness 3Experian (2022). Preventing synthetic identity fraud 4The Federal Reserve (2022). Synthetic Identity Fraud: What Is it and Why You Should Care? 5Experian (2022). Preventing synthetic identity fraud

Fraud is a serious concern for everyone, including businesses and individuals. In fact, according to our 2023 U.S. Identity and Fraud Report, nearly two-thirds (64%) of consumers are very or somewhat concerned with online security, and over 50% of businesses have a high level of concern about fraud risk. The fraud landscape is constantly evolving, and staying vigilant against the latest trends is critical to safeguarding your organization and consumers. As we reflect on 2023, let’s look at the top fraud trends and their continued potential impact on your business. The evolution of new fraud trends When economic uncertainty reigns, a rise in fraud often follows. To begin with, consumers tend to be financially stressed in such periods and prone to making risky decisions. In addition, fraudsters are keenly aware of the opportunities inherent in unstable times and develop tactics to take advantage of them. For example, as consumers rein in spending and financial institutions struggle to maintain new account volumes, fraudsters might ramp up their new account and loan activities. Fraud is becoming more sophisticated. For instance, thanks to the rapid rise in the availability of artificial intelligence (AI) tools, fraudsters are increasingly able to impersonate companies and individuals with ease, as well as consolidate data from diverse sources and use it more efficiently. The most impactful fraud trends of 2023 The fraud trends that emerged in 2023 were diverse, though they all had one thing in common: fraudsters' keen ability to take advantage of new technologies and opportunities. And businesses are feeling the repercussions, with nearly 70% reporting that fraud losses have increased in recent years. Here are five trends we forecasted in the fraud and identity space that challenged fraud fighters on the front lines this year. Deposit and checking account fraud With everyone focused on fraud in the on-line channels, it is interesting that financial institutions reported more fraud occurring at brick-and-mortar locations. Preying on the good nature of helpful branch employees, criminals are taking risks by showing up in person to open accounts, pass bad deposits and try to work their way into other financial products. The Treasury Department reports complaints doubling YoY, after increasing more than 150% between 2020 and 2021. Synthetic identity fraud Not quite fake, not quite real, so-called synthetic or "Frankenstein" identities mash up real data with false information to create unique customer profiles that can outsmart retailers' or financial institutions' fraud control systems. With synthetic identity (SID) fraud real data is often stolen or purchased on the dark web and combined with other information — even Artificial Intelligence (AI)-created faces — so that fraudsters can build up a synthetic identity's credit score before taking advantage of them to borrow and spend money that will never be paid back. One major risk? As fraud rates rise due to the use of tactics like synthetic identities, it could become more challenging and expensive to access credit. Fake job postings and mule schemes Well-paying remote work was in high demand this year, creating opportunities for fraudsters to create fake jobs to harvest data such as Social Security numbers from unsuspecting applicants. Experian also predicts a continued rise in "mule" jobs, in which workers unknowingly sign on to do illegal work, such as re-shipping stolen goods. According to the Better Business Bureau, an estimated 14 million people get caught in a fake employment scam yearly. Job seekers can protect themselves by being skeptical of jobs that ask them to do work that appears suspicious, requires money, financial details, or personal information upfront. Peer-to-peer payment fraud Peer-to-peer payment tools are increasingly popular with consumers and fraudsters, who appreciate that they're both instant and irreversible. Experian expects to continue to see an increase in fraudulent activity on these payment systems, as fraudsters use social engineering techniques to deceive consumers into paying for nonexistent merchandise or even sharing access credentials. Stay safe while using peer-to-peer payment tools by avoiding common scams like requests to return accidental payments, opting for payment protection whenever possible and choosing other transaction methods like paying with a credit card. Social media shopping fraud Social media platforms are eager to make in-app shopping fun and friction-free for consumers — and many brands and shoppers are keen to get on board. In fact, approximately 58% of users in the U.S. have purchased a product after seeing it on social media. Unfortunately, these tools neglect effective identity resolution and fraud prevention, leaving sellers vulnerable to fraudulent purchases. And while buyers have some recourse when a purchase turns out to be a scam, it's wise to be cautious while shopping on social media platforms by researching sellers, only using credit cards and being cognizant of common scams, like when vendors on Facebook Marketplace ask for payment upfront. Employer text fraud Fraudulent text messages — also known as “smishing,” a mash-up of Short Messaging Service (SMS) and phishing — continues to rise. In fact, according to data security company Lookout, 2022 was the biggest year ever for such mobile phishing attacks, with more than 30 percent of personal and enterprise mobile phone users exposed every quarter. One modern example of these types of schemes? Expect to continue to see a rise in gift card fraud targeting companies. For example, an employee might receive a text from their "boss" asking them to purchase gift cards and relay the numbers. The fraudsters get to shop, and the company is left with the bill. Why fraud prevention and detection solutions matter Nearly two-thirds of consumers say they are "very" or "somewhat concerned" with online security, and more than 85 percent expect businesses to respond to their identity and fraud concerns. Addressing and preventing fraud — and communicating these fraud-prevention actions to customers — is an essential strategy for businesses that want to maintain customer trust, thereby decreasing churn and maximizing conversions on new leads. There's a financial imperative to address fraud as well. Businesses stand to lose a great deal of money without adequate fraud prevention strategies. Account takeover fraud, for example, is an increasing threat to financial institutions, which saw a 90 percent increase in account takeover losses from 2020 to 2021. By making account takeover fraud prevention a priority, financial institutions can alleviate risks and prevent major losses. How to build an effective fraud strategy in 2024 In 2024, fraud management solutions must be even more technically advanced than the fraudulent techniques they're combating. But more than that, they need to be appealing to consumers, who are likely to abandon signup or purchase attempts when they become too onerous. In fact, 37% of consumers have moved their business elsewhere due to a negative account opening experience. Worryingly for businesses, this number was even higher among high-income households and those aged 25 to 39. To succeed, effective fraud strategies must be seamless, low friction, data-driven and customer-focused. That means making use of up-to-date technologies that boost security while prioritizing a positive customer experience. Concerned about fraud? Let Experian help As we look back at the top fraud trends of 2023, it's clear that scammers are becoming increasingly sophisticated in their methods. Fraud can create huge risks for your business — but there are ways to act. Experian's suite of fraud prevention and identity verification tools can help you detect and combat fraud. Find out more about Experian's fraud risk management strategies and how they can help keep you and your customers safe. Learn more

In financial crime, fraudsters are always looking for new avenues to exploit. The mortgage industry has traditionally been a primary target for fraudsters. But with the 30-year fixed-mortgage rate average above 7.19% for the month of September, it has caused an inherent slowdown in the volume of home purchases. As a result, criminals are turning to other lucrative opportunities in mortgage transactions. They have evolved their techniques to capitalize on unsuspecting homeowners and lenders by shifting their focus from home purchases to Home Equity Line of Credit (HELOC), as they see it as a more compelling option. Understanding mortgage fraud Mortgage fraud occurs when individuals or groups intentionally misrepresent information during the mortgage application process for personal gain. The most common forms of mortgage fraud include income misrepresentation, false identity, property flipping schemes, and inflated property appraisals. Over the years, financial institutions and regulatory bodies have implemented robust measures to combat such fraudulent activities. As the mortgage industry adapts to counter established forms of fraud, perpetrators are constantly seeking new opportunities to circumvent detection. This has led to a shift in fraud trends, with fraudsters turning their focus to alternative aspects of the mortgage market. One area that has captured recent attention is HELOC fraud, also known as home equity loan fraud. HELOC fraud: An attractive target for fraudsters What is a HELOC? HELOCs are financial products that allow homeowners to borrow against the equity in their homes, often providing flexible access to funds. While HELOCs can be a valuable financial tool for homeowners, they also present an attractive opportunity for fraudsters due to their unique characteristics. HELOC fraud schemes An example of a home equity loan fraud scheme is a fraudster misrepresenting himself to deceive a credit union call center employee into changing a member’s address and phone number. Three days later, the fraudster calls back to reset the member’s online banking password, allowing the fraudster to login to the member’s account. Once logged in, the fraudster orders share drafts to be delivered to the new address they now control. The fraudster then forges three share drafts totaling $309,000 and funds them through unauthorized advances against the member’s HELOC through online banking platforms. Why HELOCs are becoming the next target for mortgage fraud Rising popularity: HELOCs have gained significant popularity in recent years, enticing fraudsters seeking out opportunities with larger potential payouts. Vulnerabilities in verification: The verification process for HELOCs might be less rigorous than traditional mortgages. Fraudsters could exploit these vulnerabilities to manipulate property valuations, income statements, or other critical information. Lack of awareness: Unlike conventional mortgages, there may be a lack of awareness among homeowners and lenders regarding the specific risks associated with HELOCs. This knowledge gap can make it easier for fraudsters to perpetrate their schemes undetected. Home equity loans do not have the same arduous process that traditional first mortgages do. These loans do not require title insurance, have less arduous underwriting processes, and do not always require the applicant to be physically present at a closing table to gain access to cash. The result is that those looking to defraud banks can apply for multiple HELOC loans simultaneously while escaping detection. Prevention and safeguards There are several preventive measures and fraud prevention solutions that can be established to help mitigate the risks associated with HELOCs. These include: Education and awareness: Homeowners and lenders must stay informed about the evolving landscape of mortgage fraud, including the specific risks posed by HELOCs. Awareness campaigns and educational materials can play a significant role in spreading knowledge and promoting caution. Enhanced verification protocols: Lenders should implement advanced verification processes and leverage data analytics and modeling thorough property appraisals, income verification, and rigorous background checks. Proper due diligence can significantly reduce the chances of falling victim to HELOC-related fraud. Collaboration and information sharing: Collaboration between financial institutions, regulators, and law enforcement agencies is essential to combat mortgage fraud effectively. Sharing information, best practices, and intelligence can help identify emerging fraud trends and deploy appropriate countermeasures. Acting with the right solution Mortgage fraud is a constant threat that demands ongoing vigilance and adaptability. As fraudsters evolve their tactics, the mortgage industry must stay one step ahead to safeguard homeowners and lenders alike. With concerns over HELOC-related fraud rising, it is vital to raise awareness, strengthen preventive measures, and foster collaboration to protect the integrity of the mortgage market. By staying informed and implementing robust safeguards, we can collectively combat and prevent mortgage fraud from disrupting the financial security of individuals and the industry. Experian mortgage is powering advanced capabilities across the mortgage lifecycle by gaining market intelligence, enhancing customer experience to remove friction and tapping into industry leading data sources to gain a complete view of borrower behavior. To learn more about our HELOC fraud prevention solutions, visit us online or request a call. *This article leverages/includes content created by an AI language model and is intended to provide general information.

"Grandma, it’s me, Mike.” Imagine hearing the voice of a loved one (or what sounds like it) informing you they were arrested and in need of bail money. Panicked, a desperate family member may follow instructions to withdraw a large sum of money to provide to a courier. Suspicious, they even make a video call to which they see a blurry image on the other end, but the same voice. When the fight or flight feeling settles, reality hits. Sadly, this is not the scenario of an upcoming Netflix movie. This is fraud – an example of a new grandparent scam/family emergency scam happening at scale across the U.S. While generative AI is driving efficiencies, personalization and improvements in multiple areas, it’s also a technology being adopted by fraudsters. Generative AI can be used to create highly personalized and convincing messages that are tailored to a specific victim. By analyzing publicly available social media profiles and other personal information, scammers can use generative AI to create fake accounts, emails, or phone calls that mimic the voice and mannerisms of a grandchild or family member in distress. The use of this technology can make it particularly difficult to distinguish between real and fake communication, leading to increased vulnerability and susceptibility to fraud. Furthermore, generative AI can also be used to create deepfake videos or audio recordings that show the supposed family member in distress or reinforce the scammer's story. These deepfakes can be incredibly realistic, making it even harder for victims to identify fraudulent activity. What is Generative AI? Generative artificial intelligence (GenAI) describes algorithms that can be used to create new content, including audio, code, images, text, simulations, and videos. Generative AI has the potential to revolutionize many industries by creating new and innovative content, but it also presents a significant risk for financial institutions. Cyber attackers can use generative AI to produce sophisticated malware, phishing schemes, and other fraudulent activities that can cause data breaches, financial losses, and reputational damage. This poses a challenge for financial organizations, as human error remains one of the weakest links in cybersecurity. Fraudsters capitalizing on emotions such as fear, stress, desperation, or inattention can make it difficult to protect against malicious content generated by generative AI, which could be used as a tactic to defraud financial institutions. Four types of Generative AI used for Fraud: Fraud automation at scale Fraudulent activities often involve multiple steps which can be complex and time-consuming. However, GenAI may enable fraudsters to automate each of these steps, thereby establishing a comprehensive framework for fraudulent attacks. The modus operandi of GenAI involves the generation of scripts or code that facilitates the creation of programs capable of autonomously pilfering personal data and breaching accounts. Previously, the development of such codes and programs necessitated the expertise of seasoned programmers, with each stage of the process requiring separate and fragmented development. Nevertheless, with the advent of GenAI, any fraudster can now access an all-encompassing program without the need for specialized knowledge, amplifying the inherent danger it poses. It can be used to accelerate fraudsters techniques such as credential stuffing, card testing and brute force attacks. Text content generation In the past, one could often rely on spotting typos or errors as a means of detecting such fraudulent schemes. However, the emergence of GenAI has introduced a new challenge, as it generates impeccably written scripts that possess an uncanny authenticity, rendering the identification of deceit activities considerably more difficult. But now, GenAI can produce realistic text that sounds as if it were from a familiar person, organization, or business by simply feeding GenAI prompts or content to replicate. Furthermore, the utilization of innovative Language Learning Model (LLM) tools enables scammers to engage in text-based conversations with multiple victims, skillfully manipulating them into carrying out actions that ultimately serve the perpetrators' interests. Image and video manipulation In a matter of seconds, fraudsters, regardless of their level of expertise, are now capable of producing highly authentic videos or images powered by GenAI. This innovative technology leverages deep learning techniques, using vast amounts of collected datasets to train artificial intelligence models. Once these models are trained, they possess the ability to generate visuals that closely resemble the desired target. By seamlessly blending or superimposing these generated images onto specific frames, the original content can be replaced with manipulated visuals. Furthermore, the utilization of AI text-to-image generators, powered by artificial neural networks, allows fraudsters to input prompts in the form of words. These prompts are then processed by the system, resulting in the generation of corresponding images, further enhancing the deceptive capabilities at their disposal. Human voice generation The emergence of AI-generated voices that mimic real people has created new vulnerabilities in voice verification systems. Firms that rely heavily on these systems, such as investment firms, must take extra precautions to ensure the security of their clients' assets. Criminals can also use AI chatbots to build relationships with victims and exploit their emotions to convince them to invest money or share personal information. Pig butchering scams and romance scams are examples of these types of frauds where AI chatbots can be highly effective, as they are friendly, convincing, and can easily follow a script. In particular, synthetic identity fraud has become an increasingly common tactic among cybercriminals. By creating fake personas with plausible social profiles, hackers can avoid detection while conducting financial crimes. It is essential for organizations to remain vigilant and verify the identities of any new contacts or suppliers before engaging with them. Failure to do so could result in significant monetary loss and reputational damage. Leverage AI to fight bad actors In today's digital landscape, businesses face increased fraud risks from advanced chatbots and generative technology. To combat this, businesses must use the same weapons than criminals, and train AI-based tools to detect and prevent fraudulent activities. Fraud prediction: Generative AI can analyze historical data to predict future fraudulent activities. By analyzing patterns in data and identifying potential risk factors, generative AI can help fraud examiners anticipate and prevent fraudulent behavior. Machine learning algorithms can analyze patterns in data to identify suspicious behavior and flag it for further investigation. Fraud Investigation: In addition to preventing fraud, generative AI can assist fraud examiners in investigating suspicious activities by generating scenarios and identifying potential suspects. By analyzing email communications and social media activity, generative AI can uncover hidden connections between suspects and identify potential fraudsters. To confirm the authenticity of users, financial institutions should adopt sophisticated identity verification methods that include liveness detection algorithms and document-centric identity proofing, and predictive analytics models. These measures can help prevent bots from infiltrating their systems and spreading disinformation, while also protecting against scams and cyberattacks. In conclusion, financial institutions must stay vigilant and deploy new tools and technologies to protect against the evolving threat landscape. By adopting advanced identity verification solutions, organizations can safeguard themselves and their customers from potential risks. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call
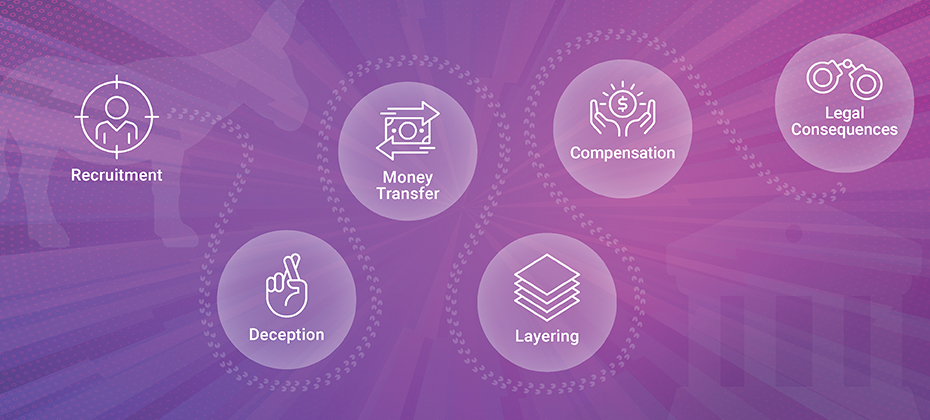
Money mule fraud is a type of financial scam in which criminals exploit individuals, known as money mules, to transfer stolen money or the proceeds of illegal activities. Money mule accounts are becoming increasingly difficult to distinguish from legitimate customers, especially as criminals find new ways to develop hard-to-detect synthetic identities. How money mule fraud typically works: Recruitment: Fraudsters seek out potential money mules through various means, such as online job ads, social media, or email/messaging apps. They will often pose as legitimate employers offering job opportunities promising compensation or claiming to represent charitable organizations. Deception: Once a potential money mule is identified, the fraudsters use persuasive tactics to gain their trust. They may provide seemingly legitimate explanations like claiming the money is for investment purposes, charity donations or for facilitating business transactions. Money Transfer: The mule is instructed to receive funds to their bank or other financial account. The funds are typically transferred from other compromised bank accounts obtained through phishing or hacking. The mule is then instructed to transfer the money to another account, sometimes located overseas. Layering: To mask the origin of funds and make them difficult to trace, fraudsters will employ layering techniques. They may ask the mule to split funds into smaller amounts, make multiple transfers to different accounts, or use various financial platforms such as money services or crypto. Compensation: The money mule is often promised a percentage of transferred funds as payment. However, the promised monies are lower than the dollars transferred, or sometimes the mule receives no payment at all. Legal consequences: Regardless whether mules know they are supporting a criminal enterprise or are unaware, they can face criminal charges. In addition, their personal information could be compromised leading to identity theft and financial loss. How can banks get ahead of the money mule curve: Know your beneficiaries Monitor inbound paymentsEngage identity verification solutionsCreate a “Mule Persona” behavior profileBeware that fraudsters will coach the mule, therefore confirmation of payee is no longer a detection solution Educate your customers to be wary of job offers that seem too good to be true and remain vigilant of requests to receive and transfer money, particularly from unknown individuals and organizations. How financial institutions can mitigate money mule fraud risk When new accounts are opened, a financial institution usually doesn’t have enough information to establish patterns of behavior with newly registered users and devices the way they can with existing users. However, an anti-fraud system should catch a known behavior profile that has been previously identified as malicious. In this situation, the best practice is to compare the new account holder’s behavior against a representative pool of customers, which will analyze things like: Spending behavior compared to the averagePayee profileSequence of actionsNavigation data related to machine-like or bot behaviorAbnormal or risky locationsThe account owner's relations to other users The risk engine needs to be able to collect and score data across all digital channels to allow the financial institution to detect all possible relationships to users, IP addresses and devices that have proven fraud behavior. This includes information about the user, account, location, device, session and payee, among others. If the system notices any unusual changes in the account holder’s personal information, the decision engine will flag it for review. It can then be actively monitored and investigated, if necessary. The benefits of machine learning This is a type of artificial intelligence (AI) that can analyze vast amounts of disparate data across digital channels in real time. Anti-fraud systems based on AI analytics and predictive analytics models have the ability to aggregate and analyze data on multiple levels. This allows a financial institution to instantly detect all possible relationships across users, devices, transactions and channels to more accurately identify fraudulent activity. When suspicious behavior is flagged via a high risk score, the risk engine can then drive a dynamic workflow change to step up security or drive a manual review process. It can then be actively monitored by the fraud prevention team and escalated for investigation. How Experian can help Experian’s fraud prevention solutions incorporate technology, identity-authentication tools and the combination of machine learning analytics with Experian’s proprietary and partner data to return optimal decisions to protect your customers and your business. To learn more about how Experian can help you leverage fraud prevention solutions, visit us online or request a call

There’s an undeniable link between economic and fraud trends. During times of economic stress, fraudsters engage in activities specifically designed to target strained consumers and businesses. By layering risk management and fraud prevention tools, your organization can manage focus on growing safely. Download infographic Review your fraud strategy

With fraud expected to surge amid uncertain economic conditions, fraudsters are preparing new deception techniques to outsmart businesses and deceive consumers. To help businesses prepare for the coming fraud threats, we created the 2023 Future of Fraud Forecast. Here are the fraud trends we expect to see over the coming year: Fake texts from the boss: Given the prevalence of remote work, there’ll be a sharp rise in employer text fraud where the “boss” texts the employee to buy gift cards, then asks the employee to email the gift card numbers and codes. Beware of fake job postings and mule schemes: With changing economic conditions, fraudsters will create fake remote job postings, specifically designed to lure consumers into applying for the job and providing private details like a social security number or date of birth on a fake employment application. Frankenstein shoppers spell trouble for retailers: Fraudsters can create online shopper profiles using synthetic identities so that the fake shopper’s legitimacy is created to outsmart retailers’ fraud controls. Social media shopping fraud: Social commerce currently has very few identity verification and fraud detection controls in place, making the retailers that sell on these platforms easy targets for fraudulent purchases. Peer-to-peer payment problems: Fraudsters love peer-to-peer payment methods because they’re an instantaneous and irreversible way to move money, enabling fraudsters to get cash with less work and more profit “As fraudsters become more sophisticated and opportunistic, businesses need to proactively integrate the latest technology, data and advanced analytics to mitigate the growing fraud risk,” said Kathleen Peters, Chief Innovation Officer at Experian Decision Analytics in North America. “Experian is committed to continually innovating and bringing solutions to market that help protect consumers and enable businesses to detect and prevent current and future fraud.” To learn more about how to protect your business and customers from rising fraud trends, download the Future of Fraud Forecast and check out Experian’s fraud prevention solutions. Future of Fraud Forecast Press Release

Written by: Mihail Blagoev As there is talk about the global economy potentially heading into a recession, while some suggest that it has already started, there is an expectation that many of the world's countries will see their economic output decline in the next couple of months or a year. Among the negative trends that can occur during a recession are companies making fewer sales and people losing their jobs. Unfortunately, just like any other economic crisis, fraud is expected to go in the opposite direction as criminals continue finding innovative ways to attack consumers when they’re most vulnerable. There is also a concern that first-party fraud attempts might rise as genuine consumers are pushed over the edge by inflation and economic uncertainty. With that in mind, here are six fraud trends that are likely to happen during a recession: Fraudsters exploiting the vulnerable It is well-documented that fraudsters found numerous ways to exploit the vulnerable during the pandemic. Unfortunately, this is expected to happen again in the coming months. As the cost of living rises, criminals will try to use that in their favor by looking for people who can't pay their utility bills or can't afford the price of gas or even food. Fraudsters will try to exploit that by offering them deals, discounts, refunds, or just about anything that will make people believe they are paying less for something that has increased in value or is out of reach at its normal price. Fraudsters have two main goals behind these tactics – stealing personal information to use in other crimes or gaining immediate financial benefits. Although their tactics are well-known – applying pressure on their victims to make quick decisions or offering them something that sounds like a great deal, but in truth, it isn't – that won't prevent them from trying. These scams show that, unlike in other industries, criminals do not rely on high success rates to achieve their goals. All they need is one or two victims out of every few hundred to fall for their schemes. Loan origination fraud Periods of financial instability often result in an increase in first-party fraud, among others. This could take many forms, and there is a possibility for an increase in fraudulent loan applications by genuine consumers to be among the most popular ones. In this type of fraud, bad actors lie on registration forms or applications to gain access to funds they wouldn't normally receive if they added their real information. That could be done by lying about their income and employment information, usually inflating their salaries, extending the amount of time they worked for a certain company, or simply adding a company they have never worked for. Other popular forgeries include anything from supplying fake phone numbers and addresses to providing fake bank statements and utility bills. Money mules Recessions can result in layoffs or people looking for work not being able to find any. That's another opportunity for fraudsters to exploit the vulnerable by offering them “jobs.” This could be achieved by posting job ads on real employment websites or social media. Once recruited, people are asked to open new bank accounts or use their previously opened accounts to transfer funds to accounts that are in the possession of criminals. In the end, the funds get laundered, while the genuine account holder receives a fee for the service. People of all ages are a possible target, but this is especially true for younger generations who often don't understand the consequences of their activities. Friendly fraud Another type of first-party fraud that could go up as a result of the increased economic pressures could be friendly fraud. In this type of fraud that mostly affects the retail industry, consumers charge back genuine payments made by them in order to end up with both the product purchased and the funds for it back in their possession. They could then keep the product or quickly resell it for less than its original value. Luxury goods and electronics could be especially attractive for this type of fraud. Claiming non-deliveries or transactions not being recognized could be among the top reasons used for charging back the transactions. Investment fraud During times of economic hardship, people are often looking for ways to keep their savings from getting eaten by inflation. Investments in property could be one solution, but as it is not affordable for everyone, people are also looking for other ways to invest their money. While this isn’t exactly a vulnerability, it is something that criminals are looking to exploit greatly. They usually reach out to potential victims through social media while also presenting them with fake websites that mimic those by real investors. The opportunities being offered can range from cryptocurrency to various schemes and products that don’t exist or are worthless. However, after the criminals obtain possession of the funds, they discontinue their contact with the victims. Fake goods While this shouldn't happen to the same extent that was seen in 2020, there is a chance that some goods might disappear from certain markets. There could be a variety of reasons for that, from companies limiting their production or going out of business due to inability to pay their bills or shortage in sales to issues with supply chains due to the high gas and oil prices. Expect fraudsters to be the first to move in if there are shortages and start offering fake products or goods that will never arrive. It is still difficult to measure if or when a recession will hit each corner of the world or how long it will take for the next phase in the financial cycle to begin. However, one thing that is certain is that the longer it takes the economy to settle, the more opportunities criminals will have to benefit from their schemes and come up with new ways to defraud people. Businesses should monitor the fraud environment around them closely and be ready to adjust their fraud management strategies quickly. They should also understand the complexity of the problems in front of them and that they will likely need a mixture of capabilities to sort them out while keeping their customer base happy. This is where fraud orchestration platforms could help by offering the needed solutions to solve multiple fraud issues and the flexibility to turn any of these tools on and off when needed. Contact us
The ongoing COVID-19 pandemic has facilitated an increase in information collection among consumers and organizations, creating a prosperous climate for cybercriminals. As businesses and customers adjust to the “new normal,” hackers are honing in on their targets and finding new, more sophisticated ways to access their sensitive data. As part of our recently launched Q&A perspective series, Michael Bruemmer, Experian’s Vice President of Data Breach Resolution and Consumer Protection, provided insight on emerging fraud schemes related to the COVID-19 vaccines and how increased use of digital home technologies could lead to an upsurge in identity theft and ransomware attacks. Check out what he had to say: Q: How did Experian determine the top data breach trends for 2021? MB: As part of our initiative to help organizations prevent data breaches and protect their information, we release an annual Data Breach Forecast. Prior to the launch of the report, we analyze market and consumer trends. We then come up with a list of potential predictions based off the current climate and opportunities for data breaches that may arise in the coming year. Closer to publication, we pick the top five ‘trends’ and craft our supporting rationale. Q: When it comes to data, what is the most immediate threat to organizations today? MB: Most data breaches that we service have a root cause in employee errors – and working remotely intensifies this issue. Often, it’s through negligence; clicking on a phishing link, reusing a common password for multiple accounts, not using two-factor authentication, etc. Organizations must continue to educate their employees to be more aware of the dangers of an internal breach and the steps they can take to prevent it. Q: How should an organization begin to put together a comprehensive threat and response review? MB: Organizations that excel in cybersecurity often are backed by executives that make comprehensive threats and response reviews a top corporate priority. When the rest of the organization sees higher-ups emphasizing the importance of fraud prevention, it’s easier to invest time and money in threat assessments and data breach preparedness. Q: What fraud schemes should consumers be looking out for? MB: The two top fraud schemes that consumers should be wary of are scams related to the COVID-19 vaccine rollout and home devices being held for ransom. Fraudsters have been leveraging social media to spread harmful false rumors and misinformation about the vaccines, their effectiveness and the distribution process. These mistruths can bring harm to supply chains and delay government response efforts. And while ransomware attacks aren’t new, they are getting smarter and easier with people working, going to school and hosting gatherings entirely on their connected devices. With control over home devices, doors, windows, and security systems, cybercriminals have the potential to hold an entire house hostage in exchange for money or information. For more insight on how to safeguard your organization and consumers from emerging fraud threats, watch our Experian Symposium Series event on-demand and download our 2021 Data Breach Industry Forecast. Watch now Access forecast About Our Expert: Michael Bruemmer, Experian VP of Data Breach Resolution and Consumer Protection, North America Michael manages Experian’s dedicated Data Breach Resolution and Consumer Protection group, which aims to help businesses better prepare for a data breach and mitigate associated consumer risks following breach incidents. With over 25 years in the industry, he has guided organizations of all sizes and sectors through pre-breach response planning and delivery.

It’s obvious that 2020 was a year of unprecedented change and created brand new opportunities for fraud. In 2021, fraudsters will continue to iterate on new and old methods of attack, requiring businesses to remain flexible and proactive to prevent losses. We created the 2021 Future of Fraud Forecast to help businesses anticipate new types of fraud and prepare and protect consumers on the road ahead. Here are the trends we expect to see over the coming year: Putting a Face to Frankenstein IDs: Synthetic identity fraud will start to rely on “Frankenstein faces” for biometric verification. “Too Good to Be True” COVID Solutions: The promise of at-home test kits, vaccines and treatments will be used as means for sophisticated phishing and social engineering schemes. Stimulus Fraud Activity, Round Two: Fraudsters will take advantage of additional stimulus funding by using stolen data to intercept payments. Say ‘Hello’ to Constant Automated Attacks: Once the stimulus fraud attacks run their course, hackers will increasingly turn to automated methods. Survival of the Fittest for Small Businesses: In 2021, businesses with lackluster fraud prevention tools will suffer large financial losses. To learn more about how to protect your business and customers, download the Future of Fraud Forecast and check out Experian’s fraud prevention solutions. Future of Fraud Forecast Request a call

Every few months we hear in the news about a fraud ring that has been busted here in the U.S. or in another part of the world. In May, I read about a fraud ring based in Georgia and Louisiana that bought 13,000 stolen identities of children who were on the Louisiana Medicaid program and billed the government for services not rendered. This group defrauded the Medicaid program of more than $500,000. This is just one of many stories that we hear about fraud rings, and given the rapidly changing economic environment, now is the time for businesses to think about how to protect against fraud rings. There are a number of challenges that organizations may have when it comes to sharing trends and collaborations, understanding the ways to tie fraud rings together, creating treatments for identifying fraud rings and ways to store and catalogue fraud ring experiences so they can be easily recognized. The trouble with identifying fraud rings It’s important to understand the challenges that organizations have because they see the fraud rings through their own internal lens. Here are a few of the top things businesses should work on: Think like a fraudster. This will help businesses become more creative in their approach to fraud prevention. Facilitate internal collaboration. Share with in-organization partners. Sometimes this can be difficult due to organizational structure. Promote external collaboration. Intel-sharing groups are a great way for businesses to network within their industries and learn about the fraud that others are seeing. An organization that I’ve worked with in the past is the National Cyber Forensic and Training Alliance (NCFTA). Putting the pieces together How do businesses identify a fraud ring? There are three steps to get started. The first is reviewing and understanding the data. Fraudsters are lazy and want to replicate the process over and over again, and because of this there is always some piece of information that is repeated. It could be a name, an email address, device fingerprint, or similar. The second step is tying the fraud ring together. This is done by creating rules to help identify the trends. Having rules in place to identify fraud rings allows businesses to easily pull stats together for their leadership. Lastly, applying an acronym or name to the particular fraud ring and adding comments to the cases associated with a particular ring will help with post-investigation analysis. Learning from the past Before I became a consultant, I remember identifying a fraud ring that was submitting events with the same language pack and where the device fingerprint was staying consistent. Those events were being referred out for review and marked with the same note. At a post-mortem review, I was able to talk to the fraud ring we had seen, and it was easy to pull all events associated with this fraud ring because my team had marked the events with the same comments. Another fraud ring example happened a few years ago. A client called me and said that they were under a fraud attack and this fraud ring was rotating the email handle. I reviewed the data and came up with a rule to catch this activity. Fraud rings will use email handle rotation to help them keep track of accounts that are opened or what emails they used in the past. By coupling the email handle rotation with an email verification service like Emailage, this insight could be very telling. I would assume that when fraud rings use email handle rotation these emails are new and have just been created. These are just a few of the many fraud rings that I’ve encountered over the course of my career and I’m sure there will be a lot more in the years to come. The best advice I can give to anyone that reads this post is to understand the data that you are reviewing, look for anomalies within the data, ask questions and test your theories by running queries on the data that you’re reviewing. I would love to hear about the different fraud rings that you’ve encountered over your career. Stay safe. Contact us

Update: After closely monitoring updates from the WHO, CDC, and other relevant sources related to COVID-19, we have decided to cancel our 2020 Vision Conference. If you had the chance to experience tomorrow, today, would you take it? What if it meant you could get a glimpse into the future technology and trends that would take your organization to the next level? If you’re looking for a competitive edge – this is it. For more than 38 years, Experian’s premier conference has connected business leaders to data-driven ideas and solutions, fueling them to target new markets, grow existing customer bases, improve response rates, reduce fraud and increase profits. What’s in it for you? Everything to gain and nothing to lose. Are you a marketer? These sessions were made to drive your conversion rates to new heights: Know your customers via omnichannel marketing: Your customers are everywhere, but can you reach them? Learn how to drive business-expansion strategy, brand affinity and customer engagement across multiple channels. Plus, gain insight into connecting with customers via one-to-one messaging. By invitation only, the future of ITA marketing: An evolving landscape means marketers face new challenges in effectively targeting consumers while staying compliant. In this session, we’ll explore how you can leverage fair lending-friendly marketing data for targeting, analysis and measurement. Want the latest in technology trends? Dive into discussions to transform your customer experience: Credit in the age of technology transformation: Machine learning and artificial intelligence are the current darlings of big data, but the platform that drives the success of any big data endeavor is crucial. This session will dive into what happens behind the curtain. Put away your plastic – next-generation identity: An industry panel of experts discusses the newest digital identity and authentication capabilities – those in use today and also exciting solutions on the horizon. How about for the self-proclaimed data geeks? Analyze these: Alternative data: Listen in on an in-depth conversation about creative and impactful examples of using emerging data assets, such as alternative and consumer-permissioned data, for improved consumer inclusion, risk assessment and verification services. The next wave in open data: Experian will share their views on the potential of advanced data and models and how they benefit the global value chain – from consumer scores to business opportunities – regardless of local regulations. And the risk masters? Join us as we kick fraud to the curb: Understanding and tackling synthetic ID fraud: Synthetic IDs present a serious challenge for our entire industry. This expert panel will explore the current landscape – what’s working and what’s not, the expected impact of the next generation SSA eCBSV service, and best practice prevention methods. You are your ID – the new reality of biometrics: Consumers are becoming increasingly comfortable with biometrics. Just as CLEAR has transformed how we use our biometric identity to move through airports, sports venues and more, financial transactions can also be made friction-free. The point is, there’s something for everyone at Vision 2020. It’s not just another conference. Trade in stuffy tradeshow halls and another tri-fold brochure for the insights and connections you need to take your career and organization to the next level. Like technology itself, Vision 2020 promises to connect us, unify us and enable us all to create a better tomorrow. Join us for unique networking opportunities, one-on-one conversations with subject-matter experts and more than 50 breakout sessions with the industry’s most sought-after thought leaders.

If you’ve seen an uptick in photos of friends and celebrities looking older with wrinkles on your social media feeds, you’re not alone. A new free photo editor has taken the internet by a storm, featuring an AI-powered image-altering application that allows users to see their “future self.” All you have to do is upload a single photo (or few) from your camera roll to be enhanced. While this may seem like harmless fun, the app is now making headlines over increased privacy concerns about what occurs behind the scenes once users submit their selfies. Red flags were raised when multiple alleged negative implications were connected to the app – including the app’s ownership and the potential risk that the app downloaded a user’s entire photo album onto their database. In fact, the privacy concerns also prompted Democratic Party officials to implore federal agencies, including the FBI, “to look into the potential national security and privacy risks the phone app poses to the United States.” Since then, the app’s creators have addressed these concerns, stating most of the photo processing occurs in the cloud and most photos are deleted within 48 hours. Additionally, the only photos uploaded are ones that have been personally submitted by the user. Regardless, a database of user-submitted photos could be seen as a goldmine to fraudsters. In a time where personal and biometric data (including facial recognition) are some of the key ways to validate security, it’s important for consumers to be aware of how and where they’re sharing their data, whether it’s for an age-progression photo app, or their financial accounts. Consumers, businesses, financial institutions – everyone – should exhibit caution and take measures to ensure personal information remains secure and is not being used for nefarious reasons. While consumers may be aware that businesses are collecting data, companies should take steps to form digital trust with transparency. This could be achieved by: Educating consumers on how their data is being used Effectively communicating privacy policies and service terms more concisely Helping consumers feel in control of their information To learn more about research that indicates a shift to advanced authentication methods (including biometrics), fraud trends and how to combat them, download our e-book. Download Now